Court Recording Software JAVS Compromised by Malware, Thousands at Risk
The Justice AV Solutions (JAVS) program, used for recording court proceedings, was compromised by injecting malware into the installation file, capable of taking control of infected systems. JAVS is widely utilized in courts, law firms, correctional facilities, and government agencies worldwide, with over 10,000 installations.
Upon discovering the threat, the company removed the compromised version from its official website. To prevent future incidents, the company conducted a comprehensive audit of all systems and reset passwords to ensure stolen data could not be used. Through continuous monitoring and collaboration with cybersecurity agencies, attempts by hackers to replace the JAVS Viewer 8.3.7 program with an infected file were identified.
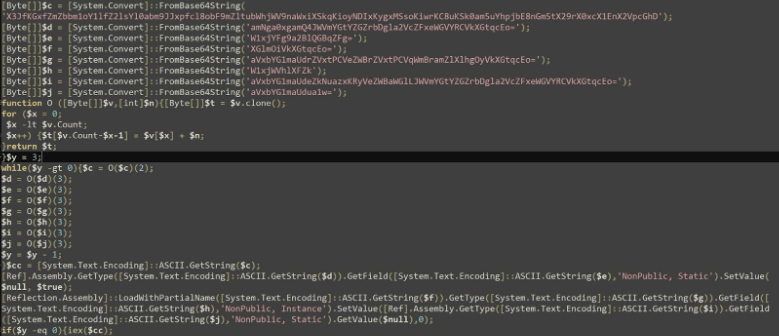
Encoded PowerShell Script Spawned by fffmpeg.exe
JAVS confirmed that all available files on JAVS.com are authentic and free of malware. The company also verified that the JAVS source code, certificates, systems, and other software products were not compromised in the incident.
Cybersecurity firm Rapid7 investigated the incident. The vulnerability was assigned the identifier CVE-2024-4978 (CVSS score: 8.7). It was determined that the threat analysis group S2W Talon first discovered the infected installation file in early April, linking it to the Rustdoor/GateDoor malware.
During the analysis of one incident related to CVE-2024-4978, Rapid7 found that the malware, once installed, sends system information to a C2 server. It then executes two hidden PowerShell scripts that attempt to disable Windows Event Tracing (ETW) and bypass the Anti-Malware Scan Interface (AMSI).
Subsequently, the malware downloads additional malicious files from the C2 server, which harvest credentials from browsers. Rapid7 confirmed that the infected installation file (JAVS.Viewer8.Setup_8.3.7.250-1.exe) was downloaded from the official JAVS website.
Rapid7 urged all JAVS customers to reinstall systems on all potentially compromised devices to completely sever the attackers’ access. Additionally, all credentials on the devices should be reset, and the software should be updated to version 8.3.9 or higher.
Rapid7 explained that simply removing the program is insufficient, as attackers may have implanted additional backdoors or malware. Reinstalling systems allows for a fresh start.





