dnstwist
See what sort of trouble users can get in trying to type your domain name. Find lookalike domains that adversaries can use to attack you. Can detect typosquatters, phishing attacks, fraud, and brand impersonation. Useful as an additional source of targeted threat intelligence.
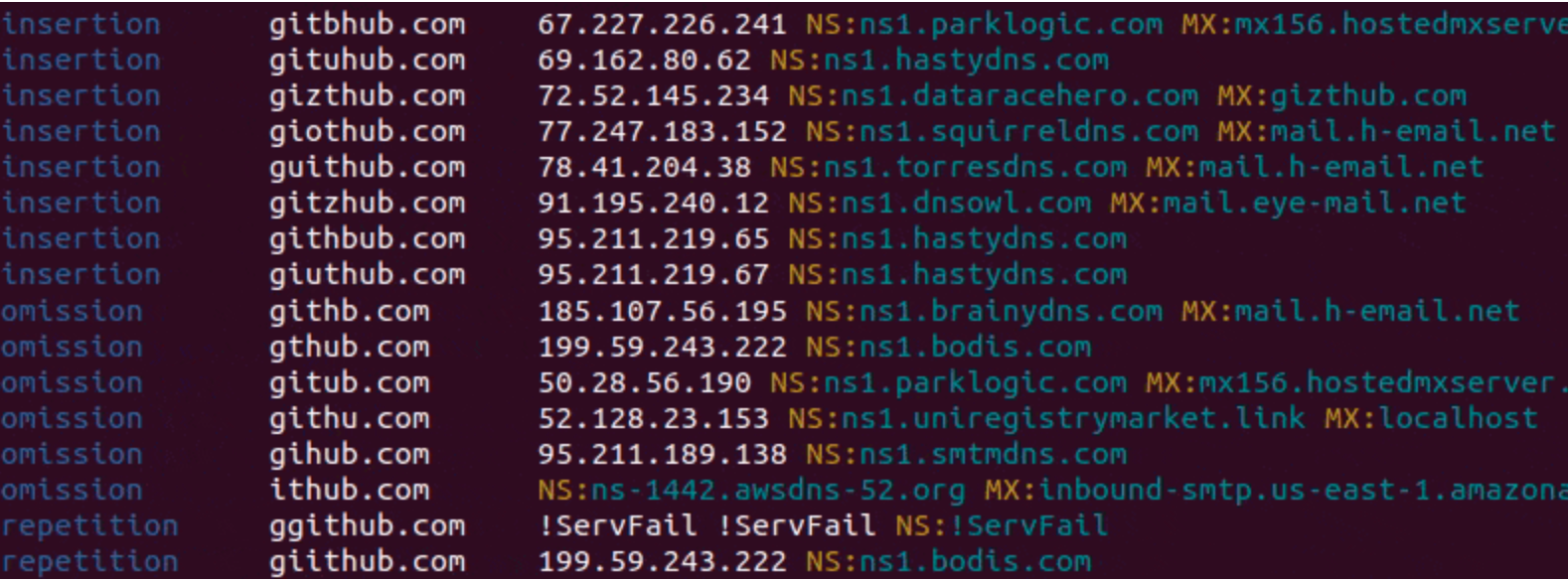
DNS fuzzing is an automated workflow that aims to uncover potentially malicious domains that target your organization. This tool generates a comprehensive list of permutations based on a provided domain name, and subsequently verifies whether any of these permutations are in use. Additionally, it can generate fuzzy hashes of web pages to detect ongoing phishing attacks or brand impersonation, and much more!
Feature
- Variety of highly effective domain fuzzing algorithms
- Unicode domain names (IDN)
- Additional domain permutations from dictionary files
- Efficient multithreaded task distribution
- Live phishing webpage detection:
- HTML similarity with fuzzy hashes (ssdeep/tlsh)
- Screenshot visual similarity with perceptual hashes (pHash)
- Rogue MX host detection (intercepting misdirected e-mails)
- GeoIP location
- Export to CSV and JSON
Phishing detection
Manually checking each domain name in terms of serving a phishing site might be time-consuming. To address this, dnstwist makes use of so-called fuzzy hashes (locality-sensitive hash, LSH) and perceptual hashes (pHash). Fuzzy hashing is a concept that involves the ability to compare two inputs (HTML code) and determine a fundamental level of similarity, while perceptual hash is a fingerprint derived from visual features of an image (web page screenshot).
Fuzzy hashing
The unique feature of detecting similar HTML source code can be enabled with --lsh argument. For each generated domain, dnstwist will fetch content from responding HTTP server (following possible redirects), normalize HTML code and compare its fuzzy hash with the one for the original (initial) domain. The level of similarity is expressed as a percentage.
In cases when the effective URL is the same as for the original domain, the fuzzy hash is not calculated at all in order to reject false positive indications.
Note: Keep in mind it’s rather unlikely to get 100% match, even for MITM attack frameworks, and that a phishing site can have a completely different HTML source code.
$ dnstwist --lsh domain.name
dnstwist will parse it and apply for each generated domain name variant. Use --lsh-url to override URL to fetch the original web page from.$ dnstwist --lsh https://domain.name/owa/
$ dnstwist --lsh --lsh-url https://different.domain/owa/ domain.name
$ dnstwist --lsh tlsh domain.name
If Chromium browser is installed, dnstwist can utilize its headless mode, which operates without a graphical user interface, to capture web page screenshots, render them, and calculate pHash values. These pHash values are then compared to evaluate the visual similarity, expressed as a percentage.
$ dnstwist --phash domain.name
$ dnstwist --phash --screenshots /tmp/domain domain.name
Proxy support
For all HTTP connections, proxies are automatically used when the presence of environment variables named $<scheme>_proxy, in a case insensitive approach, is detected. If both lowercase and uppercase environment variables exist, lowercase is preferred.