Category: Open Source Tool
mihari A query aggregator for OSINT based threat hunting. Mihari can aggregate multiple searches across multiple services in a single rule & persist findings in a database. How it works Mihari makes a...
js-x-ray JavaScript AST analysis. This package has been created to export the Node-Secure AST Analysis to enable better code evolution and allow better access to developers and researchers. The goal is to quickly identify dangerous code...
Reverse Engineers’ Hex Editor A cross-platform (Windows, Linux, Mac) hex editor for reverse engineering, and everything else. Features Large (1TB+) file support Decoding of integer/floating point value types Inline disassembly of machine code Highlighting...
Secret Magpie Organizations struggle to scan for leaked secrets in ALL of their repos. It’s easy to scan one repo, but time-consuming and tedious to scan all of them. SecretMagpie is a secret detection...
teler-waf teler-waf is a comprehensive security solution for Go-based web applications. It acts as an HTTP middleware, providing an easy-to-use interface for integrating IDS functionality with teler IDS into existing Go applications. By using teler-waf, you can...
CloudFox CloudFox helps you gain situational awareness in unfamiliar cloud environments. It’s an open-source command line tool created to help penetration testers and other offensive security professionals find exploitable attack paths in cloud infrastructure....
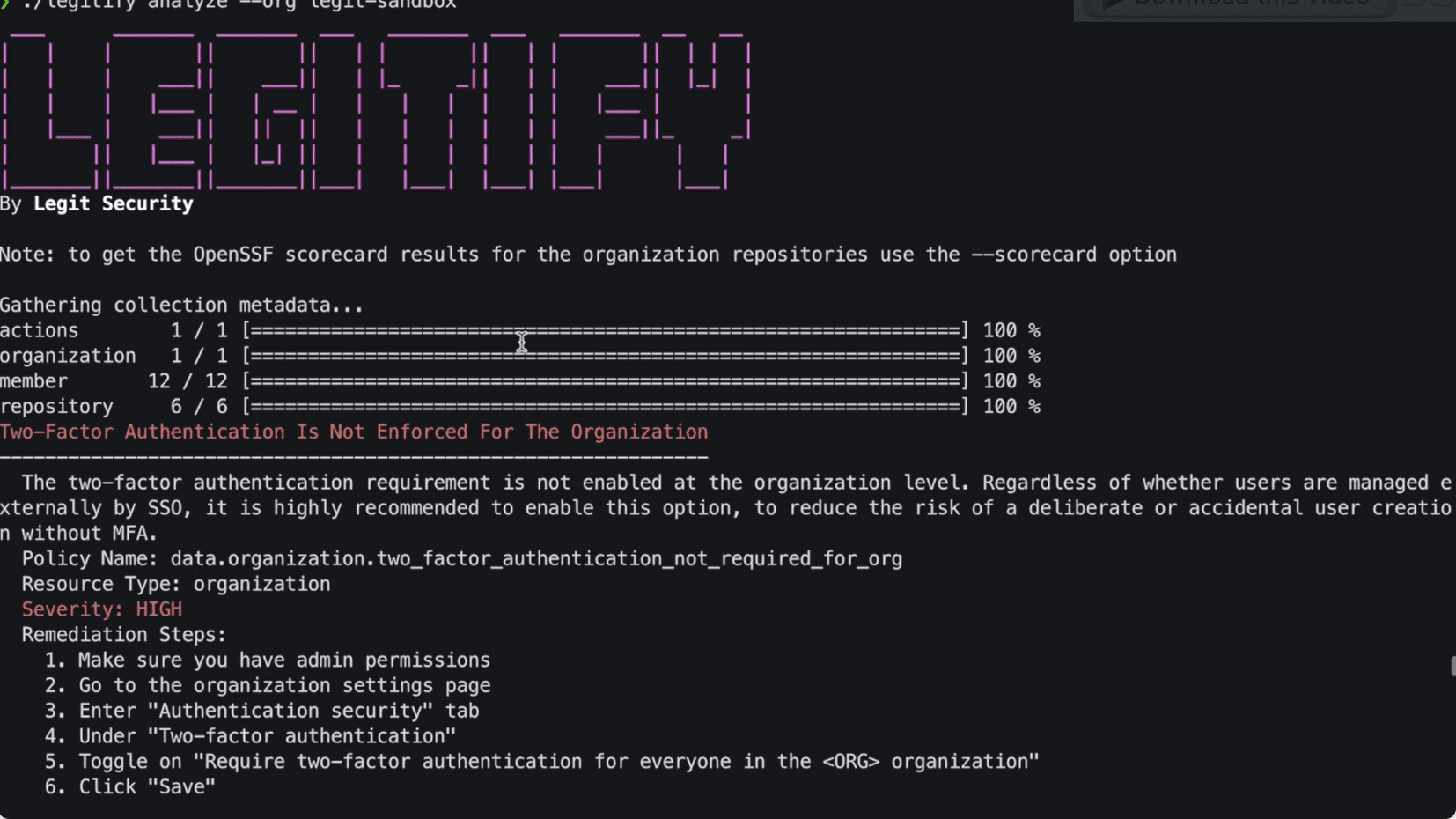
legitify Detect and remediate misconfigurations, security, and compliance issues across all your GitHub assets with ease. Scorecard Support scorecard is an OSSF’s open-source project: Scorecards is an automated tool that assesses a number of...
GUAC: Graph for Understanding Artifact Composition Graph for Understanding Artifact Composition (GUAC) aggregates software security metadata into a high-fidelity graph database—normalizing entity identities and mapping standard relationships between them. Querying this graph can drive...
ModelScan: Protection Against Model Serialization Attacks Machine Learning (ML) models are shared publicly over the internet, within teams, and across teams. The rise of Foundation Models have resulted in public ML models being increasingly...
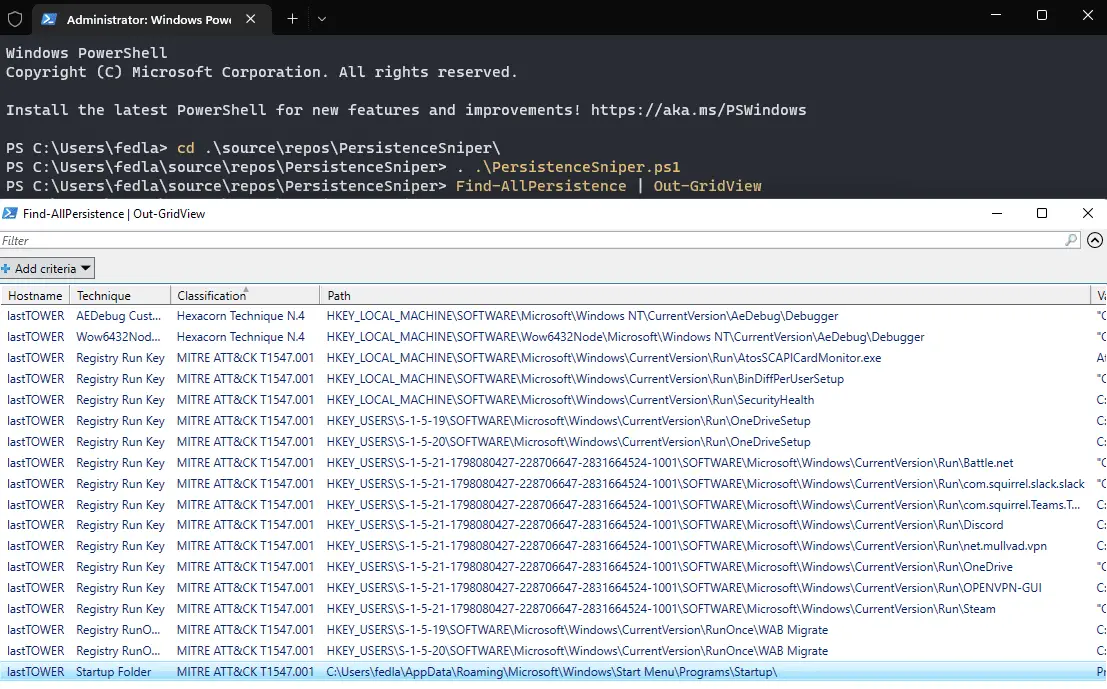
PersistenceSniper PersistenceSniper is a Powershell script that can be used by Blue Teams, Incident Responders, and System Administrators to hunt persistences implanted in Windows machines. The script is also available on Powershell Gallery. The...
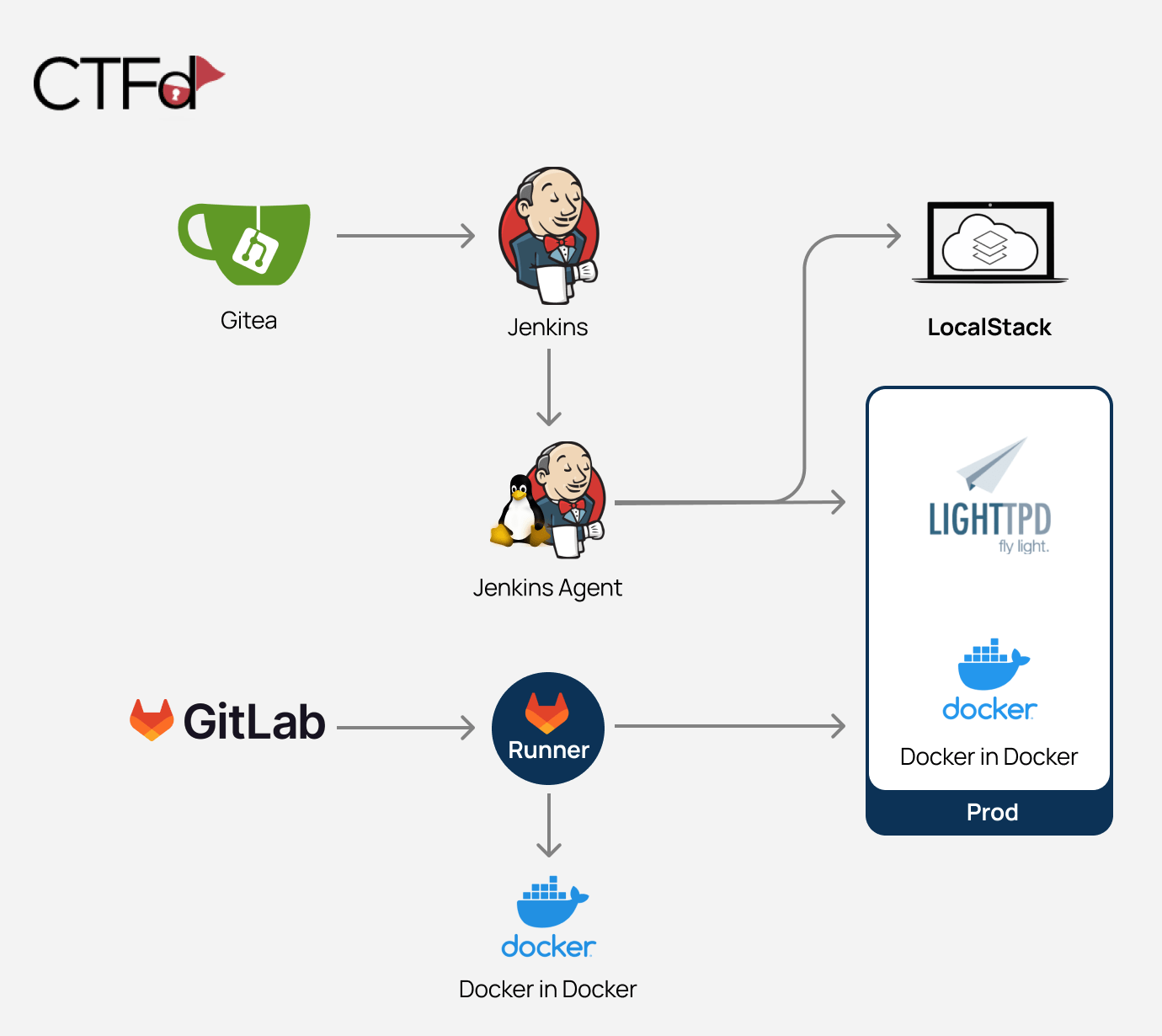
cicd-goat The CI/CD Goat project allows engineers and security practitioners to learn and practice CI/CD security through a set of 10 challenges, enacted against a real, full-blown CI/CD environment. The scenarios are of varying...
route-detect Find authentication (authn) and authorization (authz) security bugs in web application routes: Web application HTTP route authn and authz bugs are some of the most common security issues found today. These industry standard...
Firefly Firefly is an advanced black-box fuzzer and not just a standard asset discovery tool. Firefly provides the advantage of testing a target with a large number of built-in checks to detect behaviors in...
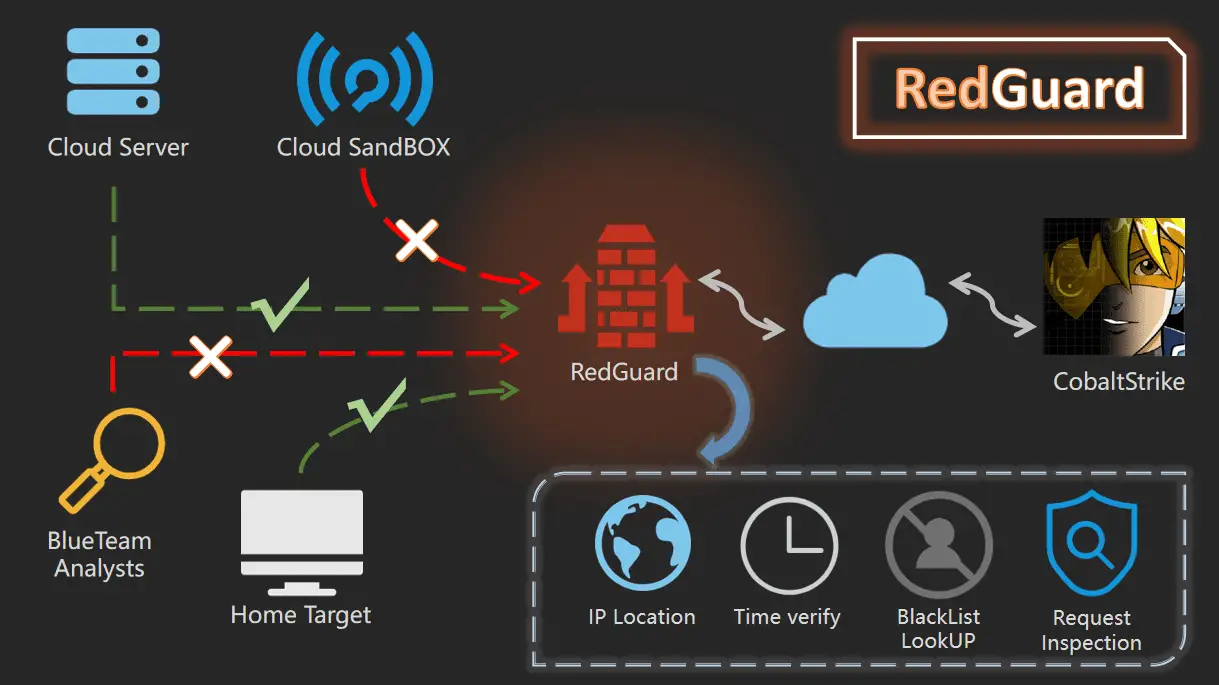
RedGuard – Excellent C2 Front Flow Control tool RedGuard is a derivative work of the C2 facility pre-flow control technology. It has a lighter design, efficient flow interaction, and reliable compatibility with go language...
tartufo tartufo searches through git repositories for secrets, digging deep into commit history and branches. This is effective at finding secrets accidentally committed. tartufo also can be used by git pre-commit scripts to screen changes for secrets...
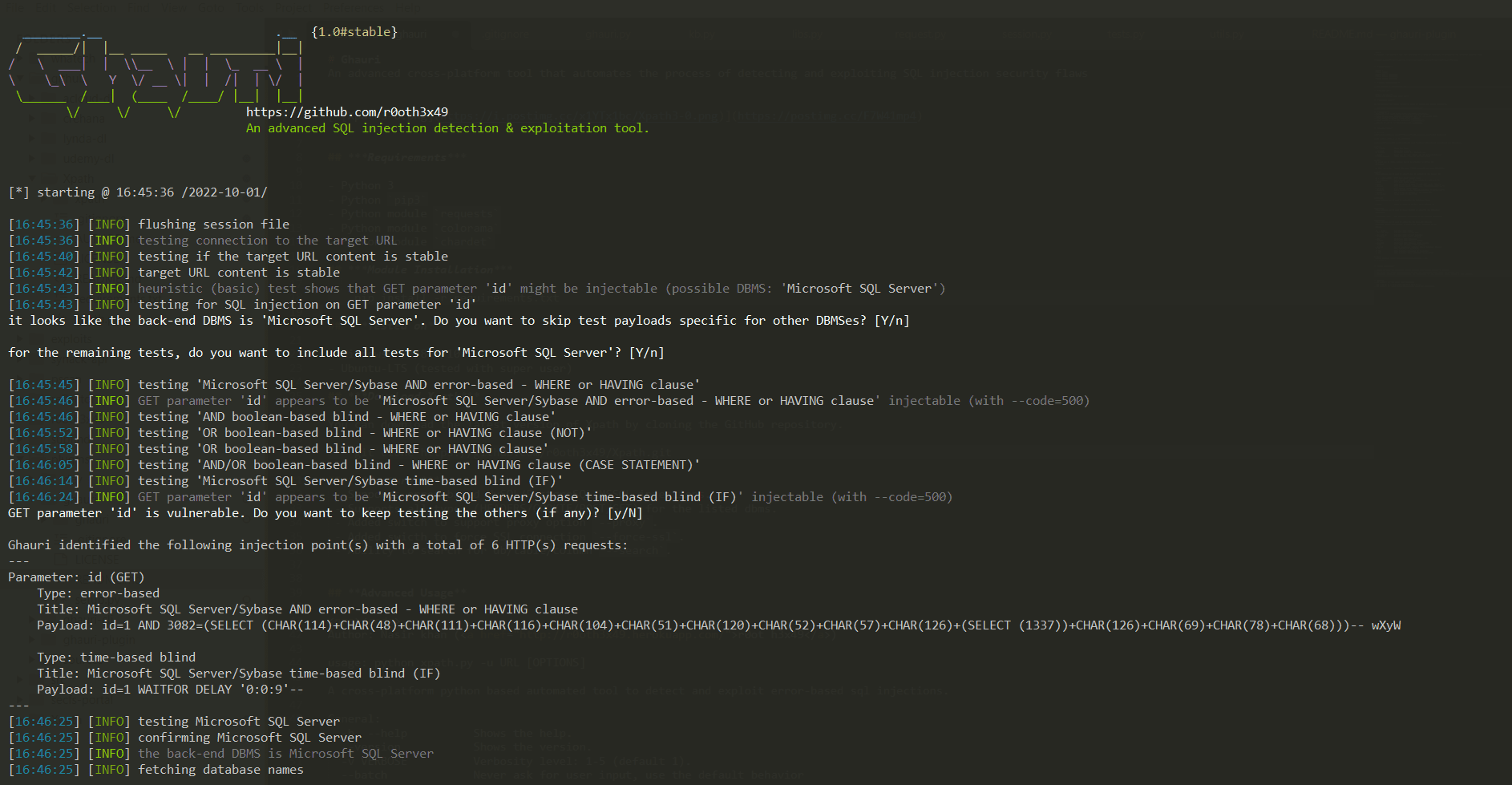
Ghauri An advanced cross-platform tool that automates the process of detecting and exploiting SQL injection security flaws Features Supports the following types of injection payloads: Boolean based. Error Based Time-Based Stacked Queries Support SQL...