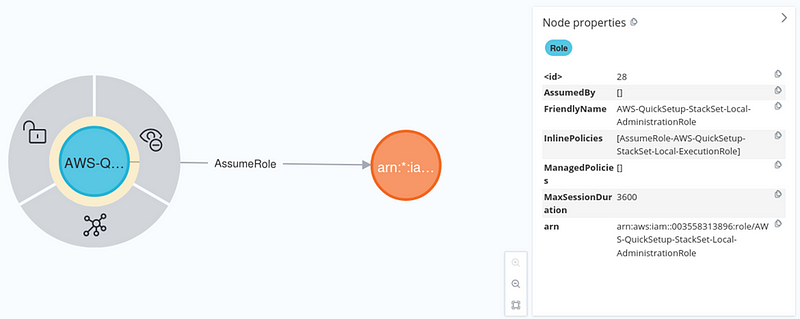
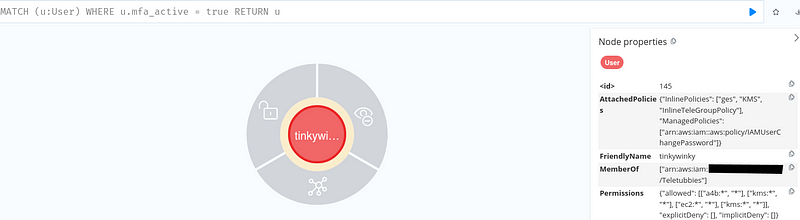
Perhaps the most critical component of an AWS infrastructure is the policy document describing the actions allowed or denied to a resource. IAM can become a messy kitchen as misconfigurations will introduce gaps in resource access. Gordon Ramsey shouting at you would be the least of your problems if threat actors take over your infrastructure.
For this reason, we created dAWShund (arguably a great pun), a suite of tools to enumerate, evaluate and visualise the access conditions between different resources. Let’s put a leash on naughty permissions.
sAWSage
Enumerate AWS IAM entities (groups, roles, and users) and resources across specified regions. The goal is to consolidate and organize Identity-Based Policies (IBPs) and Resource-Based Policies (RBPs) into a unified policy structure for easier management and auditing.
Features
- Enumeration and consolidation of policies attached to IAM entities (groups, roles, users), including both inline and managed policies.
- Identification and canonicalization of policies associated with AWS resources across specified regions.
- Combination of Identity-based Policies (IbPs) and Resource-based Policies (RbPs) into a unified structure, ensuring comprehensive policy coverage.
- Export of Credentials Report to identify interesting metadata such as MFA, access keys.
- Export the consolidated policies into a JSON file (sawsage.json) to use it in the canteen (gerakina.py) and feed the hungry doggy (dAWShund.py).
Currently, resources for the following services are supported:
- AWS Backup
- Elastic File System (EFS)
- Key Management Service (KMS)
- AWS Lambda
- S3
- S3 Glacier
- Secrets Manager
- Simple Notification Service (SNS)
- Simple Queue Service
A complete list of the services supporting Resource-based policies is found here You are encouraged to do a pull request for a service enumerator!
Gerakina
Simulate the policies attached to AWS IAM principals (users, groups, roles) using the simulate-principal-policy API from AWS. AWS uses a flowchart model to decide if an action is allowed or denied. The script parses the policy statements from sawsage for each of the enumerated principals and resources and simulates the policies to export the effective permissions into a new JSON file. The food is now ready to be ingested in dAWShund.
Features
- Reads IAM principal data from a JSON file.
- Simulates IAM policies using AWS
simulate-principal-policyAPI. - Validates and adjusts action names to meet AWS API requirements.
- Outputs effective permissions (allowed, explicit deny, implicit deny) for each principal in a new JSON file.