Category: Open Source Tool
Sysdig Inspect Sysdig Inspect is a powerful opensource interface for container troubleshooting and security investigation Inspect’s user interface is designed to intuitively navigate the data-dense sysdig captures that contain granular system, network, and application activity...
DRAKVUF Sandbox DRAKVUF Sandbox is an automated black-box malware analysis system with a DRAKVUF engine under the hood. This project provides you with a friendly web interface that allows you to upload suspicious files to...
VAST — Visibility Across Space and Time VAST is a network telemetry engine for data-driven security investigations. It ingests high-volume streams of network and logs data, indexes it for later retrieval, and offers several...
Mitaka Mitaka is a browser extension that makes your OSINT (Open Source Intelligence) search & scan easier. Key features: Auto IoC (indicators of compromise) selection with refanging. E.g. example[.]com to example.com, test[at]example.com to test@example.com, hxxp://example.com to http://example.com, etc. Supports 65+ services. Features ...
HAL- Hardware Analyzer Virtually all available research on netlist analysis operates on a graph-based representation of the netlist under inspection. At its core, HAL provides exactly that: A framework to parse netlists of arbitrary...
Parsec Parsec allows you to easily share your work and data in the cloud in total privacy thanks to end-to-end cryptographic security. Key features: Works as a virtual drive on you computer. You can...
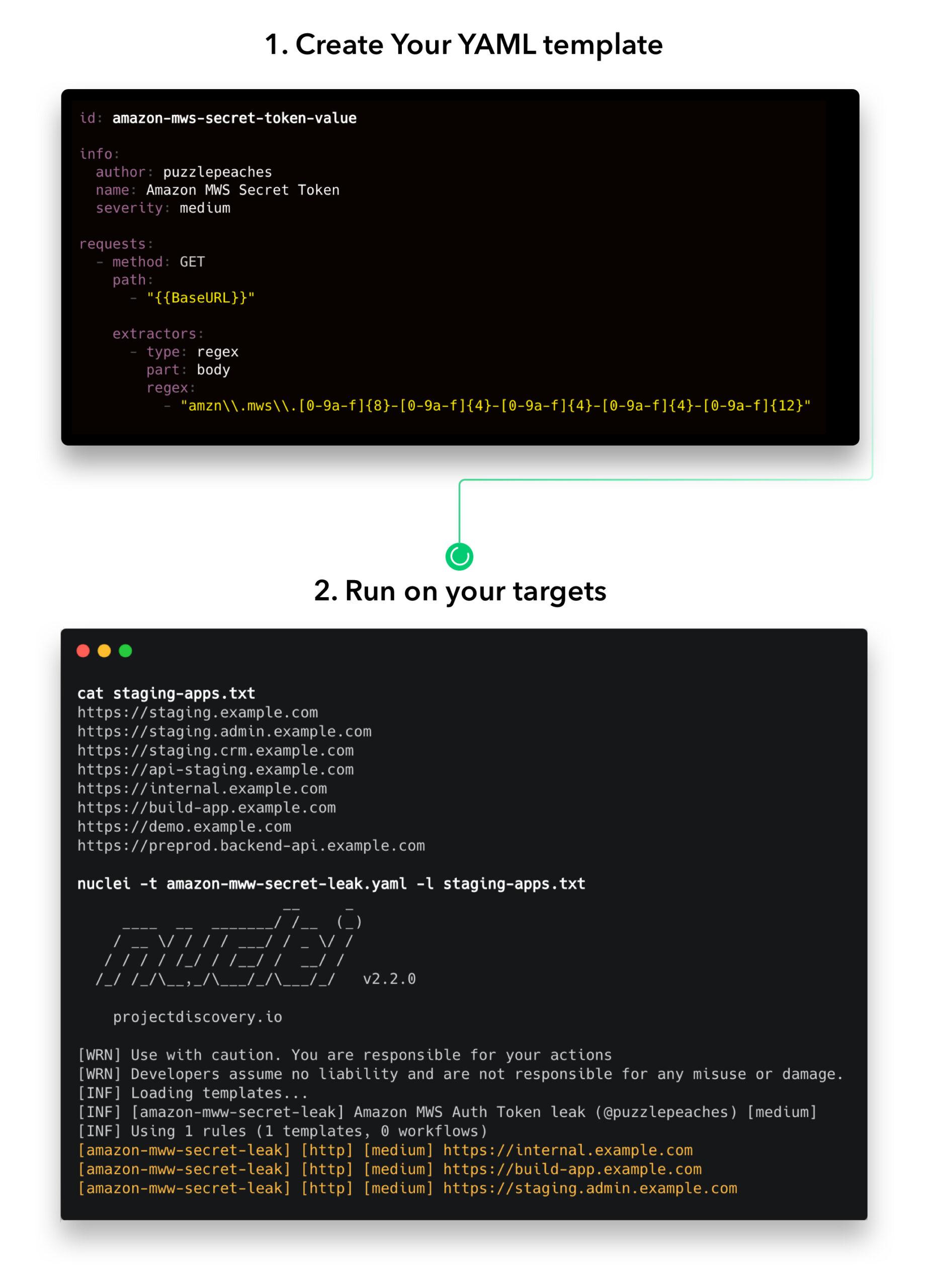
Nuclei Nuclei is a fast vulnerability scanner designed to probe modern applications, infrastructure, cloud platforms, and networks, aiding in the identification and mitigation of exploitable vulnerabilities. At its core, Nuclei uses templates—expressed as straightforward...
Security Scorecards Goals Automate analysis and trust decisions on the security posture of open source projects. Use this data to proactively improve the security posture of the critical projects the world depends on. Checks...
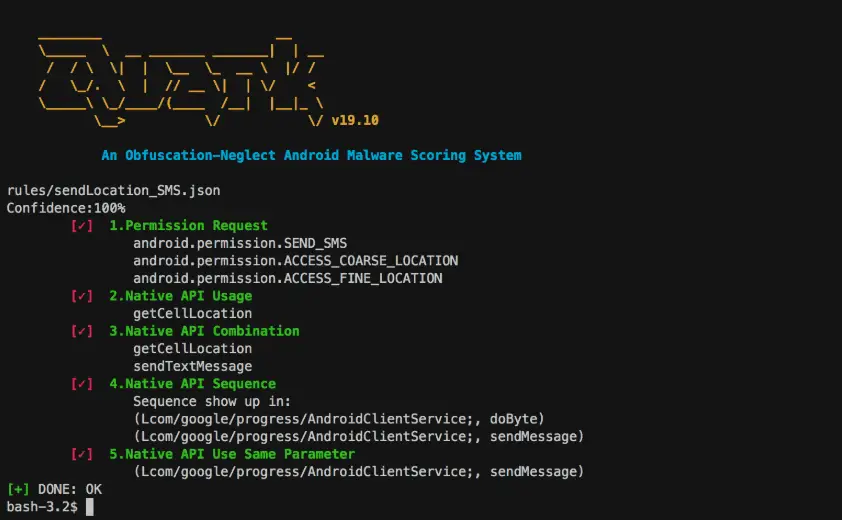
Quark Engine An Obfuscation-Neglect Android Malware Scoring System Android malware analysis engine is not a new story. Every antivirus company has its secrets to build it. With curiosity, we develop a malware scoring system...
nipe The Tor project allows users to surf the Internet, chat, and send instant messages anonymously through its mechanism. It is used by a wide variety of people, companies, and organizations, both for lawful...
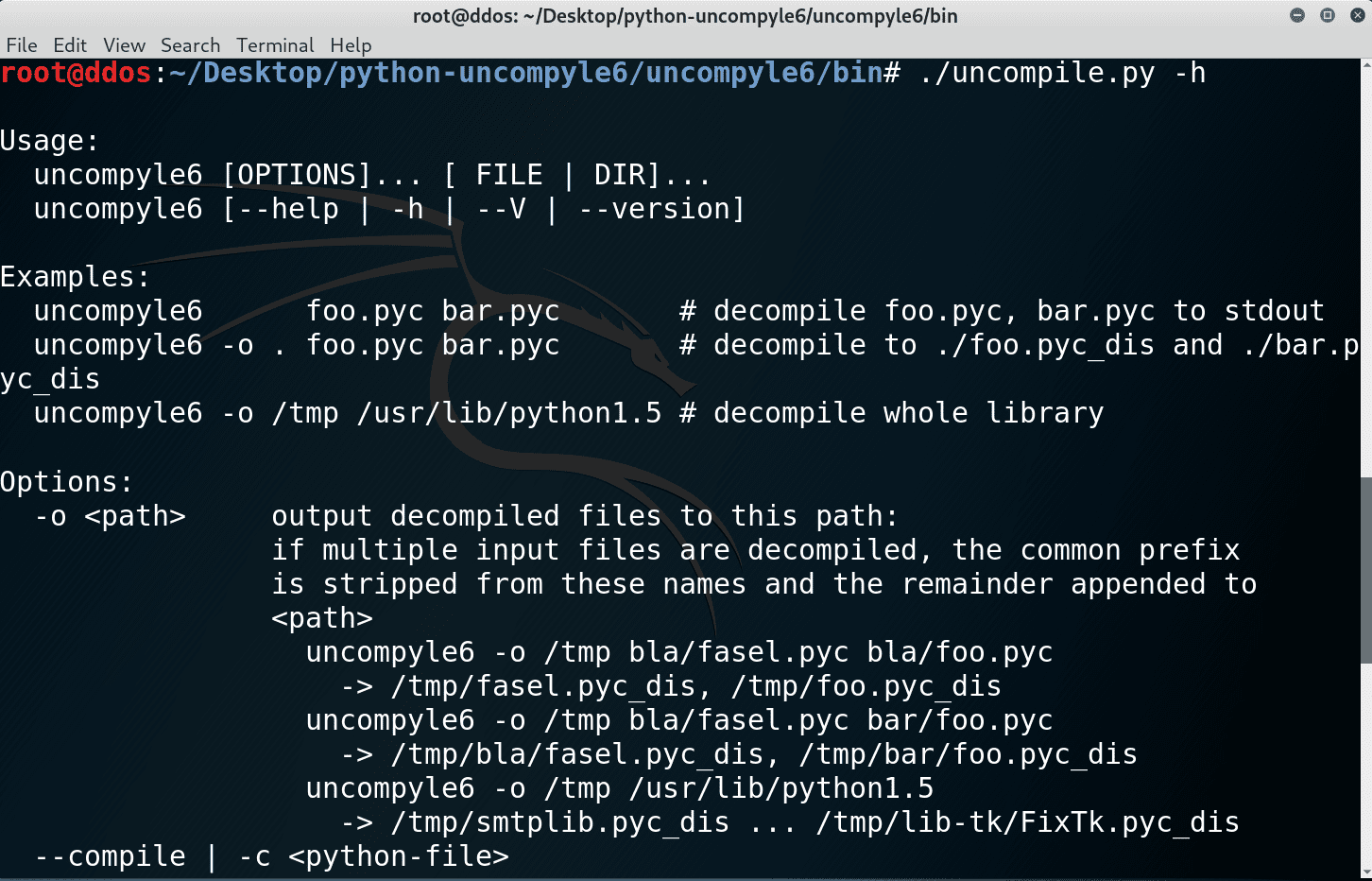
uncompyle6 A native Python cross-version decompiler and fragment decompiler. The successor to decompyle, uncompyle, and uncompyle2. Introduction uncompyle6 translates Python bytecode back into the equivalent Python source code. It accepts bytecodes from Python version...
What is TCA Tencent Cloud Code Analysis (TCA for short, code-named CodeDog inside the company early) is a code comprehensive analysis platform, which includes three components: server, web, and client. It supports the integration...
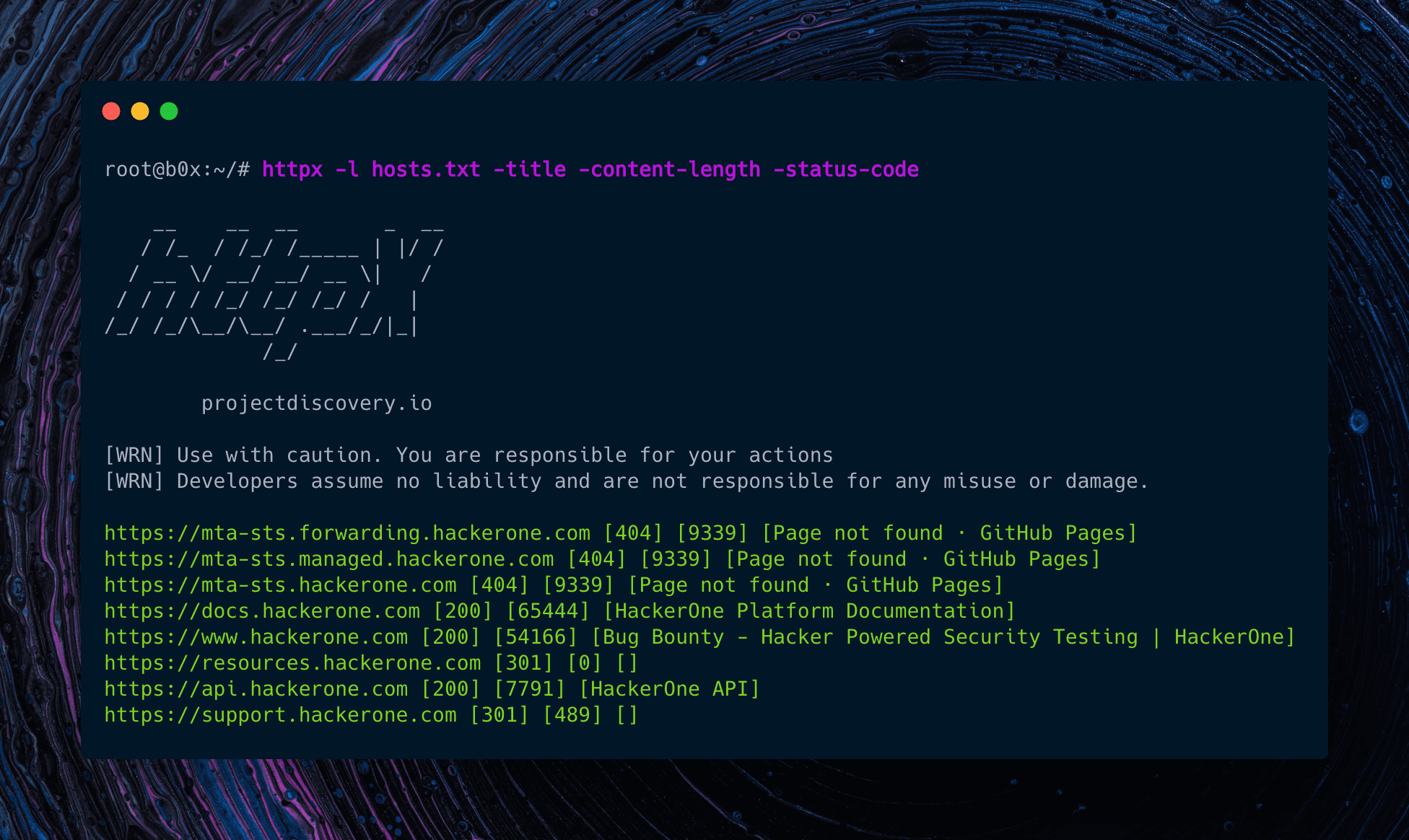
httpx httpx is a fast and multi-purpose HTTP toolkit built to support running multiple probes using a public library. Probes are specific tests or checks to gather information about web servers, URLs, or other...
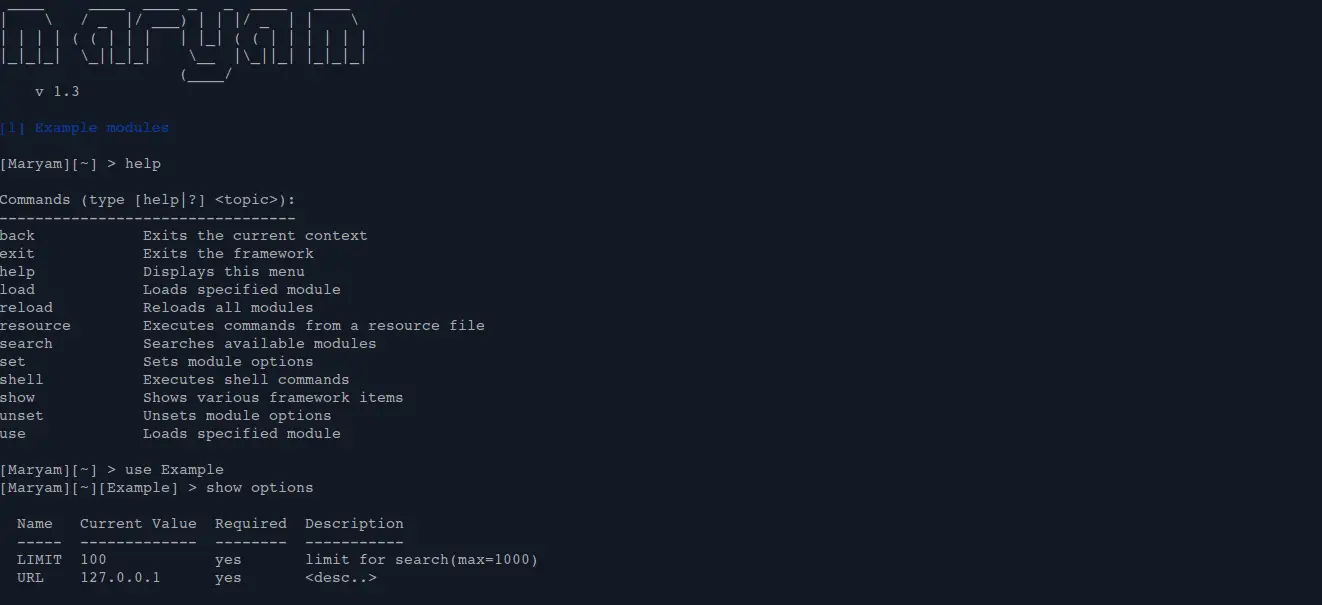
Maryam OWASP Maryam is an Open-source intelligence(OSINT) and Web-based Footprinting modular framework based on the Recon-ng core and written in Python. If you want Extracts Emails, Docs, Subdomains, Social networks from search engines Extracts Links, CSS and JS files,...
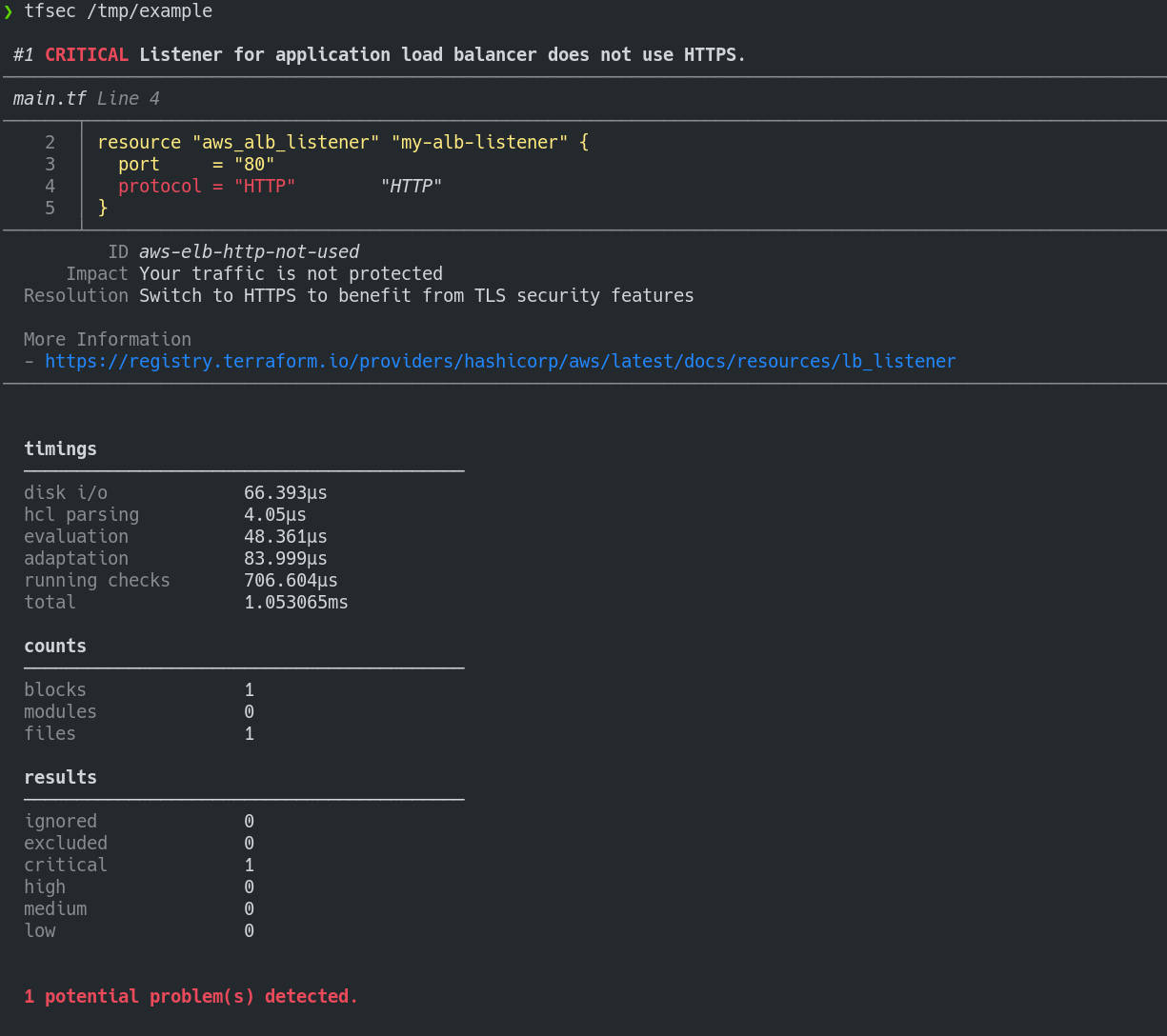
tfsec tfsec uses static analysis of your terraforms templates to spot potential security issues. Features ☁️ Checks for misconfigurations across all major (and some minor) cloud providers ⛔ Hundreds of built-in rules ? Scans...
ImHex A Hex Editor for Reverse Engineers, Programmers, and people who value their eyesight when working at 3 AM. Features Featureful hex view Byte patching Patch management Copy bytes as a feature Bytes...