CVE-2023-35636: Critical Outlook Bug Puts Passwords at Risk
Varonis, a cybersecurity firm, has unearthed a new vulnerability in Microsoft products, alongside several attack methodologies that allow malefactors to acquire users’ password hashes.
Identified as CVE-2023-35636, this critical vulnerability affects the shared calendar function in Outlook, rated as “important” with a 6.5 CVSS score. Through this vulnerability, an attacker can send a specially crafted email that compels Outlook to connect to a server controlled by the hacker, subsequently transmitting the NTLM v2 hash for authentication.
The NTLM v2 protocol, utilized for authenticating users on remote servers, is highly coveted by attackers. The NTLM v2 user password hash can either facilitate a brute force attack to decipher the password in plaintext or be used directly for authentication.
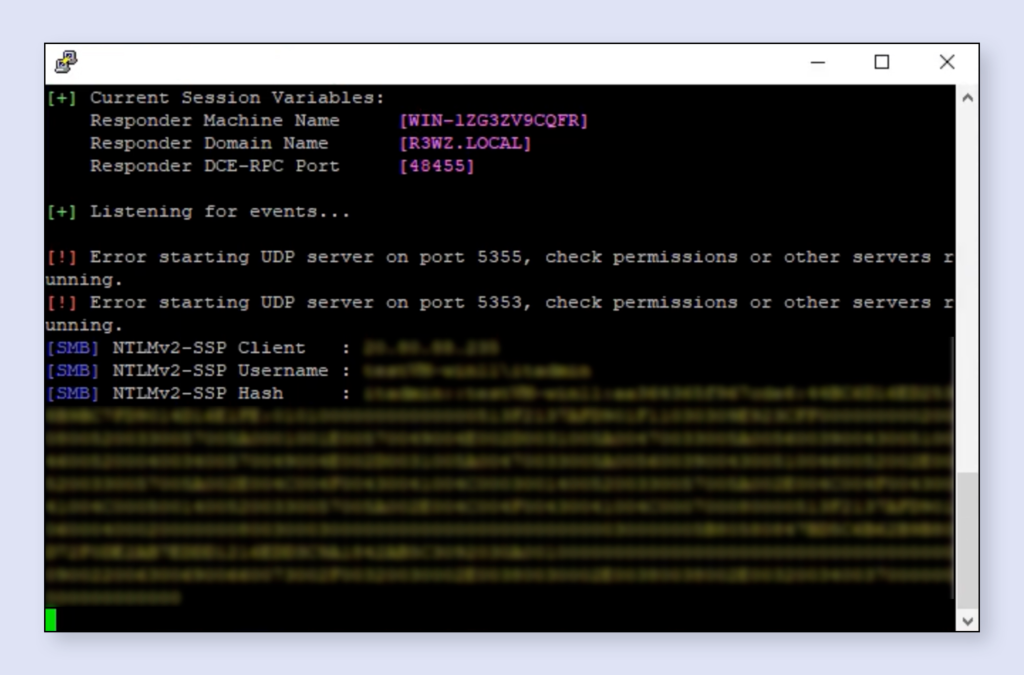
An example of an intercepted NTLM v2 hash.
Microsoft rectified CVE-2023-35636 in an unscheduled security update in December 2023. However, certain attack methods that also allow attackers to obtain the authentication hash remain operational.
One such method employs the Windows Performance Analyzer (WPA), a tool frequently used by developers. Researchers discovered that processing links associated with WPA utilizes a special URI identifier attempting authentication using NTLM v2 over the internet, thereby exposing the NTLM hash.
This technique also involves sending an email containing a link designed to redirect the victim to a malicious WPA payload on a site controlled by the attacker.
Two additional methods exploit the standard Windows File Explorer. Unlike WPA, which is not a default system component and is primarily used by software developers, File Explorer is deeply integrated into Windows and used daily by the vast majority of users. Both attack variants involve the attacker sending a malicious link to the target user via email, social networks, or other channels.
“Once the victim clicks on the link, the attacker can obtain the hash and then attempt to crack the user’s password offline,” Varonis experts explained. “Upon cracking the hash and acquiring the password, the attacker can use it to log into the organization as the user.
As mentioned earlier, CVE-2023-35636 was fixed in December, but the remaining issues still pose a threat. Companies are advised to install the latest security updates and take extra precautions against phishing attacks to avoid falling victim to these malefactors.





