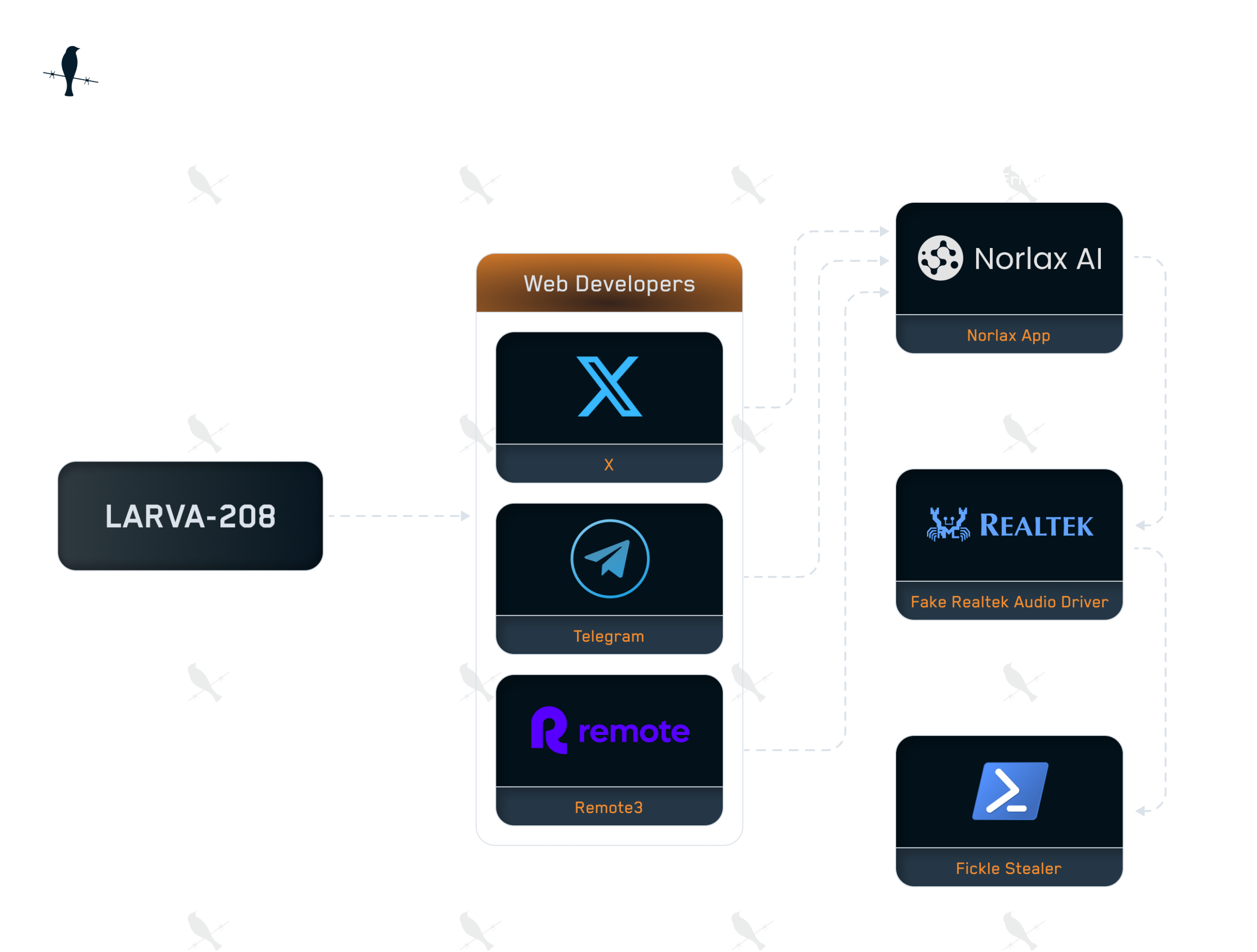
The hacking collective known as EncryptHub—also tracked as LARVA-208 and Water Gamayun—has launched a new wave of attacks specifically targeting developers within the Web3 ecosystem. Their aim: to infect victims with data-stealing malware capable of exfiltrating cryptocurrency wallets and accessing sensitive project environments.
According to researchers from the Swiss cybersecurity firm PRODAFT, the attackers have shifted tactics, now masquerading as AI platforms such as the counterfeit website Norlax AI, which closely mimics the appearance of Teampilot. Through such deceptive fronts, they lure victims with offers of “employment” or “portfolio evaluations,” leading them instead to malicious infrastructure.
Previously known for deploying ransomware, EncryptHub has pivoted toward data theft—a quicker path to monetization. Web3 developers are especially attractive targets: many possess access to crypto wallets, smart contract repositories, and staging environments. Moreover, their freelance status often places them outside corporate security perimeters, rendering both defenses weaker and breaches less noticeable.
The scammers disseminate links to these phony platforms through Telegram and X (formerly Twitter), posing as recruiters or project leads. They sometimes advertise job listings on Remote3, a platform tailored to Web3 talent, and follow up with applicants via direct messages containing links to supposed interview platforms.
To bypass Remote3’s warnings about malware, attackers initiate contact through Google Meet. During the conversation, they prompt the candidate to switch to an external platform—such as Norlax AI—claiming it’s necessary to continue the interview. There, the user is asked to enter an email address and invitation code, only to be shown an error citing a missing audio driver.
Under the guise of resolving the issue, the site prompts the download of a file masquerading as a Realtek HD Audio Driver. In truth, the file is a malicious payload that, via PowerShell, downloads and executes Fickle Stealer—a sophisticated info-stealer that transmits harvested data to a remote server codenamed SilentPrism.
PRODAFT emphasizes that this campaign reflects a strategic evolution—from direct extortion to monetizing stolen credentials, wallets, and sensitive data on underground markets.
Meanwhile, additional threats have emerged. Researchers at Trustwave SpiderLabs have identified a novel ransomware strain dubbed KAWA4096, whose operational style resembles the notorious Akira gang. The ransom note structure imitates that of Qilin, possibly as a means to project credibility within cybercriminal circles. Since June 2025, at least 11 organizations—primarily in the United States and Japan—have fallen victim. The initial access vectors remain unknown.
KAWA4096 distinguishes itself with the ability to encrypt files on network shares. It employs multithreading to expedite scanning and encryption, queueing files and processing them simultaneously across multiple threads—significantly enhancing the speed and efficacy of the attack.
Another emerging threat is Crux, a new ransomware strain that claims affiliation with the BlackByte group. It has been observed in three attacks between July 4 and 13. In one instance, threat actors leveraged legitimate credentials and Remote Desktop Protocol (RDP) for access. Across all incidents, attackers utilized native Windows tools—such as svchost.exe and bcdedit.exe—to conceal malicious commands and tamper with boot settings, complicating recovery efforts.
According to experts at Huntress, Crux relies heavily on legitimate Windows processes, making detection more challenging. However, vigilant monitoring through Endpoint Detection and Response (EDR) solutions can help uncover such activity before it culminates in catastrophic damage.