Category: Open Source Tool
Hunt-Sleeping-Beacons This project is ( mostly ) a callstack scanner which tries to identify IOCs indicating an unpacked or injected C2 agent. All checks are based on the observation that C2 agents wait between...
AlphaGolang AlphaGolang is a collection of IDAPython scripts to help malware reverse engineers master Go binaries. The idea is to break the scripts into concrete steps, thus avoiding brittle monolithic scripts, and mimicking the...
Malduck Malduck is your ducky companion in malware analysis journeys. It is mostly based on the Roach project, which derives many concepts from mlib library created by Maciej Kotowicz. The purpose of the fork was to make Roach...
Vermilion Vermilion is a simple and lightweight CLI tool designed for rapid collection, and optional exfiltration of sensitive information from Linux systems. Its primary purpose is to streamline the process of gathering critical data...
Protect Loader Protect Loader is a shellcode loader written in pure golang designed to provide various security and evasion techniques for Go applications. It includes features such as shellcode loading, obfuscation, the use of...
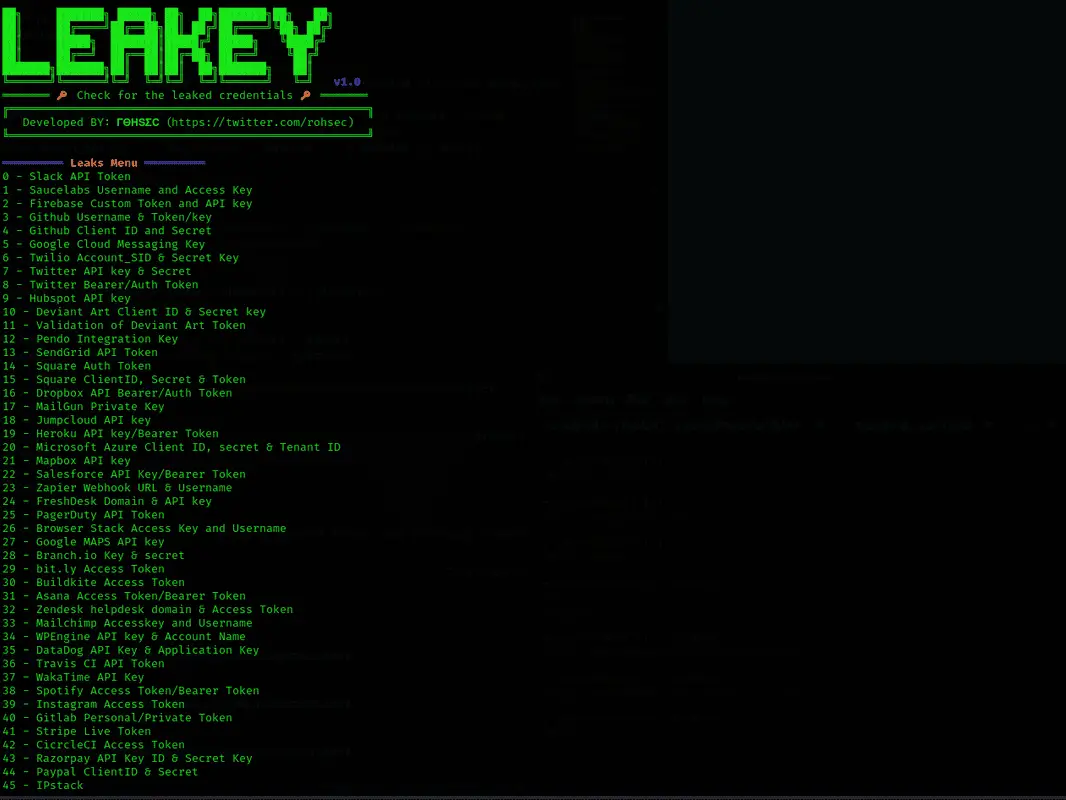
LEAKEY LEAKEY is a tool for validation of leaked API tokens/keys found during pentesting and Red Team Engagements. The script is really useful for Bug Hunters in order to validate and determine the impact...
BREAD BREAD (BIOS Reverse Engineering & Advanced Debugging) is an ‘injectable’ real-mode x86 debugger that can debug arbitrary real-mode code (on real HW) from another PC via serial cable. BREAD emerged from many failed...
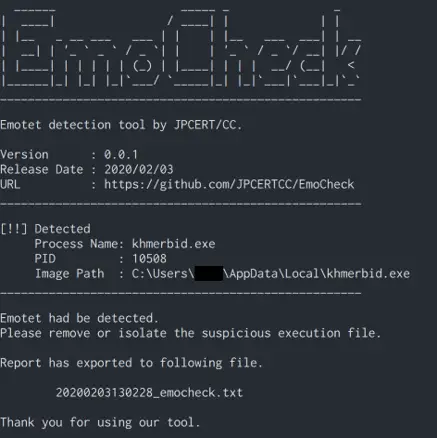
EmoCheck Emotet detection tool for Windows OS. How EmoCheck detects Emotet (v0.0.1) Emotet generates their process name from a specific word dictionary and C drive serial number. EmoCheck scans the running process on the...
HellBunny The purpose of this research project was to develop a comprehensive understanding of the architecture and internals of the Windows operating system, including the Native API, the Process and Thread Environment Block, and...
AWS Threat Detection with Stratus Red Team This repository is a documentation of my adventures with Stratus Red Team – a tool for adversary emulation for the cloud. Stratus Red Team is “Atomic Red Team for the...
drozer drozer is a security testing framework for Android. drozer allows you to search for security vulnerabilities in apps and devices by assuming the role of an app and interacting with the Android Runtime,...
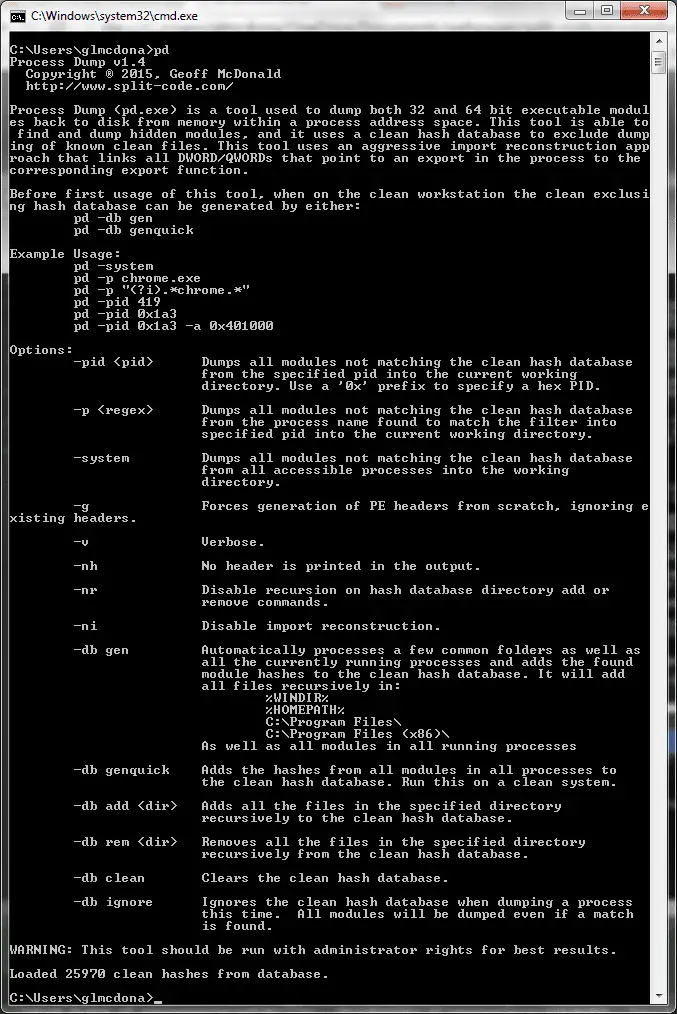
Process Dump Process Dump is a Windows reverse-engineering command-line tool to dump malware memory components back to disk for analysis. Often malware files are packed and obfuscated before they are executed in order to...
GraphStrike GraphStrike is a suite of tools that enables Cobalt Strike’s HTTPS Beacon to use Microsoft Graph API for C2 communications. All Beacon traffic will be transmitted via two files created in the attacker’s SharePoint site,...
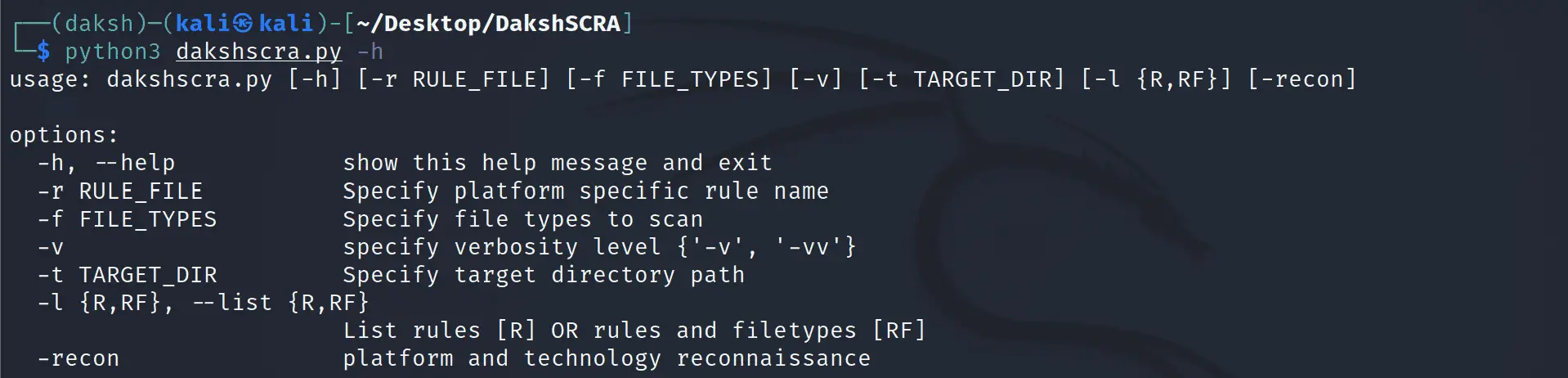
Daksh SCRA (Source Code Review Assist) Daksh SCRA (Source Code Review Assist) tool is built to enhance the efficiency of the source code review process, providing a well-structured and organized approach for code reviewers....
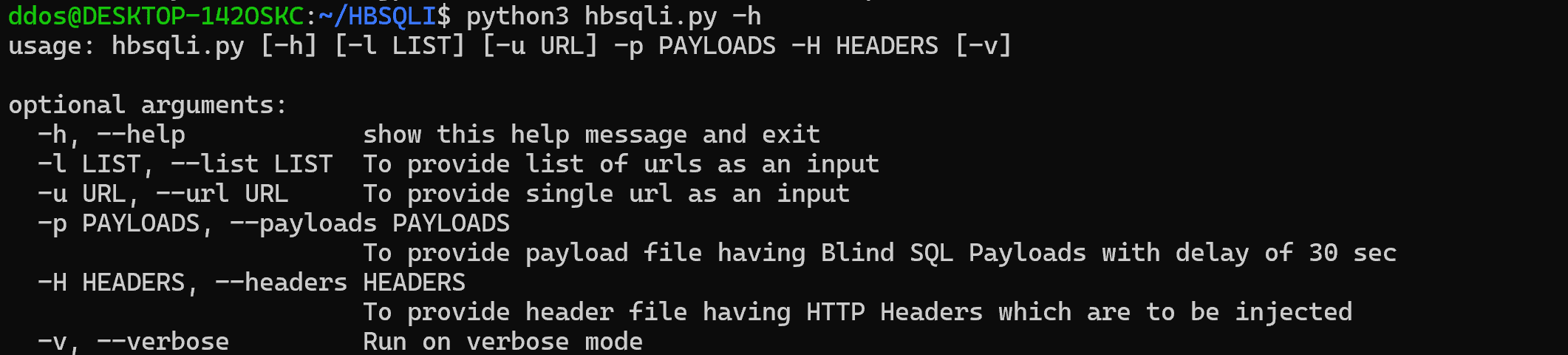
HBSQLI: Automated Tester For Header-Based Blind SQL Injection HBSQLI is an automated command-line tool for performing Header Based Blind SQL injection attacks on web applications. It automates the process of detecting Header Based Blind...
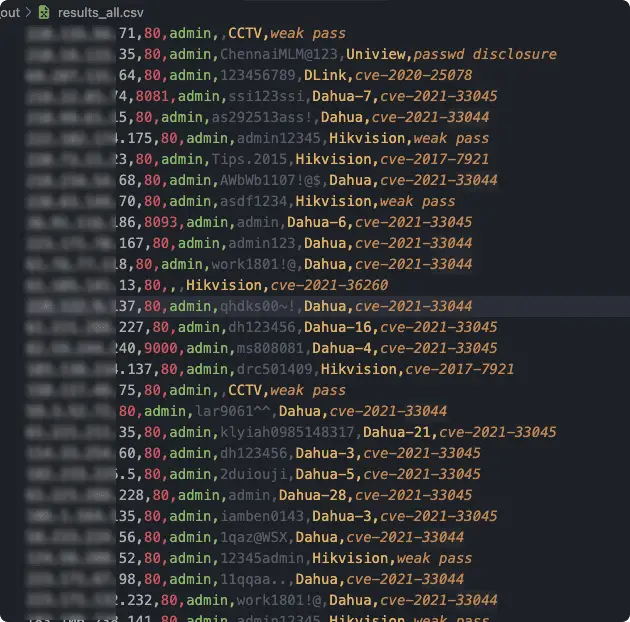
Ingram This is a webcam device vulnerability scanning tool, that already supports Hikvision, Dahua, and other devices. Installation Firstly, clone this repo: git clone https://github.com/jorhelp/Ingram.git Then, go to the repo dir, create a virtual...