China-Linked Hackers Target Asia-Pacific with Deuterbear RAT, Researchers Reveal
Cybersecurity researchers have unveiled new details about a remote access Trojan called Deuterbear RAT, used by the China-affiliated hacker group BlackTech in a cyber-espionage campaign targeting the Asia-Pacific region.
BlackTech, active since at least 2007, is known by many names, including Circuit Panda, Earth Hundun, HUAPI, Manga Taurus, Palmerworm, Red Djinn, and Temp.Overboard.
For many years, BlackTech employed the malicious Waterbear in its nefarious campaigns, but since October 2022, the group has also been using its updated version called Deuterbear.
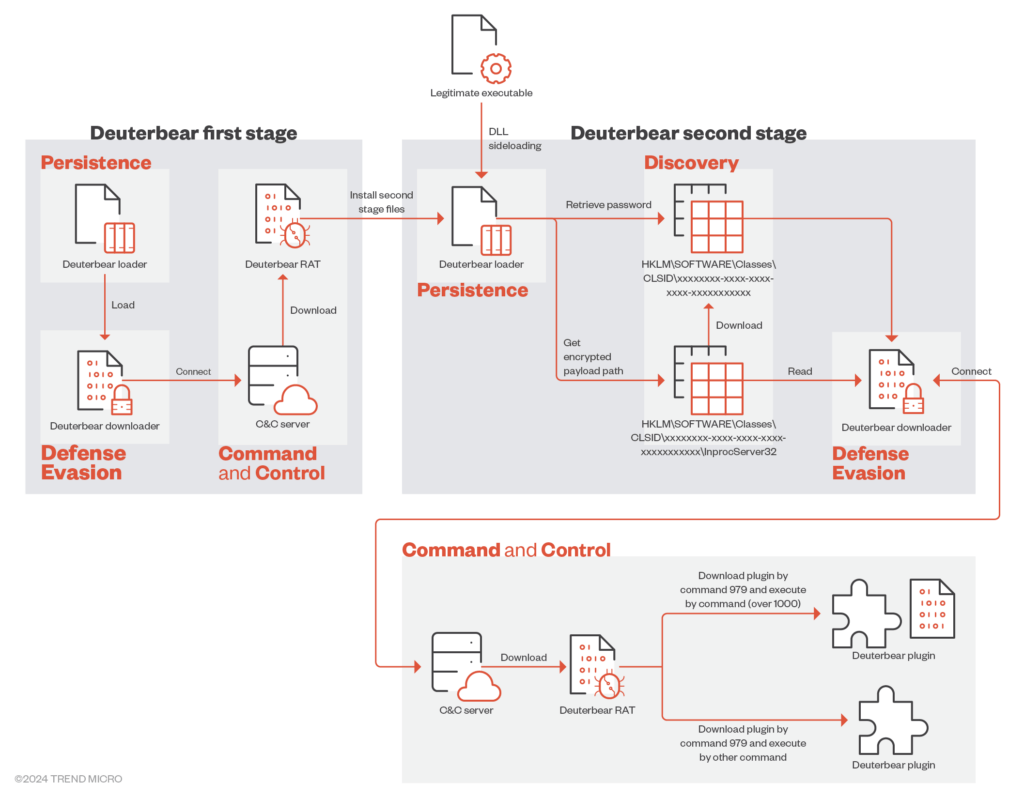
Installation pathway of Deuterbear
“Deuterbear, while similar to Waterbear in many ways, shows advancements in capabilities such as including support for shellcode plugins, avoiding handshakes for RAT operation, and using HTTPS for C&C communication,” explained Pierre Li and Cyriis Tseng, researchers at Trend Micro, in their new analysis.
“Comparing the two malware variants, Deuterbear uses a shellcode format, possesses anti-memory scanning, and shares a traffic key with its downloader unlike Waterbear,” the specialists added.
Both malware variants are distributed through a dedicated loader using DLL sideloading, employing malicious libraries paired with legitimate executable files to load and decrypt the malicious module directly. However, the older malware had a more complex installation process.
Researchers state that Deuterbear RAT is, overall, a simplified version of its predecessor, retaining only hard-coded commands compared to Waterbear’s plugin-based approach for adding additional functionality.
Experts also believe that the malware serves somewhat different purposes, so they will continue to evolve independently of each other. This complexity poses a challenge for security teams, who must monitor a greater number of threats and maintain heightened vigilance.





