Google has once again drawn the attention of cybersecurity experts following its implementation of a new user data protection mechanism in the Chrome browser—AppBound Cookie Encryption. Although the initiative reflects an ambitious stride toward bolstering privacy, recent research has revealed vulnerabilities in the system that allow attackers to bypass restrictions and access cookies, even with minimal privileges.
Prior to the introduction of AppBound Cookie Encryption, malware required access to two critical files on Windows systems: a SQLite database named Cookies, which stored encrypted data, and a JSON file called Local State, which held the decryption key. While this key was protected using the Windows Data Protection API (DPAPI), the underlying mechanism was flawed—any process running under the same user context as the browser could decrypt the cookies.
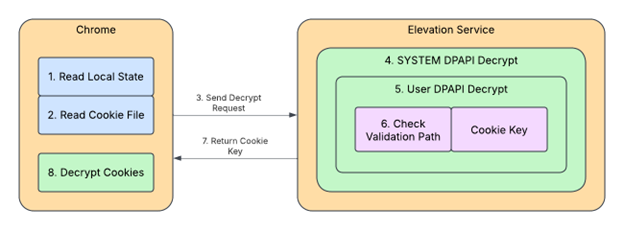
To address this weakness, Google introduced a more intricate encryption scheme. The new approach incorporates an additional protection layer using SYSTEM-level DPAPI, thereby restricting cookie decryption to processes with SYSTEM privileges. Since Chrome itself runs under a standard user context, Google introduced a specialized elevation service—a COM server operating with SYSTEM rights. When Chrome needs to decrypt cookies, it sends a request to this service, which performs a two-step decryption and returns the key.
Despite the enhanced architecture, researchers discovered methods to circumvent the safeguards. The first exploit leverages a vulnerability known as COM hijacking. Since the elevation service functions as a standard COM server, it is susceptible to interception. An attacker could substitute the path to the service’s executable with one pointing to a non-existent library. In such cases, Chrome, unable to reach the original service, reverts to its legacy encryption method—still vulnerable to attacks. While this tactic cannot expose already saved cookies, malware can intercept and decrypt newly generated ones.
A far more critical vulnerability was uncovered in what researchers dubbed C4 — Chrome Cookie Cipher Cracker. This exploit is based on the Padding Oracle Attack, a well-known cryptographic technique used to compromise data encrypted with AES in CBC mode. Although AES remains robust under standard conditions, the combination of CBC and PKCS7 padding introduces weaknesses that can be exploited by carefully manipulating encrypted data and analyzing error logs generated by Windows.
In essence, the attack involves repeatedly altering portions of an encrypted cookie key and submitting them for decryption via the elevation service. Windows system logs, which record decryption errors, act as oracles, revealing whether the decrypted data conforms to expected structures. By iteratively refining inputs and observing responses, attackers can eventually recover the entire encrypted fragment—even when protected with SYSTEM-DPAPI.
Once the outer encryption layer is removed, the inner layer—encrypted for the user—remains. However, because the malicious code operates under that user’s context, a standard call to CryptUnprotectData suffices to unlock the remaining data. Chrome applies an additional “post-processing” step using a hardcoded key and XOR operation, but researchers succeeded in circumventing that as well.
While the attack demands considerable computational effort—full decryption may take up to 16 hours—it fundamentally challenges the perceived security of Chrome cookies and other Chromium-based browsers.
Moreover, experts demonstrated that the C4 technique is not limited to cookies. Any data encrypted with SYSTEM-level DPAPI becomes a potential target. For instance, researchers discovered SYSTEM-encrypted objects in the Windows Credential Manager containing SOAP-XML documents with account credentials. They also theorized the possibility of extracting saved passwords from the Task Scheduler when configured with stored credentials.
This research highlights the risk of layering modern defenses atop aging security frameworks. In this case, the deployment of AppBound Cookie Encryption inadvertently empowered attackers to exploit existing Windows system components.
The research team responsibly disclosed their findings to both Google and Microsoft. Google acknowledged the vulnerability and has begun issuing fixes. A partial update is already available in Chrome, though it remains disabled by default. A full resolution is expected in future browser releases. Microsoft, however, declined to classify the issue as a security threat, citing the low feasibility of real-world exploitation due to its dependence on physical access and specific operational conditions.
The ongoing situation surrounding AppBound Cookie Encryption and the C4 attack underscores a sobering truth: even the most sophisticated security architectures can harbor latent weaknesses—especially when built upon complex, yet imperfect foundations like DPAPI and CBC encryption.






