Category: Open Source Tool
GAP This is an evolution of the original getAllParams extension for Burp. Not only does it find more potential parameters for you to investigate, but it also finds potential links to try these parameters...
HAWK What Hawk is and isn’t Hawk provides a Limited analysis of the gathered data. This is by design! Hawk is here to help get all of the data in a single place it...
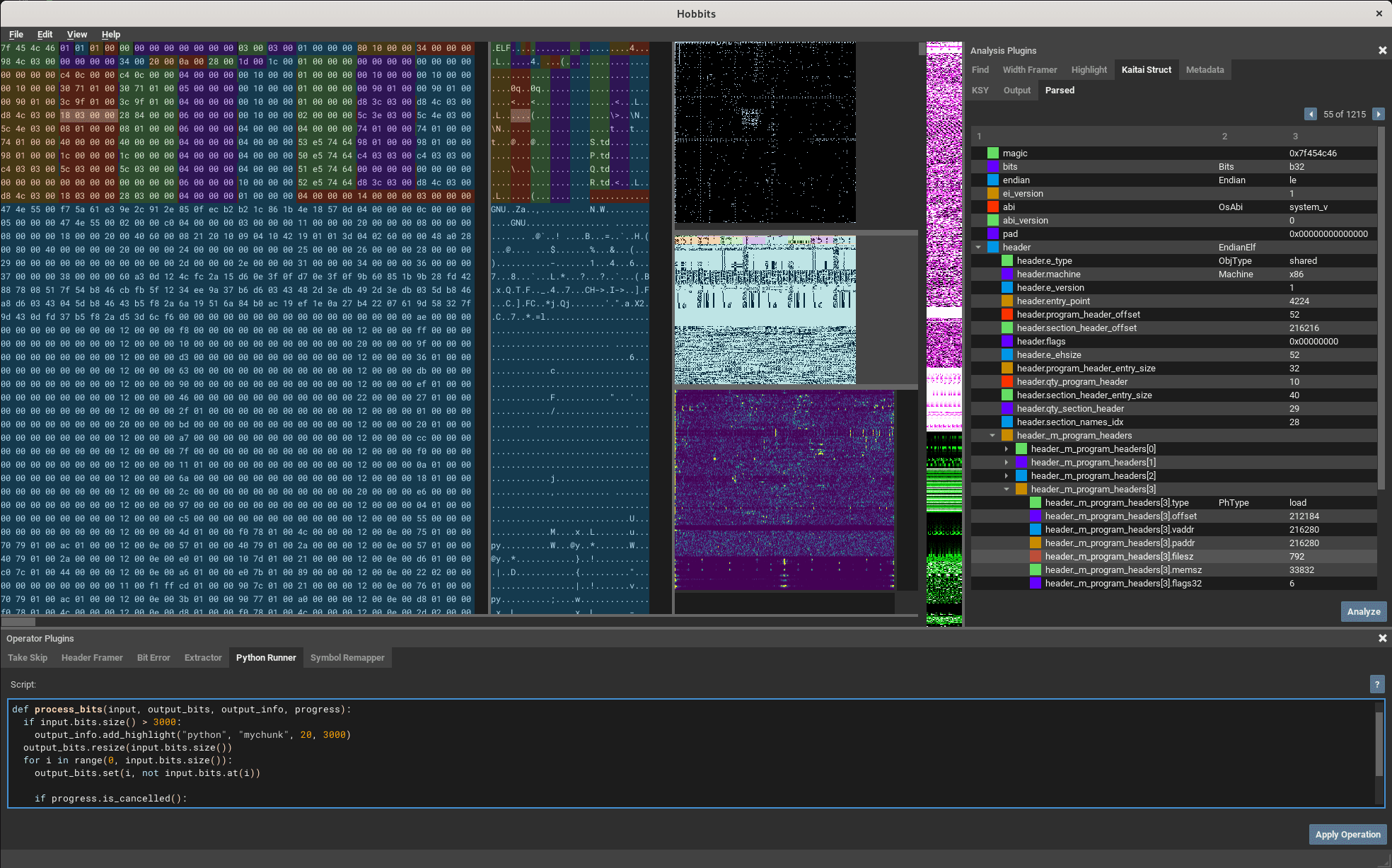
Hobbits Hobbits is a software platform for analyzing, processing and visualizing bits. The Hobbits GUI is the central tool of the platform and will be the primary focus of this document. The Hobbits Runner...
Nemesis Nemesis is an offensive data enrichment pipeline and operator support system. Built on Kubernetes with scale in mind, our goal with Nemesis was to create a centralized data processing platform that ingests data...
Shellz A script for generating common reverse shells fast and easy. Especially nice when in need of PowerShell and Python reverse shells, which can be a PITA getting correctly formatted. PowerShell revshells Shows username@computer.(domain),...
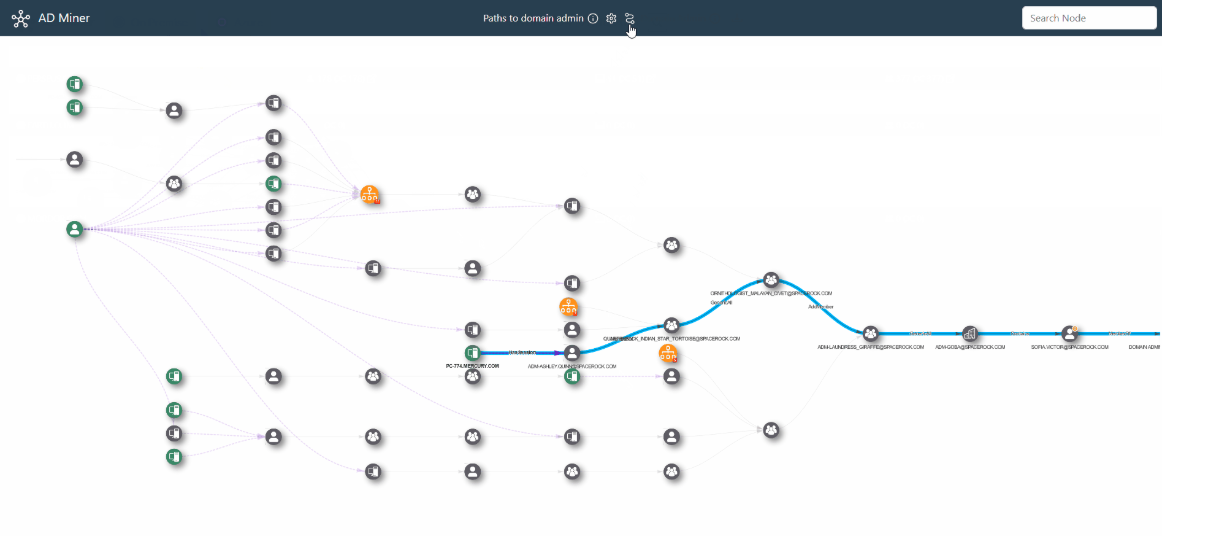
ADMiner ADMiner is an Active Directory audit tool that leverages cypher queries to crunch data from the BloodHound graph database (neo4j) and gives you a global overview of existing weaknesses through a web-based static report, including...
Threagile Agile Threat Modeling Toolkit Threagile is an open-source toolkit for agile threat modeling: It allows to model architecture with its assets in an agile fashion as a YAML file directly inside the IDE. Upon...
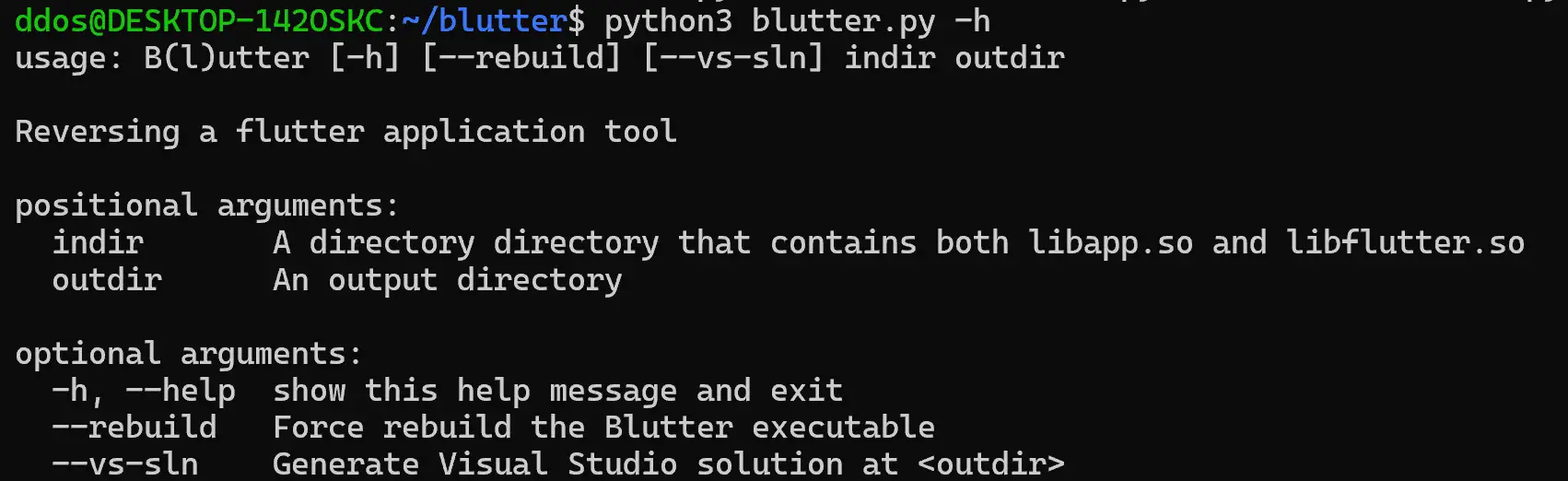
B(l)utter Flutter Mobile Application Reverse Engineering Tool by Compiling Dart AOT Runtime Currently, the application supports only Android libapp.so. Also, the application currently works only against recent Dart versions. Install This application uses the...
Supernova Supernova is an open-source tool that empowers users to securely encrypt and/or obfuscate their raw shellcode.Supernova supports various features beyond those typically found in a common shellcode encryptor tool. Features Supernova offers automatic...
Kerbeus-BOF Beacon Object Files for Kerberos abuse. This is an implementation of some important features of the Rubeus project, written in C. The project features integration with the C2 frameworks Cobalt Strike and Havoc. Download git clone https://github.com/RalfHacker/Kerbeus-BOF.git Use...
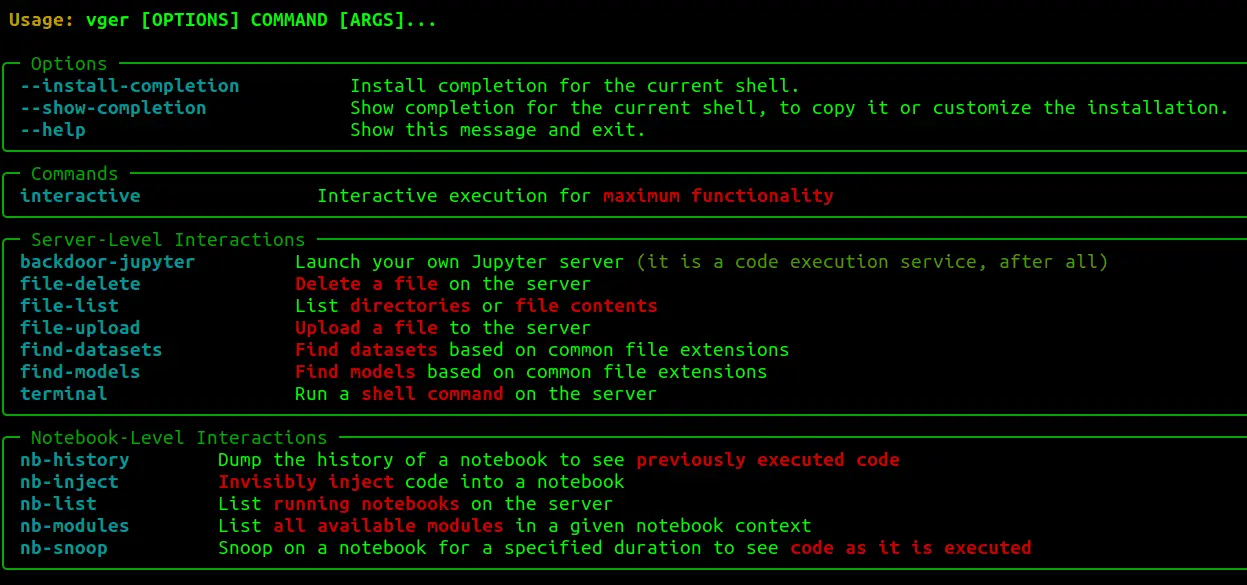
V’ger V’ger is an interactive command-line application for post-exploitation of authenticated Jupyter instances with a focus on AI/ML security operations. User Stories As a Red Teamer, you’ve found Jupyter credentials, but don’t know what you...
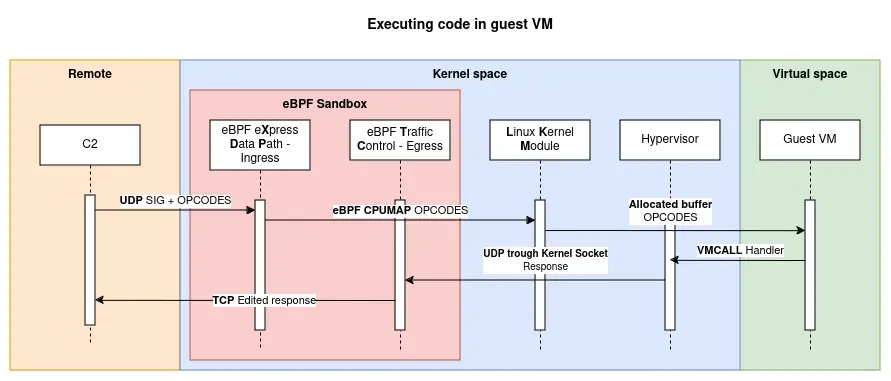
blackpill A Linux kernel rootkit in Rust using a custom made type-2 hypervisor, eBPF XDP and TC programs Features The rootkit is composed of multiple modules (talking about Rust modules, not kernel modules): defense...
AI Exploits The AI world has a security problem and it’s not just in the inputs given to LLMs such as ChatGPT. Based on research done by Protect AI and independent security experts on the Huntr Bug...
Obfu[DE]scate Obfu[DE]scate is a Python tool designed to simplify the process of de-obfuscating and comparing two versions of an Android APK – even if the functions have been renamed as part of obfuscation. With...
AutoTimeliner Automagically extract forensic timeline from volatile memory dumps. How it works AutoTimeline automates this workflow: Identify the correct volatility profile for the memory image. Runs the timeliner plugin against volatile memory dump using volatility. Runs the mftparser volatility...
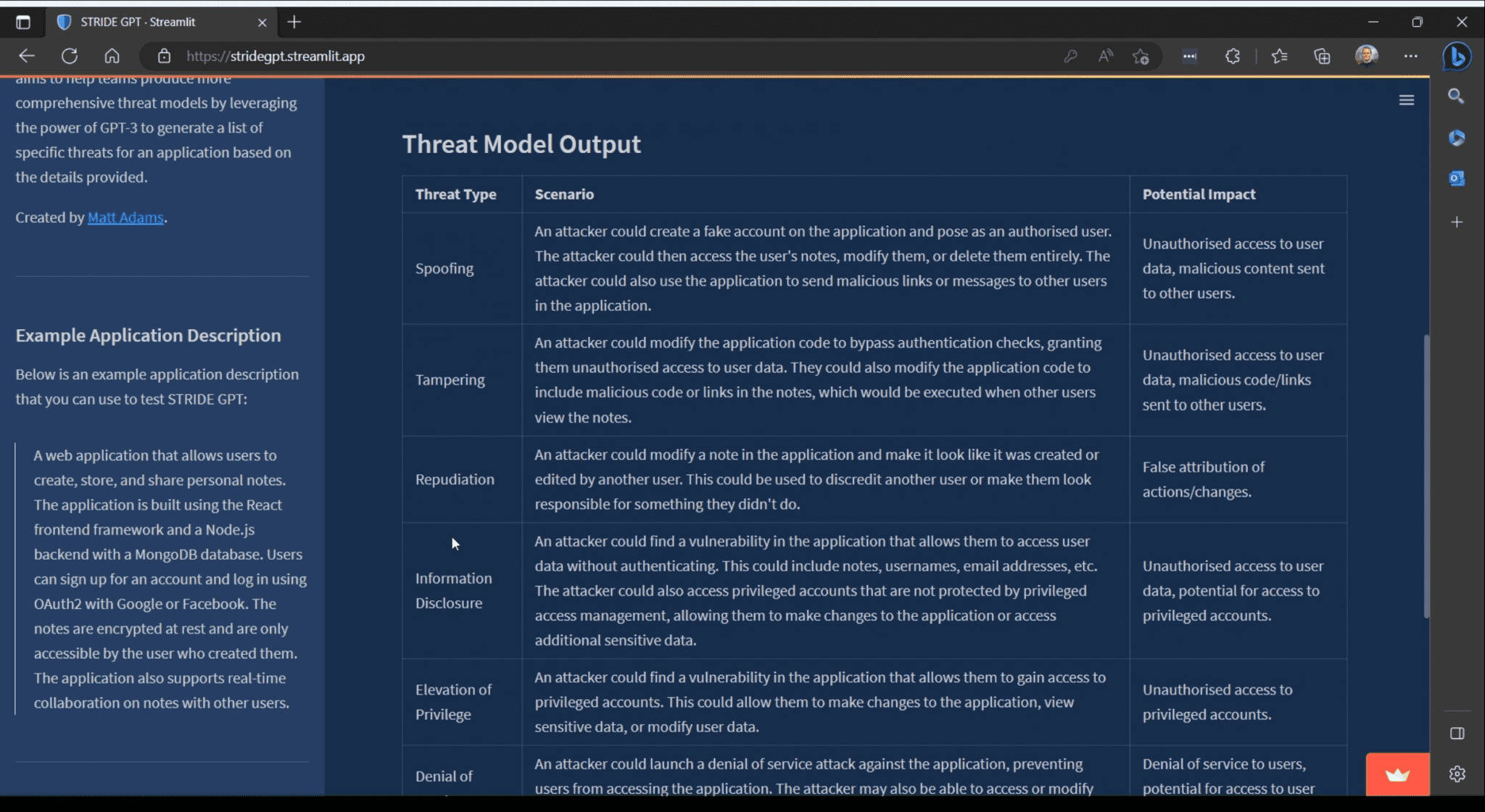
STRIDE GPT STRIDE GPT is an AI-powered threat modeling tool that leverages OpenAI’s GPT models to generate threat models and attack trees for a given application based on the STRIDE methodology. Users provide application...