Fennec: Artifact collection tool for *nix systems
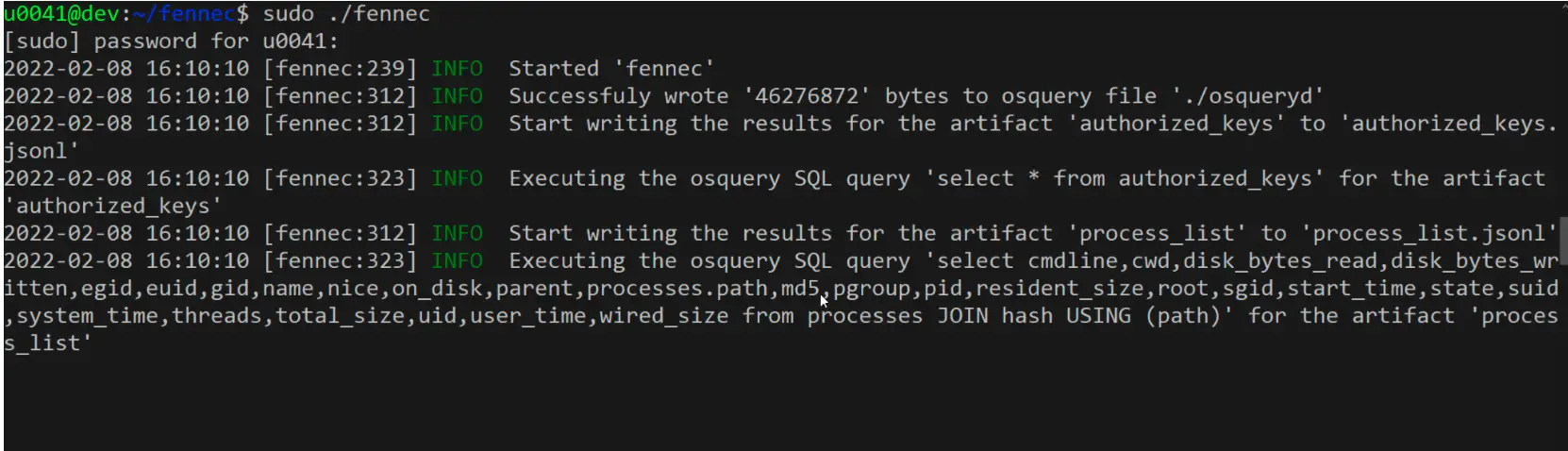
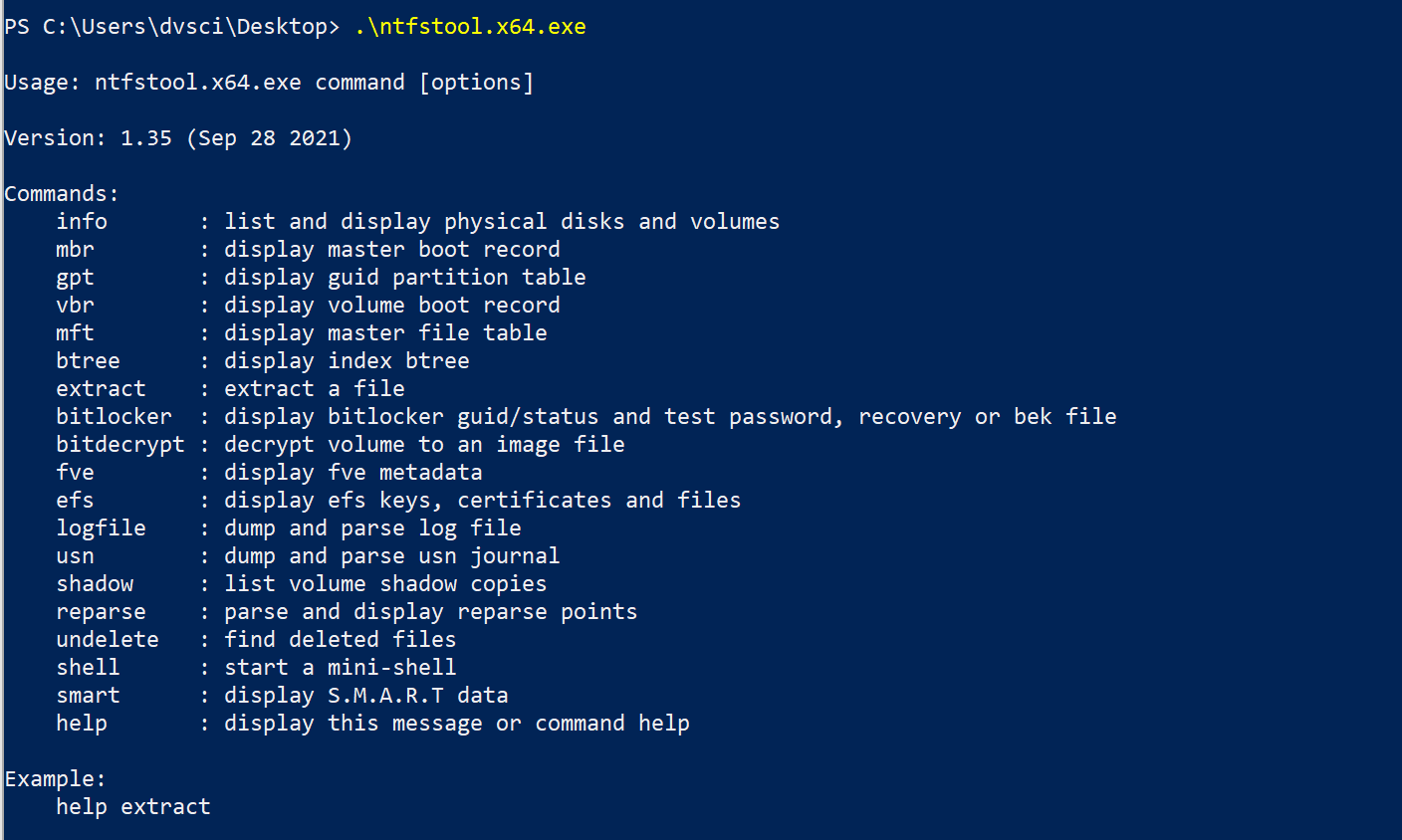
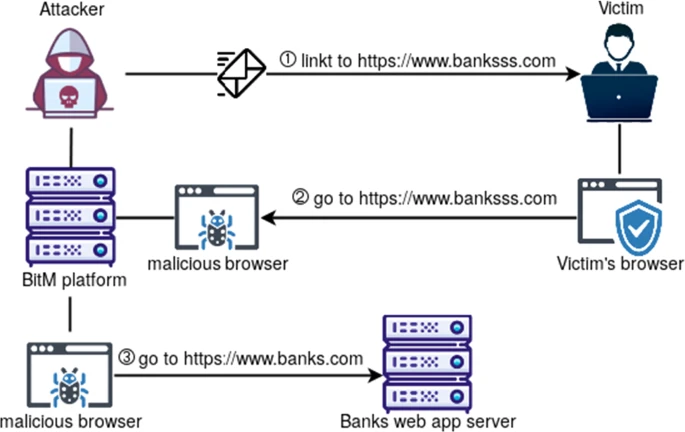
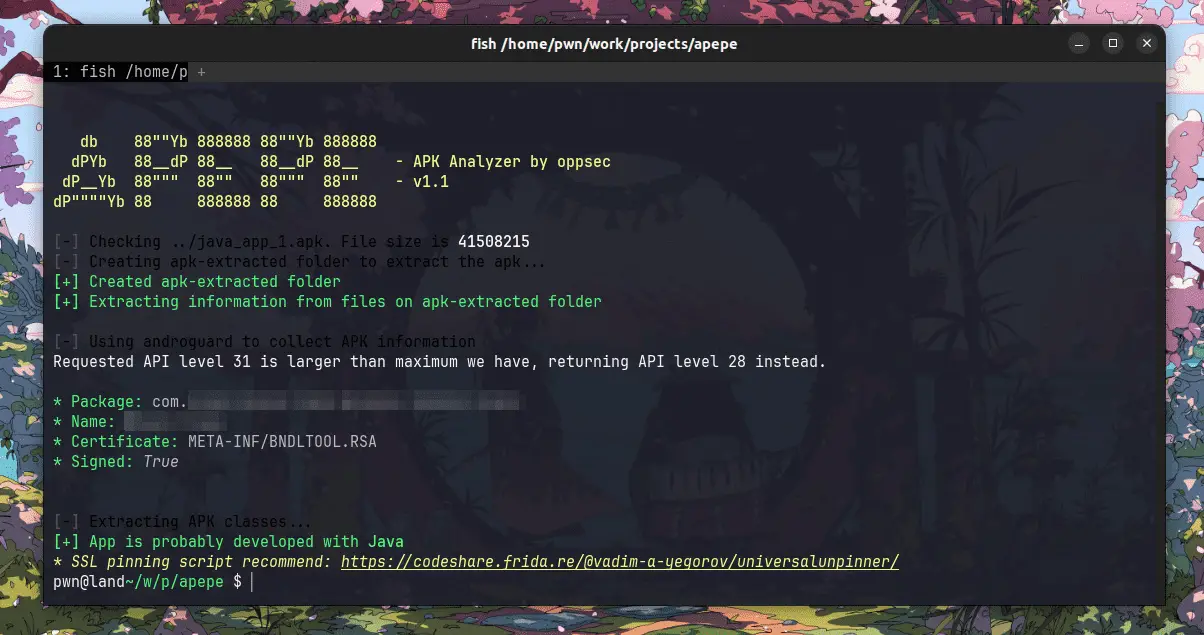
Fennec fennec is an artifact collection tool written in Rust to be used during an incident response on *nix based systems. fennec allows you to write a configuration file that contains how to collect...