Category: Open Source Tool
GoExec is a new take on some of the methods used to gain remote execution on Windows devices. GoExec implements a number of largely unrealized execution methods and provides significant OPSEC improvements overall. Goexec supports...
Domain Coverage Analysis Tool Tool for analyzing domain security based on various data sources: LDAP domain dump NTDS.dit dump Hashcat output List modules uv run main.py -l Available modules: – reversible_encryption – passwords_reuse –...
A lightweight, ergonomic framework for building bug bounty-ready Cybersecurity AIs (CAIs). Why CAI? The cybersecurity landscape is undergoing a dramatic transformation as AI becomes increasingly integrated into security operations. We predict that by 2028, AI-powered...
DeviceCodePhishing This is a novel technique that leverages the well-known Device Code phishing approach. It dynamically initiates the flow as soon as the victim opens the phishing link and instantly redirects them to the...
The stable release of Suricata 8.0 has officially been unveiled—a powerful open-source intrusion detection and network traffic analysis system developed by the OISF foundation. This marks the first major update in two years since...
GPOHound is a tool for dumping and analysing Group Policy Objects (GPOs) extracted from the SYSVOL share. It provides a structured, formalized format to help uncover misconfigurations, insecure settings, and privilege escalation paths in...
Apache Tomcat webshell application for RCE A webshell application and interactive shell for pentesting Apache Tomcat servers. Features Webshell plugin for Apache Tomcat. Execute system commands via an API with ?action=exec. Download files from the...
Gallia Gallia is an extendable pentesting framework with the focus on the automotive domain. The scope of the toolchain is conducting penetration tests from a single ECU up to whole cars, with the main...
Whether you’re a developer, security engineer, or just a curious person, Cloud Snitch is guaranteed to teach you something and take your relationship with your cloud to the next level. Cloud Snitch provides a...
Nimhawk is an advanced command and control (C2) framework that builds upon the exceptional foundation laid by Cas van Cooten (@chvancooten) with his NimPlant project. Cas’s innovative work in developing a lightweight implant written in Nim has been...
DreamWalkers Reflective shellcode loader inspired by MemoryModule and Donut, with advanced call stack spoofing and .NET support. Unlike traditional call stack spoofing, which often fails within reflectively loaded modules due to missing unwind metadata, DreamWalkers introduces a...
Corporate laptops and production servers typically have robust security monitoring in place to reduce risk and meet compliance requirements. However, CI/CD runners, which handle sensitive information like secrets for cloud environments and create production...
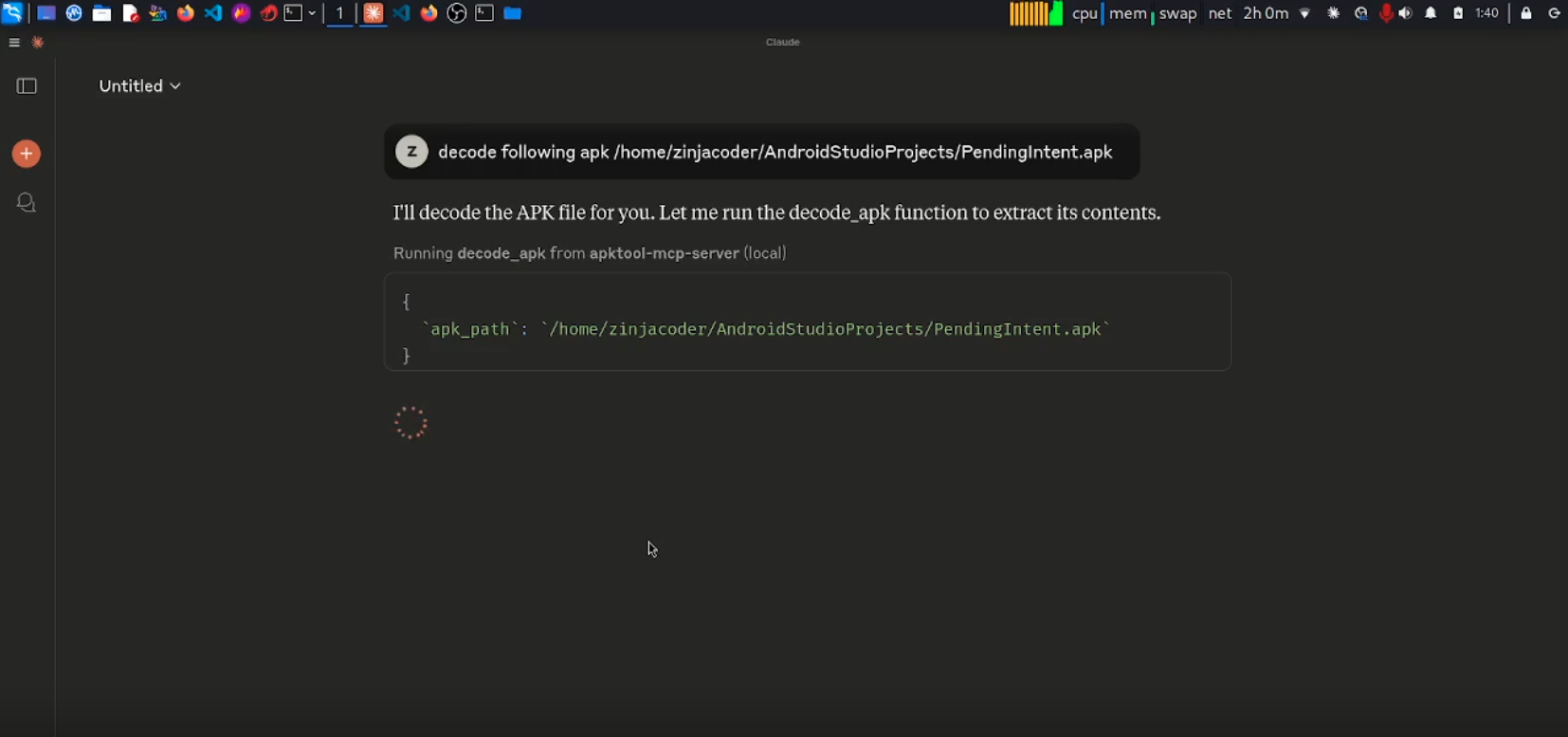
Fully automated MCP server built on top of apktool to analyze Android APKs using LLMs like Claude — uncover vulnerabilities, parse manifests, and reverse engineer effortlessly. apktool-mcp-server is a MCP server for the Apk Tool that integrates...
The Damn Vulnerable Model Context Protocol (DVMCP) is an educational project designed to demonstrate security vulnerabilities in MCP implementations. It contains 10 challenges of increasing difficulty that showcase different types of vulnerabilities and attack...
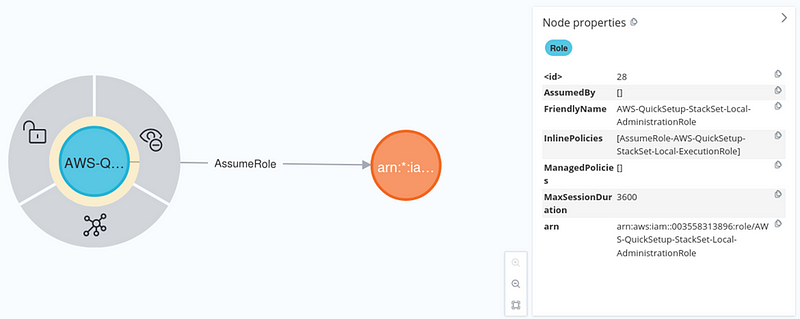
Perhaps the most critical component of an AWS infrastructure is the policy document describing the actions allowed or denied to a resource. IAM can become a messy kitchen as misconfigurations will introduce gaps in...
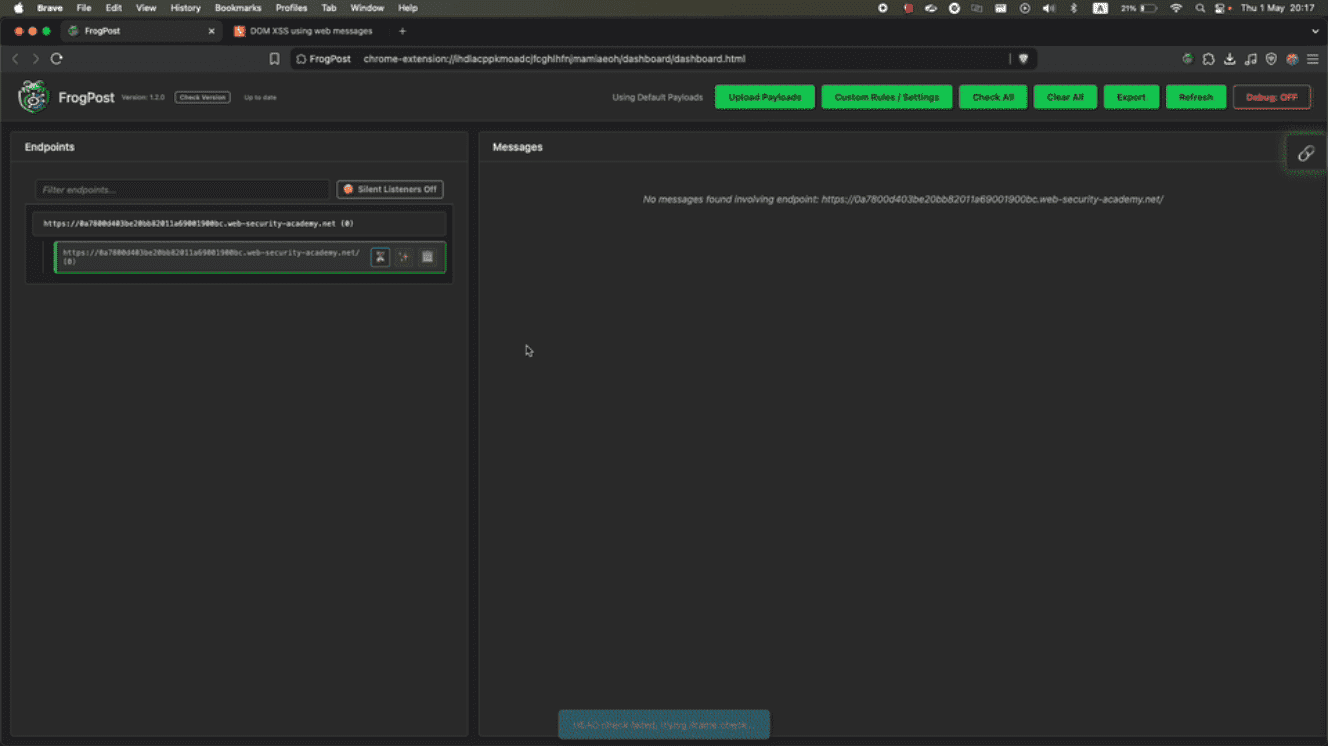
FrogPost is a powerful Chrome extension for testing and analyzing the security of postMessage communications between iframes. It helps developers and security professionals identify vulnerabilities in message-handling implementations. Key Features Live monitor of cross-origin postMessage traffic Automatic detection...