Decade-Old Phishing: Pawn Storm Remains a Global Email Threat
In a recent report by Trend Micro, the cybercriminal group known as Pawn Storm, engaged in hacking operations targeting key global organizations since 2004, is detailed. Despite the seemingly outdated nature of their methods, including phishing campaigns that have spanned over a decade, Pawn Storm continues to successfully breach thousands of email accounts.
Trend Micro reveals that the group has recently shifted its tactics towards attacks using Net-NTLMv2 hashes in an attempt to infiltrate networks of governmental, defense, and military organizations worldwide. Demonstrating activity across Europe, North and South America, Asia, Africa, and the Middle East, the hackers have shown tenacity by altering folder permissions in victims’ mailboxes, facilitating their network traversal.
An example of a username exfiltration routine from Pawn Storm
Since 2019, cybercriminals have frequently employed brute force techniques to crack email servers and corporate VPN services. The group also utilized anonymization methods such as VPN services, Tor networks, compromised EdgeOS routers, and free services like URL shortening. Anonymization extended to phishing emails sent from compromised email accounts via Tor or VPN.
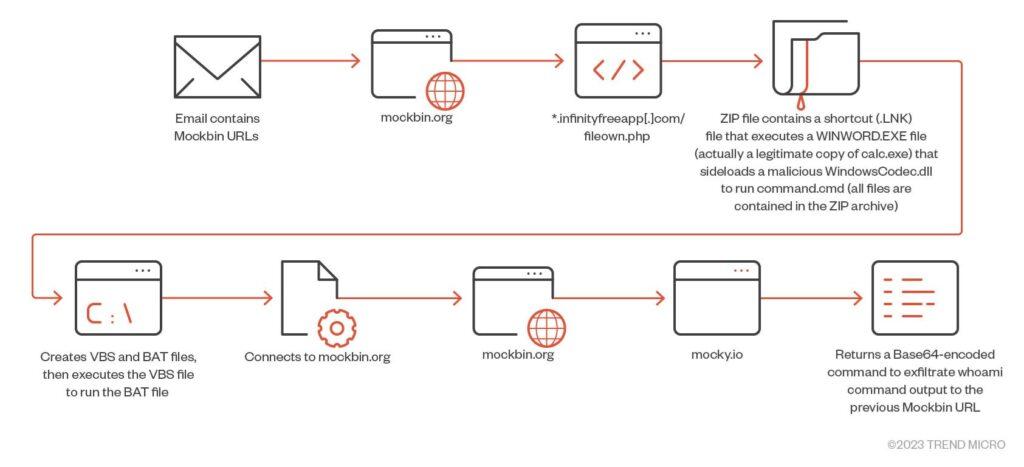
The critical vulnerability CVE-2023-23397 (CVSS score: 9.8), patched in March 2023, allowed Pawn Storm to conduct Relay attacks on Outlook users. Utilizing this flaw, the group sent specialized calendar invitations, initiating a Net-NTLMv2 attack. The campaign persisted until August 2023, becoming increasingly sophisticated with scripts hosted on Mockbin and URLs redirecting to PHP scripts on free web hosting domains.
Pawn Storm also exploited the WinRAR vulnerability CVE-2023-38831 (CVSS score: 7.8) for Relay attacks. In late 2023, the hackers launched a phishing campaign aimed at stealing credentials from European government bodies, using “webhook[.]site” URLs and VPN IP addresses. Beyond Pawn Storm, several other APT groups exploited this flaw, attacking 130 organizations and successfully seizing traders’ funds.
In October 2022, Pawn Storm utilized an info-stealer without connecting to a Command and Control (C2) server. This straightforward yet effective method involved uploading stolen files to a free file-sharing service using shortened URLs for access.
In March 2023, the Microsoft security team identified a critical vulnerability in Microsoft Outlook, tracked under CVE-2023-23397, allowing attackers to steal Net-NTLMv2 hashes and gain access to user accounts. A specially crafted email message poses a particular threat, as opening it transfers the user’s Net-NTLMv2 hash to the attacker.





