Category: Open Source Tool
pwnlook Pwnlook is an offensive post exploitation tool that will give you complete control over the Outlook desktop application and therefore to the emails configured in it. What it does: List mailboxes List folders...
Pandora This is a red team tool that assists in gathering credentials from different password managers. They are separated into three categories, Windows 10 desktop applications, browsers, and browser plugins. This may work on...
Wapiti works as a “black-box” vulnerability scanner, that means it won’t study the source code of web applications but will work like a fuzzer, scanning the pages of the deployed web application, extracting links...
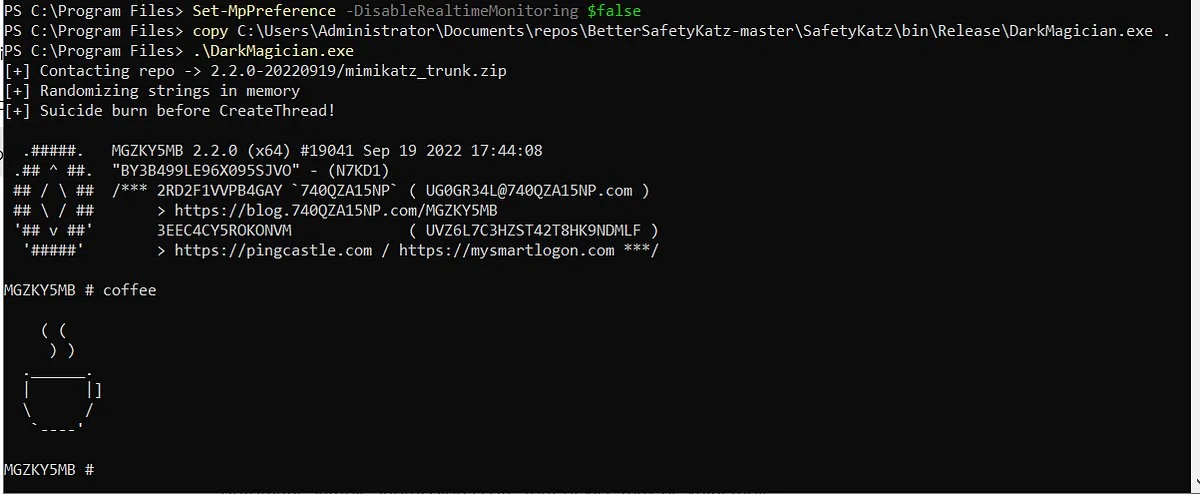
RustiveDump RustiveDump is a Rust-based tool designed to dump the memory of the lsass.exe process using only NT system calls. It creates a minimal minidump file from scratch, containing essential components like SystemInfo, ModuleList, and Memory64List, with support for XOR encryption and remote transmission....
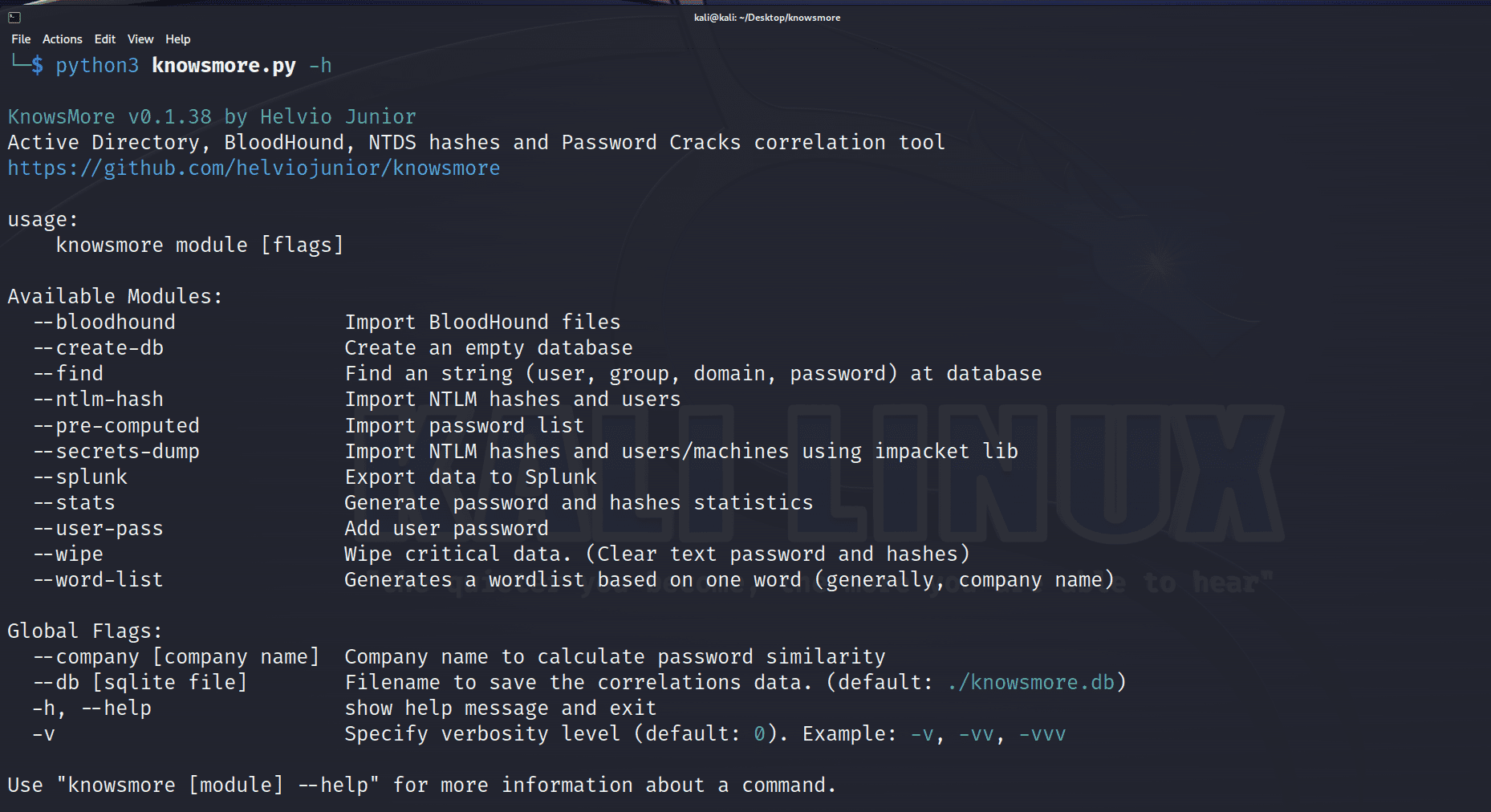
KnowsMore KnowsMore is a Swiss army knife tool for pentesting Microsoft Active Directory (NTLM Hashes, BloodHound, NTDS, and DCSync). Main features Import NTLM Hashes from .ntds output txt file (generated by CrackMapExec or secretsdump.py)...
kernel hardening checker There are plenty of Linux kernel hardening config options. A lot of them are not enabled by the major distros. We have to enable these options ourselves to make our systems...
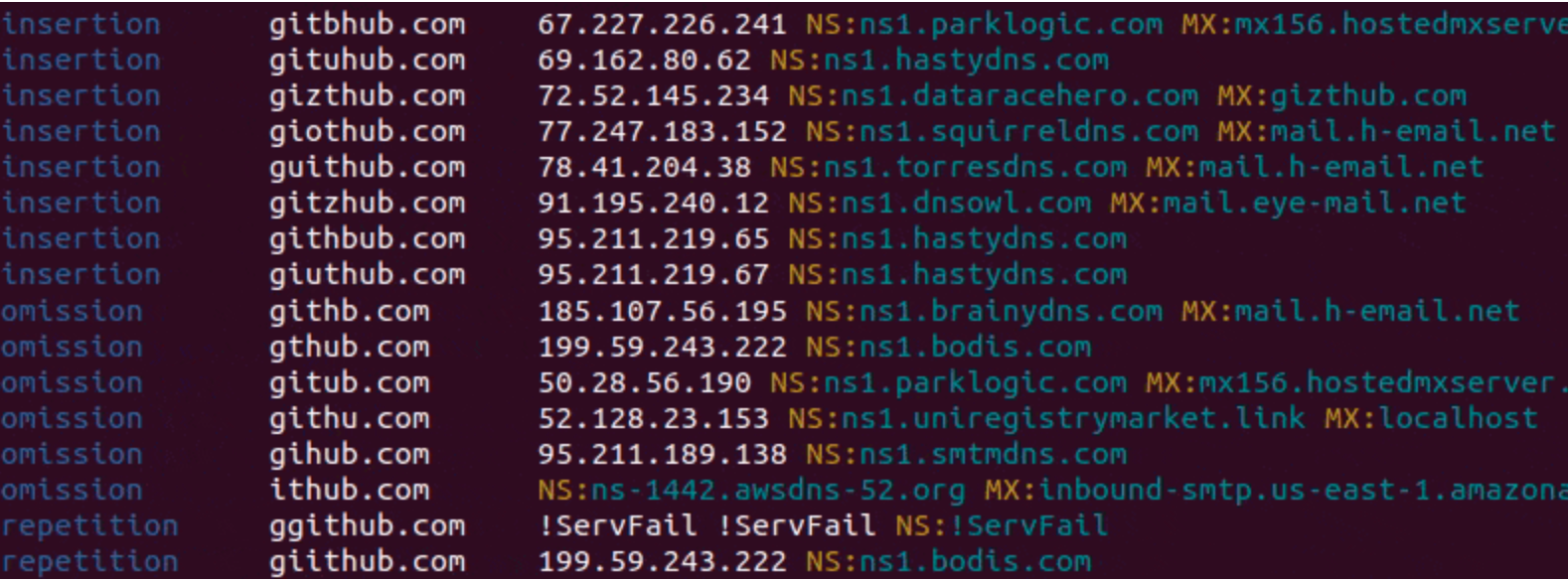
dnstwist See what sort of trouble users can get in trying to type your domain name. Find lookalike domains that adversaries can use to attack you. Can detect typosquatters, phishing attacks, fraud, and brand...
Cameradar Cameradar allows you to Detect open RTSP hosts on any accessible target host Detect which device model is streaming Launch automated dictionary attacks to get their stream route (e.g.: /live.sdp) Launch automated dictionary attacks to...
Gatekeeper What is Gatekeeper? Gatekeeper is the first open-source DoS protection system. It is designed to scale to any peak bandwidth, so it can withstand DoS attacks both today and tomorrow. In spite of...
Overview This is a tool used to exploit CRED-1 over a SOCKS5 connection (with UDP support). How CRED-1 Attack Works CRED-1 can be broken down into the following steps: Send a DHCP Request for...
Velociraptor – Endpoint visibility and collection tool. Velociraptor is a unique, advanced open-source endpoint monitoring, digital forensic, and cyber response platform. It was originally developed by DFIR professionals who needed a powerful and efficient...
IVRE IVRE is an open-source framework for network recon. It relies on open-source well-known tools (Nmap, Zmap, Masscan, Bro, and p0f) to gather data (network intelligence), stores it in a database (MongoDB), and provides tools to analyze it....
Locksmith A tool built to find and fix common misconfigurations in Active Directory Certificate Services. Installation Module Install module from the PowerShell Gallery (preferred): Open a PowerShell prompt and run Install-Module -Name...
ActivityWatch The goal of ActivityWatch is simple: Enable the collection of as many valuable lifedata as possible without compromising user privacy. What ActivityWatch is A set of watchers that record relevant information about what you...
The Firmware Analysis and Comparison Tool (FACT) Firmware analysis is a tough challenge with a lot of tasks. Many of these tasks can be automated (either with new approaches or incorporation of existing tools)...
Slhasher – Bulk VirusTotal Hash Lookups Slhasher is a collaborative tool designed to perform bulk SHA256 hash lookups through a graphical user interface. It integrates with VirusTotal to fetch hash metadata and supports exporting...