Amid escalating tensions between Iran and Israel, cybersecurity experts at Lookout have uncovered a new Android-based spyware known as DCHSpy, which has been linked to Iran’s Ministry of Intelligence and Security (MOIS). This malicious software is distributed under the guise of legitimate VPN services and even exploits the popular Starlink brand—SpaceX’s satellite internet service—as a lure.
Researchers identified four distinct samples of the malware within just one week of the conflict’s outbreak. While the exact number of victims remains unknown, it is clear that the spyware targets individuals for whom anonymity is paramount—dissidents, journalists, and human rights advocates.
DCHSpy was first observed in July 2024. According to the researchers, it is affiliated with the MuddyWater threat group—a cyber espionage unit operating on behalf of the Iranian government. Also known by aliases such as Boggy Serpens, Cobalt Ulster, TA450, Seedworm, and Static Kitten, this group has a history of sophisticated intrusions. The spyware harvests a wide range of sensitive information, including WhatsApp data, contact lists, SMS messages, files, geolocation, call logs, and can even record audio and capture images using the device’s camera.
In its early stages, the malware was disseminated through Telegram channels in both English and Farsi—the official language of Iran—featuring themes that contradicted the regime’s official narrative. Promoting VPN services, the campaign appealed to users seeking to circumvent state-imposed internet restrictions.
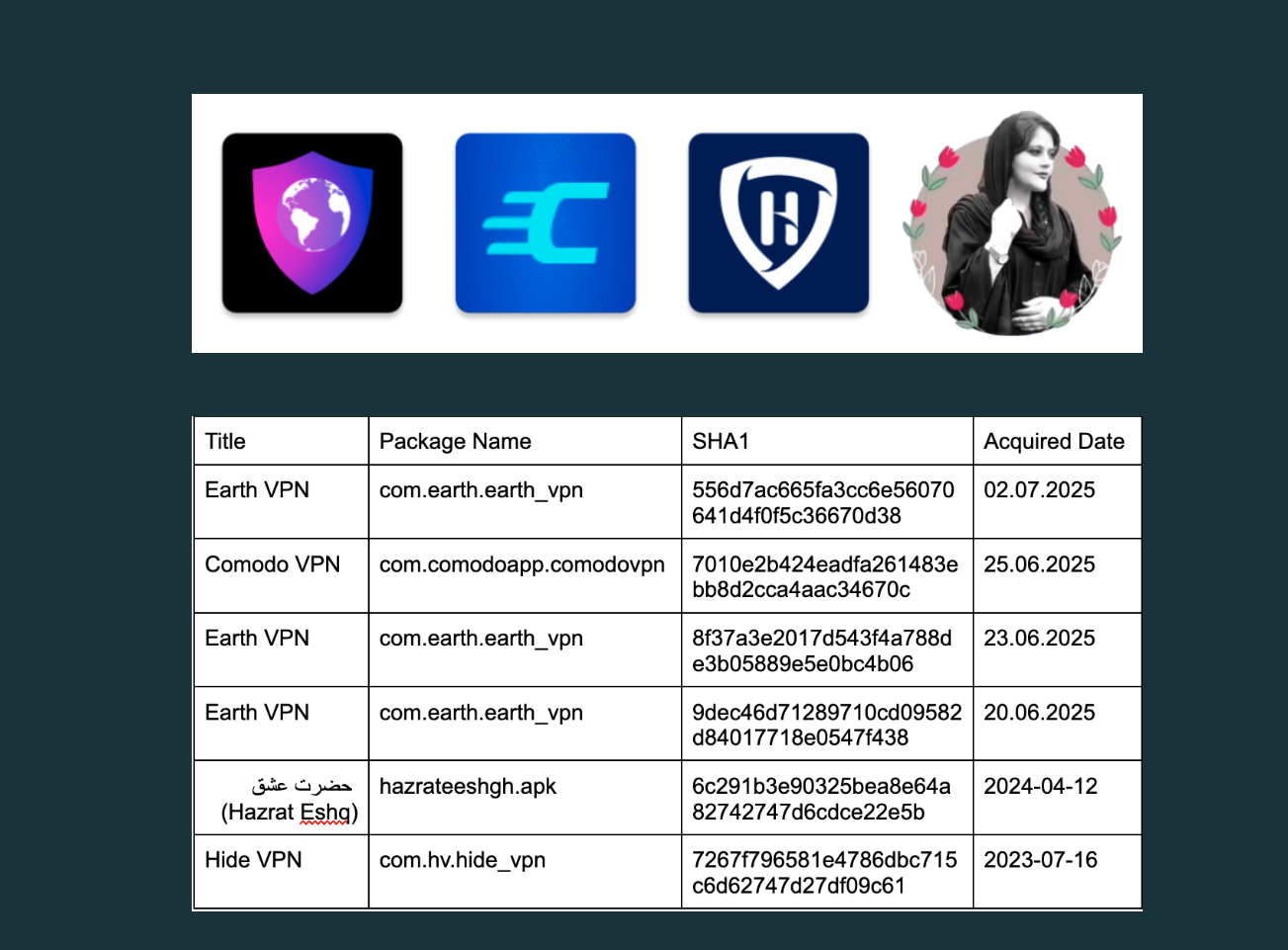
Among the masquerading apps were Earth VPN, Comodo VPN, and Hide VPN. Some APK files bore names such as “starlink_vpn(1.3.0)-3012 (1).apk,” clearly reflecting a calculated effort to capitalize on the public’s interest in Starlink. It’s worth noting that Starlink’s satellite internet became operational in Iran during a period of heightened online censorship. However, just weeks later, the Iranian parliament enacted legislation banning its use.
DCHSpy is a modular trojan capable of conducting precise surveillance on compromised devices. It shares infrastructure with another notorious piece of malware, SandStrike, which similarly spread through fake VPN applications and targeted Persian-speaking users.
The spyware is propagated via malicious links sent directly through messaging platforms, particularly Telegram. This distribution method enables highly targeted attacks while avoiding broad detection. The uncovered samples indicate that the tool remains in active development, evolving in tandem with the region’s political dynamics.






