GraphQL Cop: Security Audit Utility for GraphQL
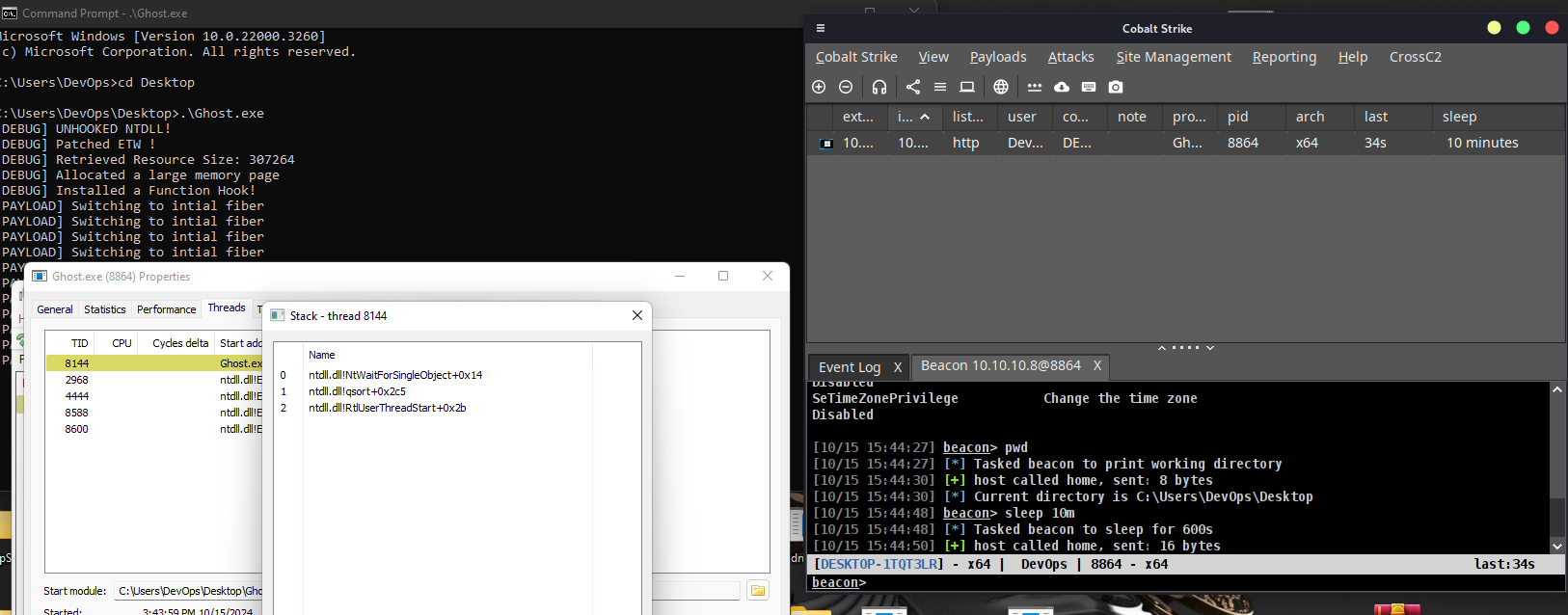
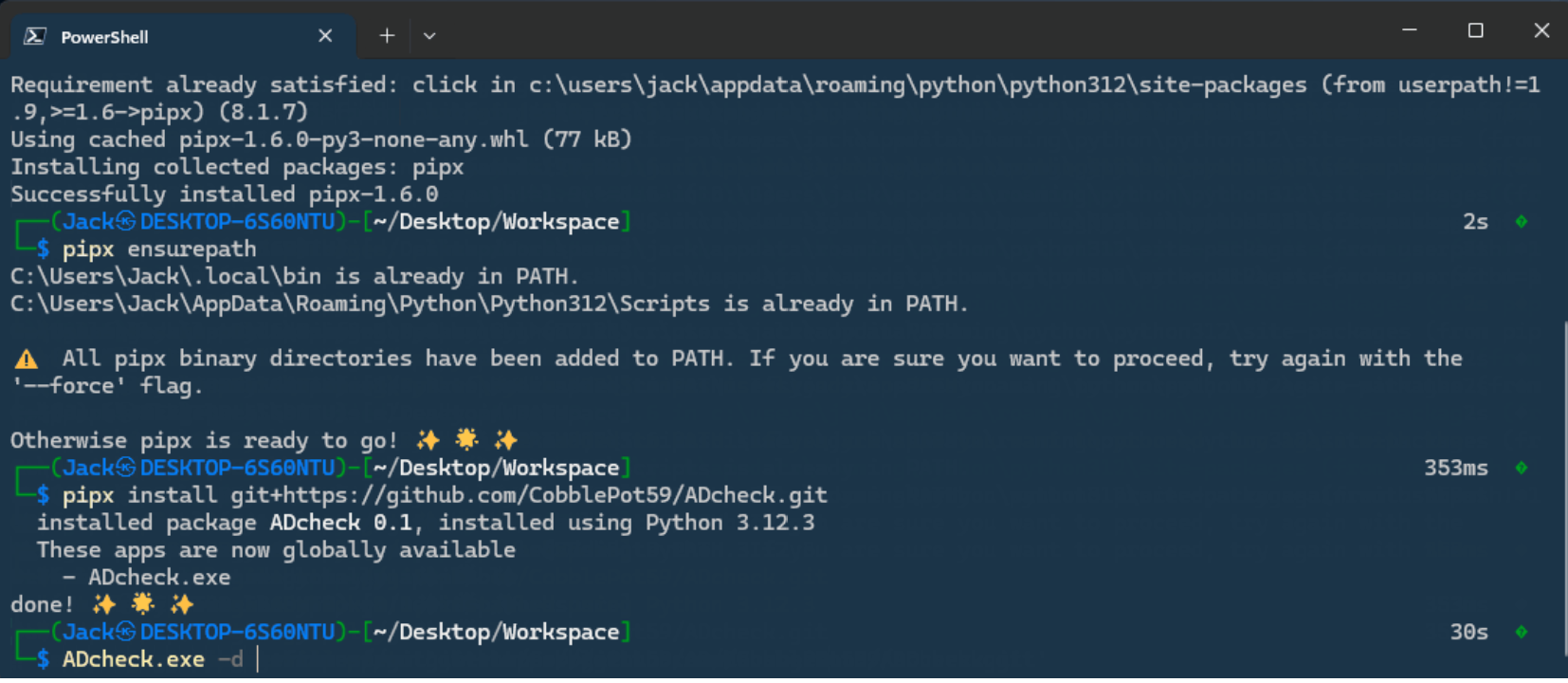
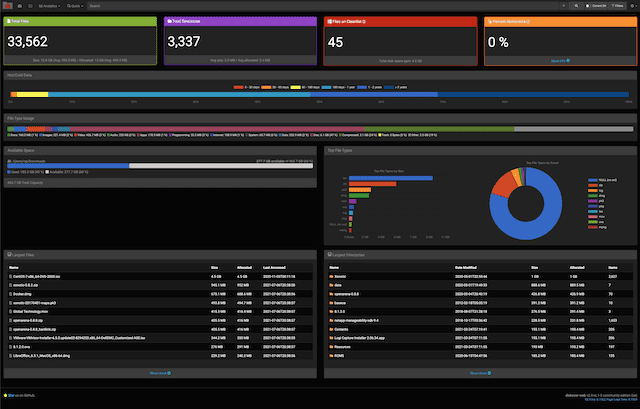
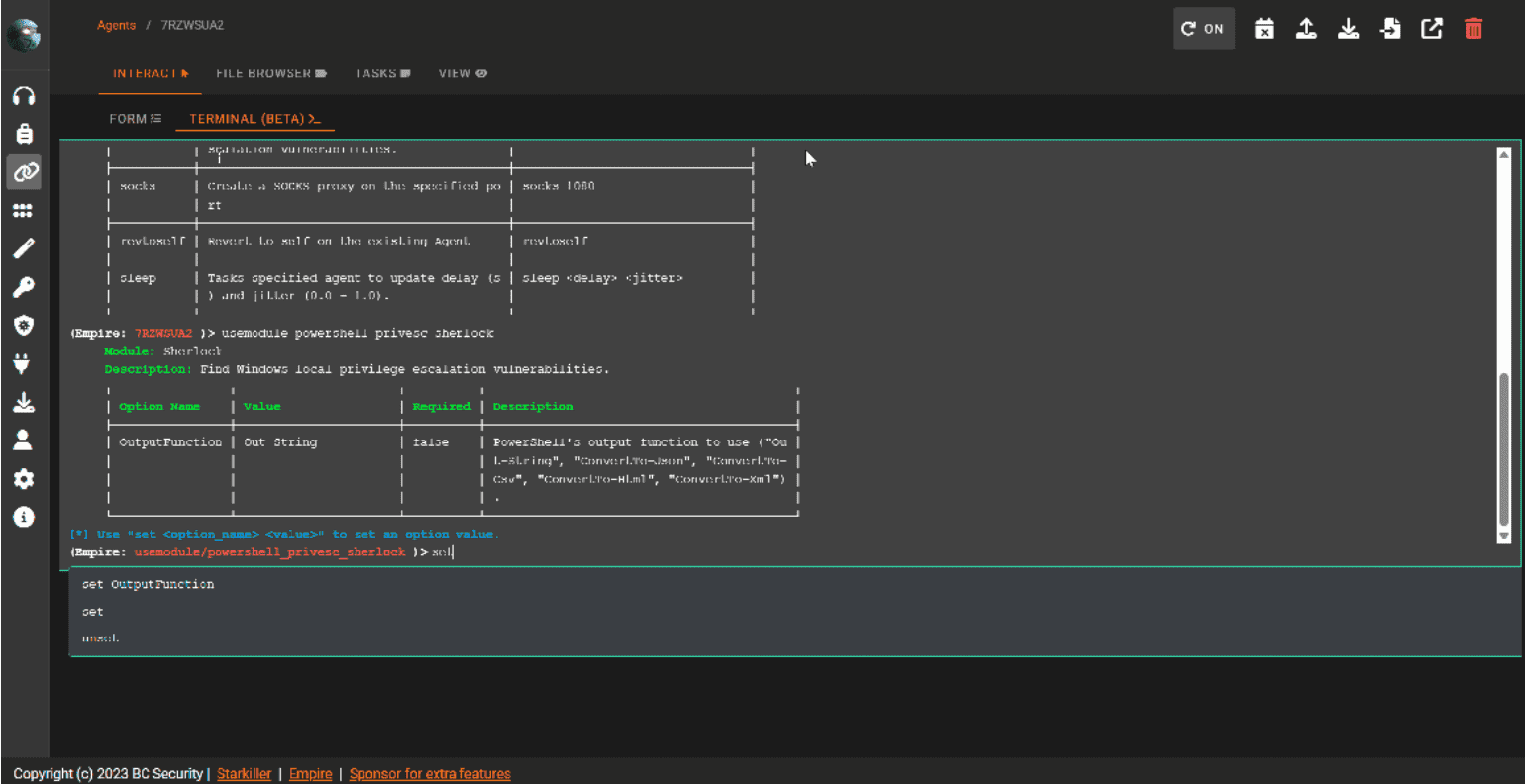
GraphQL Cop – Security Audit Utility for GraphQL GraphQL Cop is a small Python utility to run common security tests against GraphQL APIs. GraphQL Cop is perfect for running CI/CD checks in GraphQL. It...