Earth Hundun’s Waterbear Rampage Targets Asia-Pacific
A recently uncovered cyberattack has impacted the technological, scientific, and governmental sectors across the Asia-Pacific region. The attack has been attributed to the hacker group BlackTech, known for its sophisticated methods of obfuscating its activities.
The attacks involved updated versions of malicious software, including the modular backdoor Waterbear and its advanced iteration, Deuterbear. Researchers from Trend Micro report that Waterbear is particularly challenging to detect and analyze due to its numerous evasion mechanisms. Deuterbear, compared to its predecessor, incorporates enhancements such as countermeasures against memory scanning and data encryption, making it even more dangerous than the original.
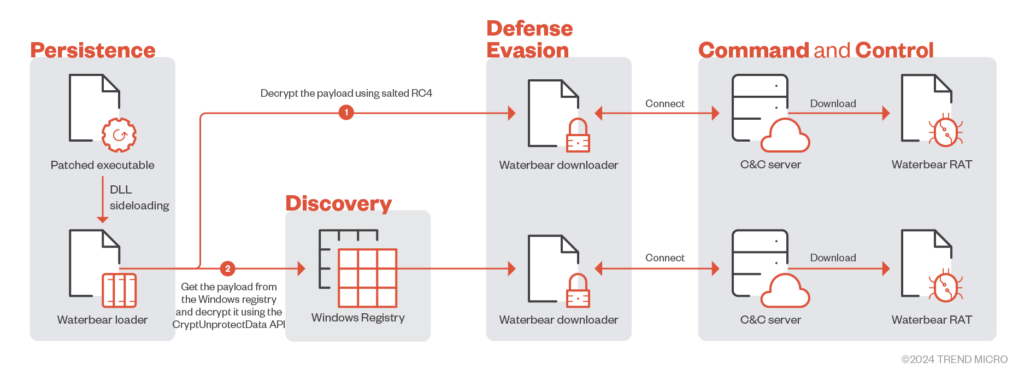
Waterbear infection flow chart
BlackTech, also known under aliases such as Earth Hundun and Circuit Panda, has been actively conducting cyberattacks against targets in various countries since 2007 and continually refines its methods. In September last year, intelligence agencies from Japan and the USA linked the group’s actions to China, highlighting the hackers’ ability to modify router firmware and exploit trust relationships between domains to access corporate networks.
BlackTech’s operations remain concealed thanks to the use of proprietary software and Living off the Land (LotL) tactics, which include disabling logging on routers. The group’s primary tool, the Waterbear malware, has been in use since 2009 and is regularly updated to enhance its stealth capabilities. Introduced in 2022, Deuterbear employs obfuscation methods and HTTPS for communication with its command server and is also frequently updated.
These multifaceted malware programs can execute around 50 commands, including process and file management, modifications to the Windows registry, and the collection of screenshots. The ongoing development of Waterbear and its derivatives since 2009 demonstrates BlackTech’s continuous enhancement of its cyberattack methods.
This relentless advancement of sophisticated cyberattack tactics underscores the growing necessity of strengthening cybersecurity measures to protect vital data and systems from malicious hacker groups employing increasingly refined malware.





