Category: Open Source Tool
BadZure BadZure is a PowerShell script that leverages the Microsoft Graph SDK to orchestrate the setup of Azure Active Directory tenants, populating them with diverse entities while also introducing common security misconfigurations to create...
Frida-Jit-unPacker The Frida-Jit-unPacker aims to help researchers and analysts understand the behavior of malicious .NET packed samples in order to provide a mitigation. This tool uses the Frida instrumentation toolkit to inject scripts into the CLR...
IPPrint C2 A Proof-of-Concept for using Microsoft Windows printers for persistence/command and control via Internet Printing. Printing systems are an often overlooked target for attackers looking to establish command and control (C2) channels on...
ELFieScanner A C++ POC for advanced process memory scanning that attempts to detect many malicious techniques used by threat actors & those that have been incorporated into open-source user-mode rootkits. ELFieScanner inspects every running...
RWX MEMEORY HUNT AND INJECTION DV Abusing Windows fork API and OneDrive.exe process to inject the malicious shellcode without allocating new RWX memory region. This technique is finding RWX region in already running processes...
IconJector This is a Windows Explorer DLL injection technique that uses the change icon dialog on Windows. How does it work? Firstly, a folder is created in the temp directory, and the properties of...
SharpGraphView Sharp post-exploitation toolkit providing modular access to the Microsoft Graph API (graph.microsoft.com) for cloud and red team operations. Methods Auth Methods: Command Description Get-GraphTokens Get graph token via device code phish (saved to graph_tokens.txt)...
Immoral Fiber This repository contains two new offensive techniques using Windows Fibers: PoisonFiber (The first remote enumeration & Fiber injection capability POC tool) PhantomThread (An evolved callstack-masking implementation) It also contains an example test...
Amnesiac Amnesiac is a post-exploitation framework designed to assist with lateral movement within active directory environments. Amnesiac is being developed to bridge a gap on Windows OS, where post-exploitation frameworks are not readily available unless...
okta-terrify Okta Terrify is a tool to demonstrate how passwordless solutions such as Okta Verify’s FastPass or other FIDO2/WebAuthn type solutions can be abused once an authenticator endpoint has been compromised. Whilst Okta Terrify...
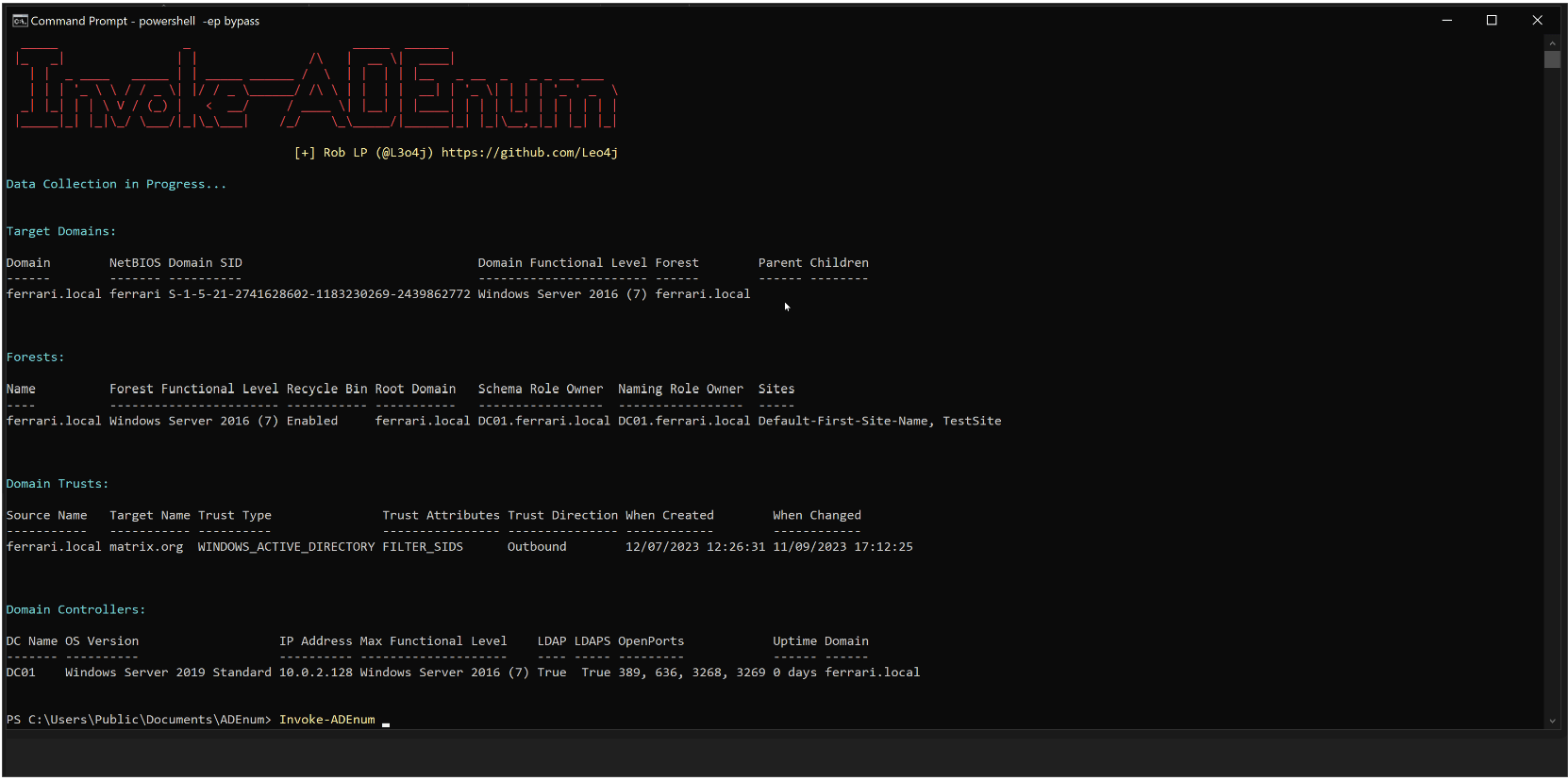
Invoke-ADEnum Invoke-ADEnum is an enumeration tool designed to automate the process of gathering information from an Active Directory environment. With Invoke-ADEnum, you can enumerate various aspects of Active Directory, including forests, domains, trusts, domain...
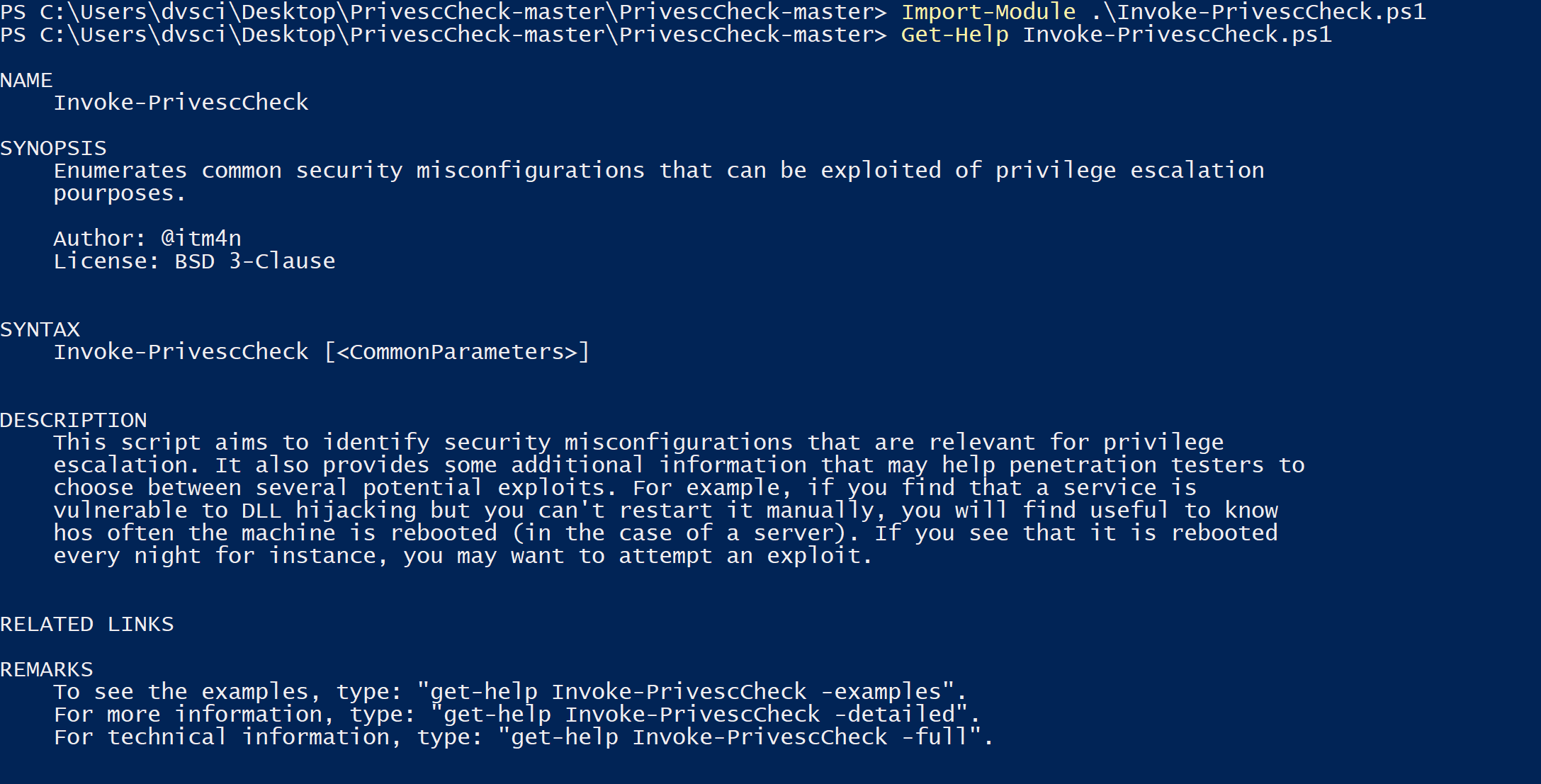
PrivescCheck This script aims to identify Local Privilege Escalation (LPE) vulnerabilities that are usually due to Windows configuration issues, or bad practices. It can also gather useful information for some exploitation and post-exploitation tasks. Check types...
GoDefender This Go package provides functionality to detect and defend against various forms of debugging tools and virtualization environments Anti-Virtualization Triage Detection: Detects if the system is running in a triage or analysis environment....
What is afrog afrog is a high-performance vulnerability scanner that is fast and stable. It supports user-defined PoC and comes with several built-in types, such as CVE, CNVD, default passwords, information disclosure, fingerprint identification,...
FalconHound FalconHound is a blue team multi-tool. It allows you to utilize and enhance the power of BloodHound in a more automated fashion. It is designed to be used in conjunction with an SIEM...
reconftw reconFTW automates the entire process of reconnaissance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target. reconFTW uses a lot of techniques...