Cppcheck: A static analysis tool for C/C++ code
Cppcheck
Cppcheck is a static analysis tool for C/C++ code. It provides a unique code analysis to detect bugs and focuses on detecting undefined behavior and dangerous coding constructs. The goal is to detect only real errors in the code (i.e. have very few false positives).
Features
Unique code analysis that detects various kinds of bugs in your code.
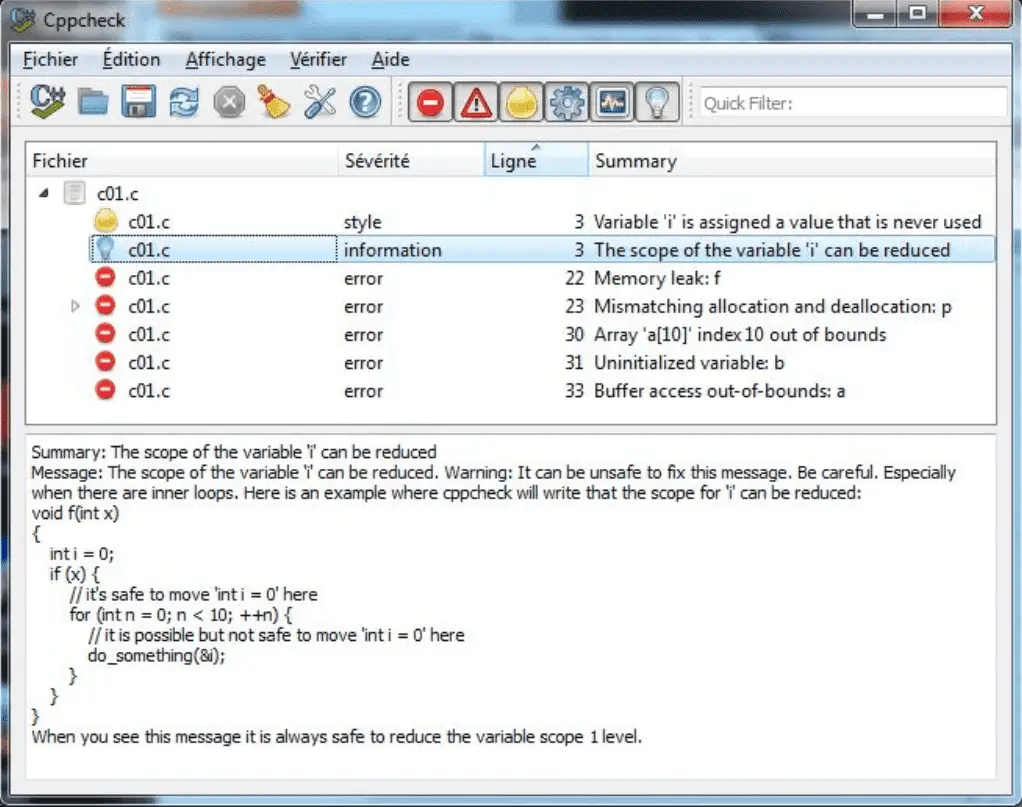
Both command line interface and graphical user interface are available.
Cppcheck has a strong focus on detecting undefined behaviour.
Undefined behaviour
- Dead pointers
- Division by zero
- Integer Overflows
- Invalid bit shift operands
- Invalid conversions
- Invalid usage of STL
- Memory management
- Null pointer dereferences
- Out of bounds checking
- Uninitialized variables
- Writing const data
Security
The most common types of security vulnerabilities in 2017 (CVE count) was:
| Category | Amount | Detected by Cppcheck | ||
| Buffer Errors | 2530 | A few | ||
| Improper Access Control | 1366 | A few (unintended backdoors) | ||
| Information Leak | 1426 | A few (unintended backdoors) | ||
| Permissions, Privileges, and Access Control | 1196 | A few (unintended backdoors) | ||
| Input Validation | 968 | No |
CVEs that was found using Cppcheck:
- CVE-2017-1000249: file : stack-based buffer overflow
This was found by Thomas Jarosch using Cppcheck. The cause is a mistake in a condition. - CVE-2013-6462: 23-year-old stack overflow in X.org that was found with Cppcheck.
This has been described in a few articles (link). - CVE-2012-1147: readfilemap.c in expat before 2.1.0 allows context-dependent attackers to cause a denial of service (file descriptor consumption) via a large number of crafted XML files.
Download
Copyright (C)
Source: https://github.com/danmar/





