Category: Open Source Tool
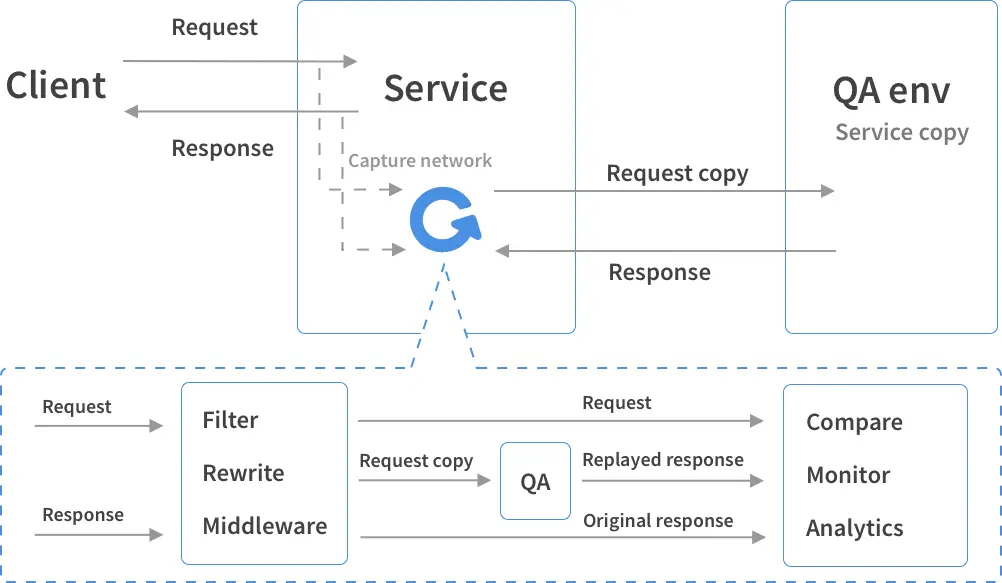
goreplay GoReplay is an open-source network monitoring tool which can record your live traffic and use it for shadowing, load testing, monitoring, and detailed analysis. As your application grows, the effort required to test...
BOAZ (Bypass, Obfuscate, Adapt, Zero-trace) evasion was inspired by the concept of multi-layered approach which is the evasive version of defence-in-depth first mentioned in “One packer to rule them all” at BH USA14 (Swinnen...
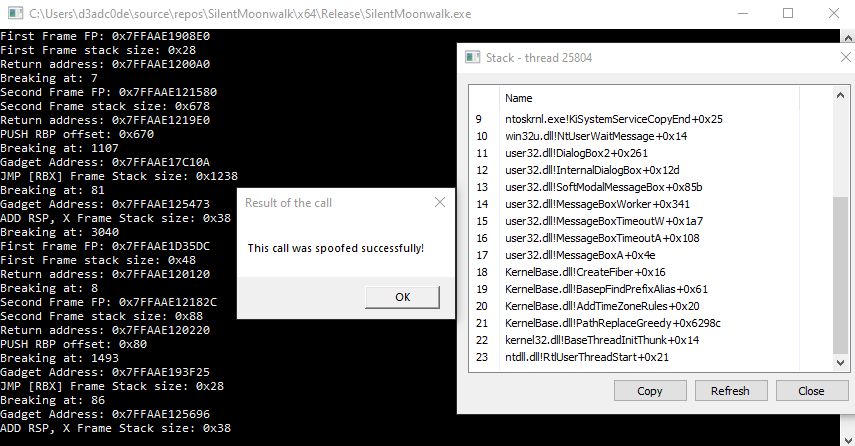
SilentMoonwalk SilentMoonwalk is a PoC implementation of a fully dynamic call stack spoofer, implementing a technique to remove the original caller from the call stack, using ROP to desynchronize unwinding from the control flow....
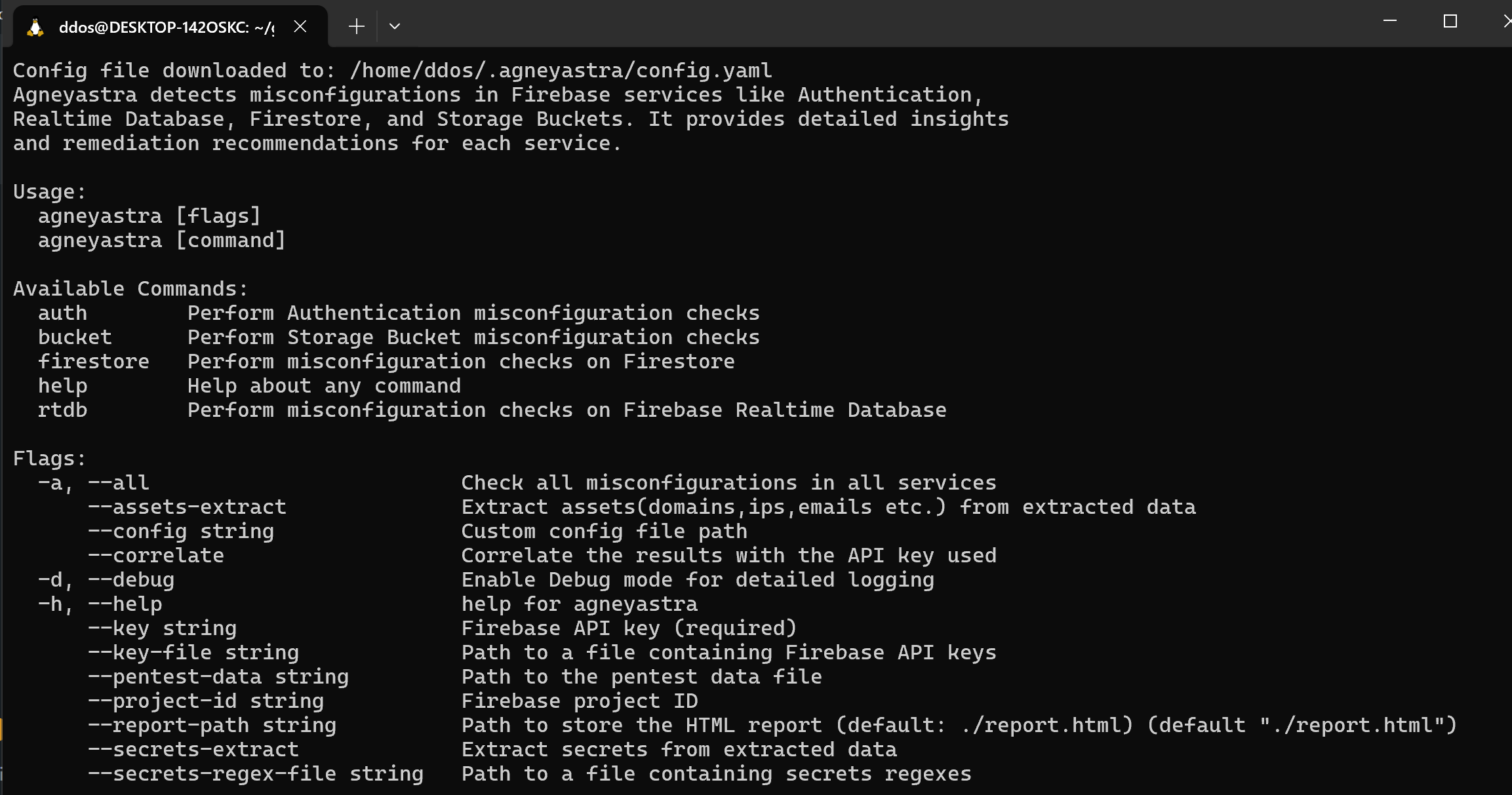
Firebase, a versatile platform by Google, powers countless web and mobile applications with its extensive suite of services including real-time databases, authentication, cloud storage, and hosting. Its ubiquity and ease of use make it...
Quiet Riot An enumeration tool for scalable, unauthenticated validation of AWS principals; including AWS Account IDs, root e-mail addresses, users, and roles. Featureploitation Limits Throttling After performing extensive analysis of scaling methods using the...
A tool specifically designed for Kubernetes environments aims to efficiently and automatically discover hidden vulnerable APIs within clusters. It reveals and demonstrates a common error through a workshop format, which could lead to API...
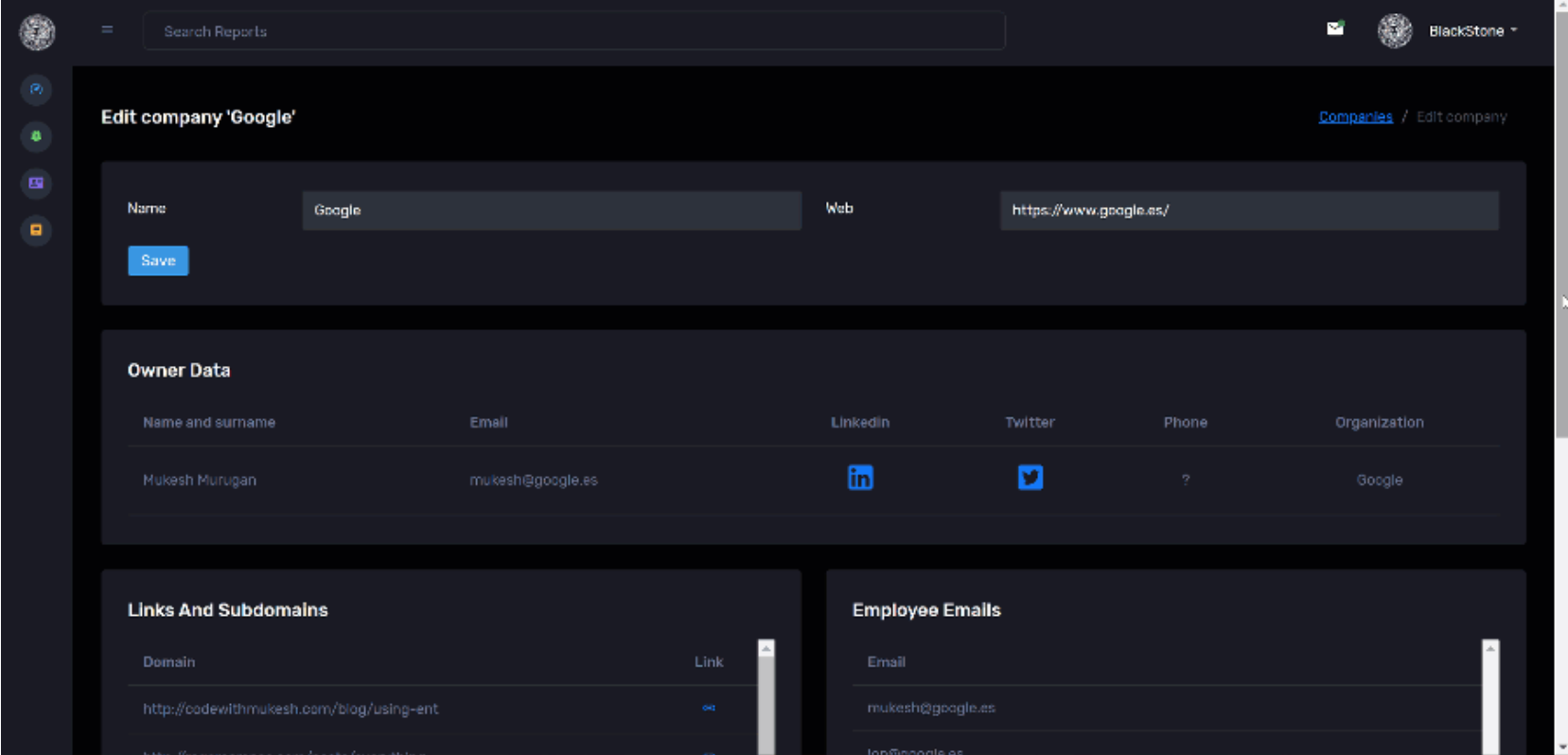
BlackStone Project BlackStone project or “BlackStone Project” is a tool created in order to automate the work of drafting and submitting a report on audits of ethical hacking or pentesting. In this tool we...
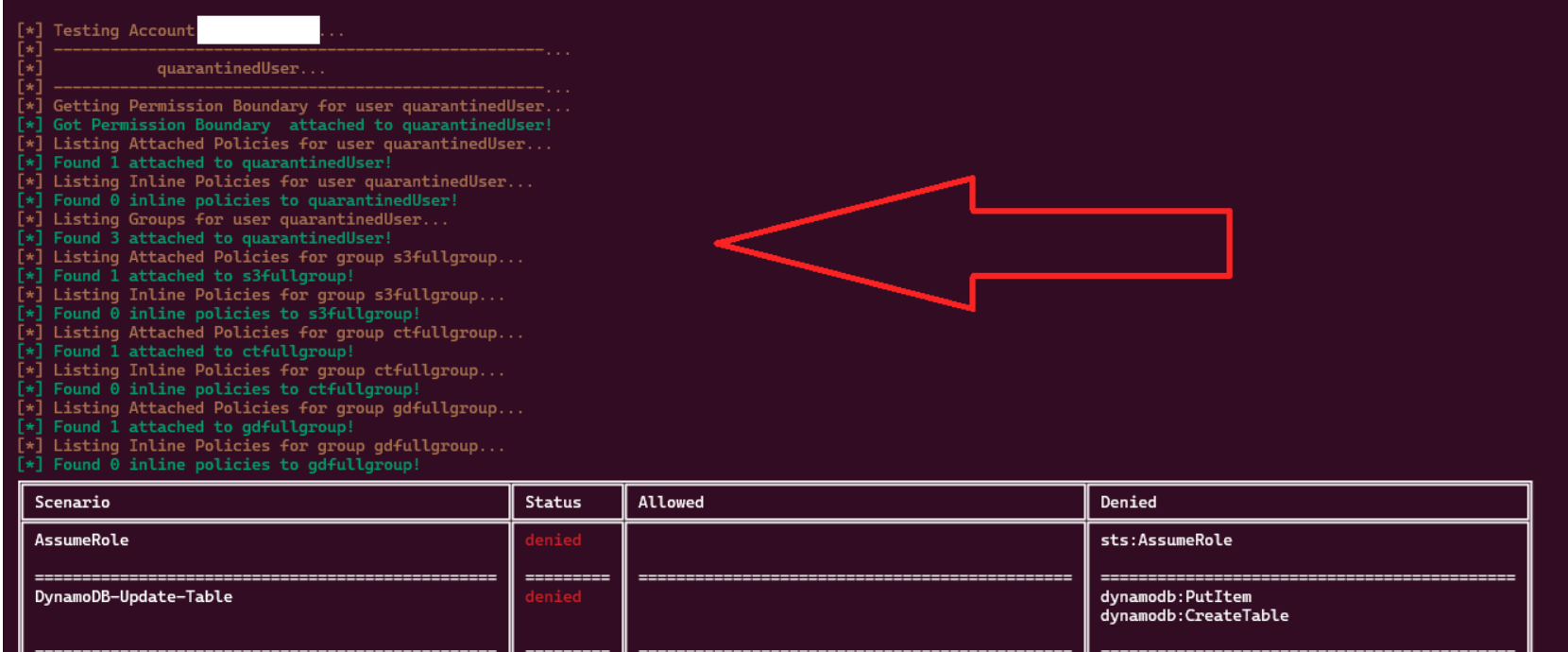
DetentionDodger is a tool designed to find users whose credentials have been leaked/compromised and the impact they have on the target. Install Local Installation To install, the only thing needed, is to install the...
WindowSpy WindowSpy is a Cobalt Strike Beacon Object File meant for targeted user surveillance. The goal of this project was to trigger surveillance capabilities only on certain targets, e.g. browser login pages, confidential documents,...
In recent years, attacks targeting the Web Application Platform have been increasing rapidly. sisakulint is a static and fast SAST for GitHub Actions. This great tool can automatically validate yaml files according to the guidelines...
KubeStalk KubeStalk is a tool to discover Kubernetes and related infrastructure-based attack surfaces from a black-box perspective. This tool is a community version of the tool used to probe for unsecured Kubernetes clusters around...
SupplyShield is an open-source application security orchestration framework designed to secure your software supply chain from vulnerabilities, malicious dependencies, and unapproved base images. It provides a comprehensive solution to automate the detection, prioritization, and...
sh4d0wup Have you ever wondered if the update you downloaded is the same one everybody else gets or did you get a different one that was made just for you? Shadow updates are updates that...
An AI-powered, self-hosted GitHub bot designed to detect and mitigate supply chain attacks in pull requests. SadGuard combines intelligent code analysis with executable behavior monitoring to secure your software pipeline. SadGuard was inspired by...
Introducing Varunastra, an innovative tool designed to enhance the security of Docker environments. Named after The Varunastra (वरुणास्त्र), it is the water weapon according to the Indian scriptures, incepted by Varuna, god of hydrosphere....
Metlo Metlo is an open-source API security platform Create an Inventory of all your API Endpoints. Proactively test your APIs before they go into production. Detect API attacks in real-time. Features Endpoint Discovery –...