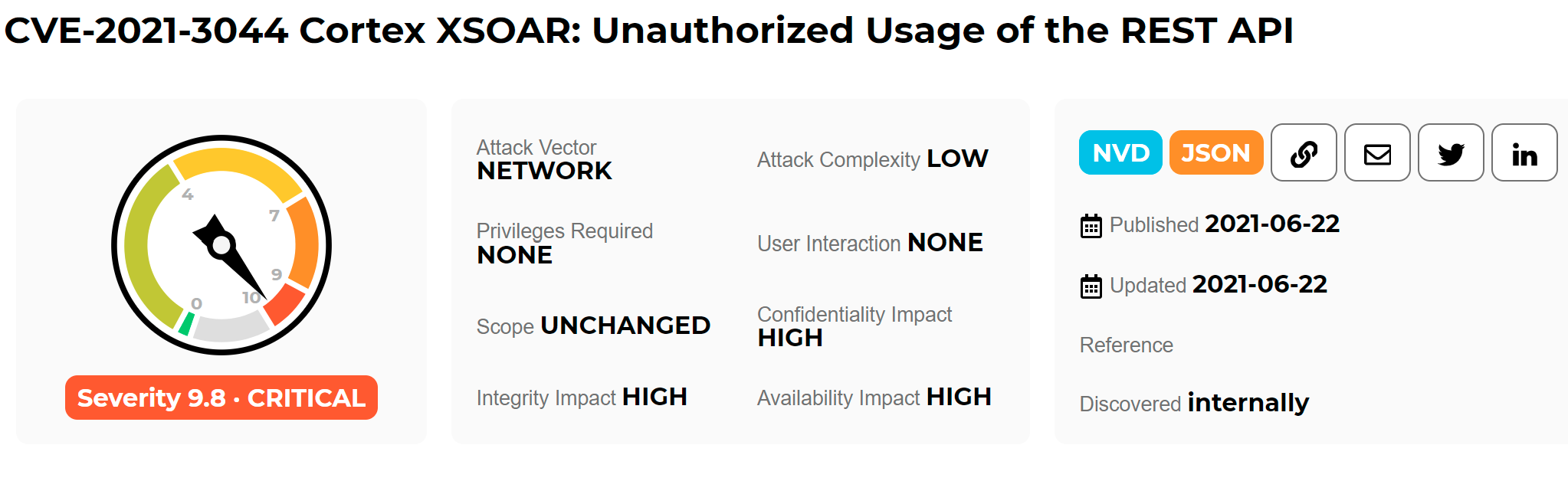
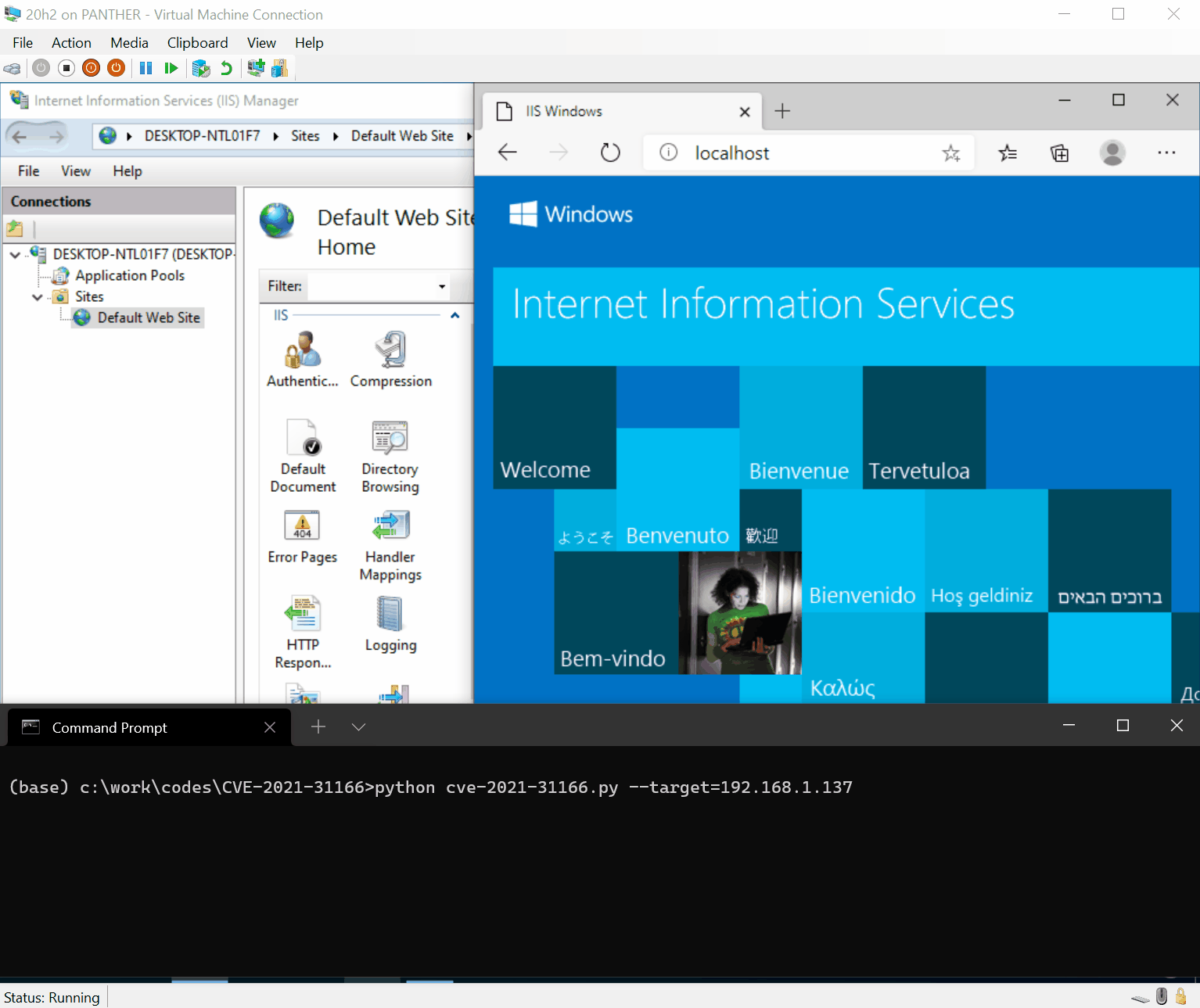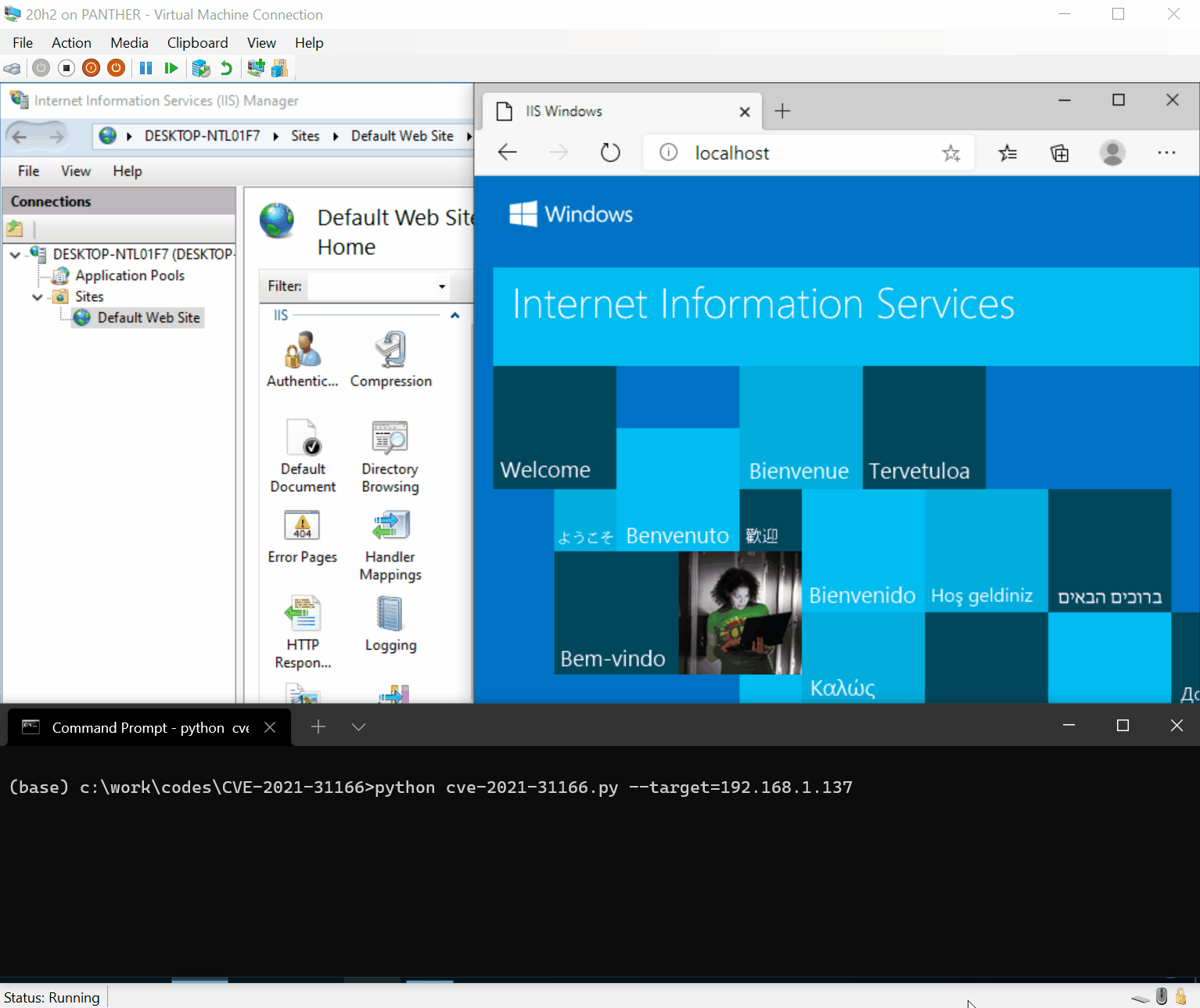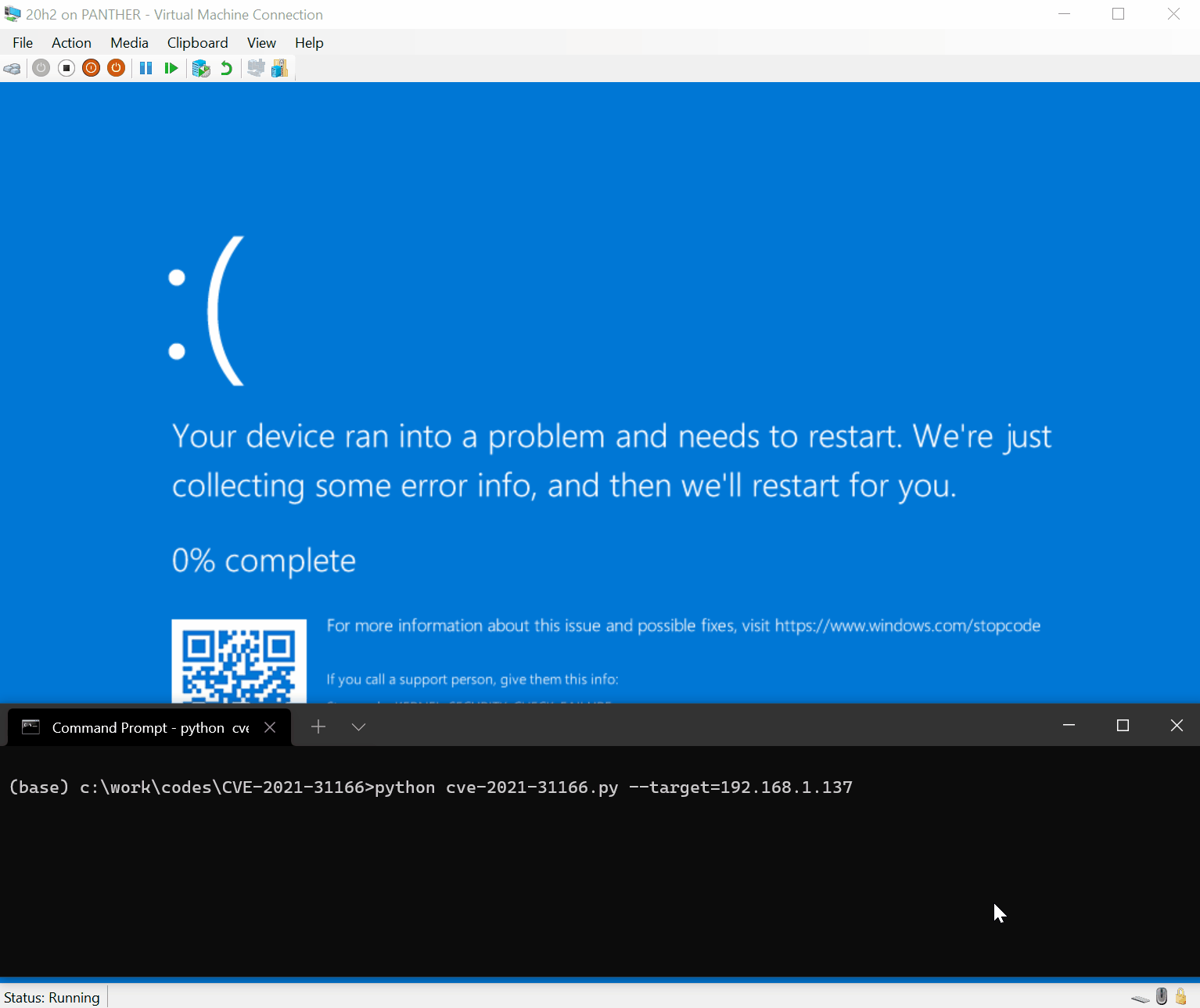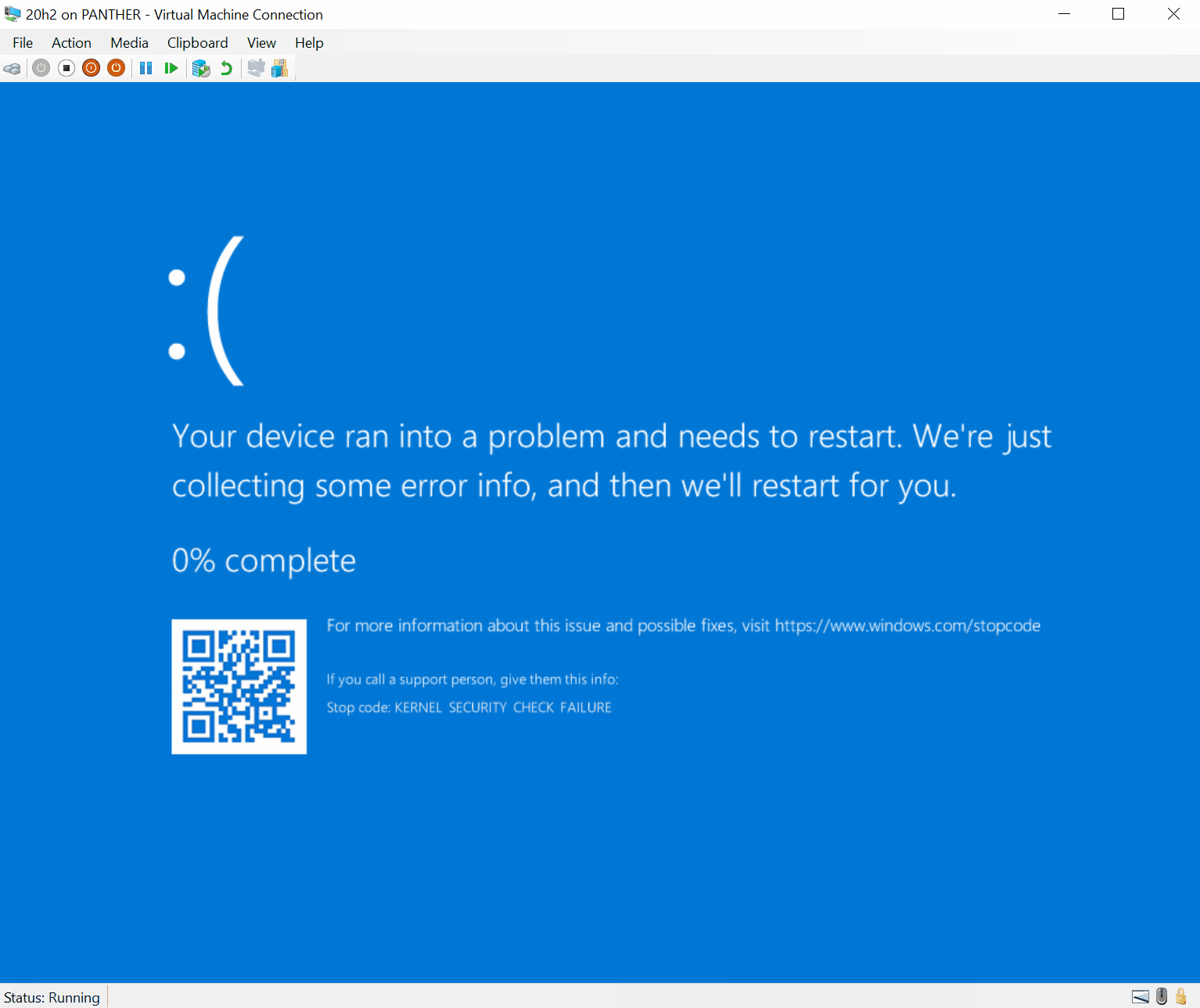
Dell SupportAssist vulnerability affects 30 million PCs
Recently, security researchers discovered four security vulnerabilities in the BIOSConnect feature of Dell SupportAssist. These vulnerabilities allow attackers to remotely execute code in the BIOS of the affected device. According to the official Dell...