catalyst: automate alert handling and incident response processes
Catalyst
Catalyst is an incident response platform or SOAR (Security Orchestration, Automation, and Response) system. It can help you to automate your alert handling and incident response procedures.
Features
Ticket (Alert & Incident) Management

Tickets are the core of Catalyst. They represent alerts, incidents, forensics investigations, threat hunts, or any other event you want to handle in your organisation.
Ticket Templates

Templates define the custom information for tickets. The core information for tickets like title, creation date, or closing status is kept quite minimal and other information like criticality, description, or MITRE ATT&CK information can be added individually.
Conditional Custom Fields

Custom Fields can be dependent on each other. So if you, for example, choose “malware” as an incident type a custom field asks you to define it further as ransomware, worm, etc. which a “phishing” incident would ask for the number of received mails in that campaign.
Playbooks

Playbooks represent processes that can be attached to tickets. Playbooks can contain manual and automated tasks. Complex workflows with different workflow branches, parallel tasks, and task dependencies can be modeled.
Automation
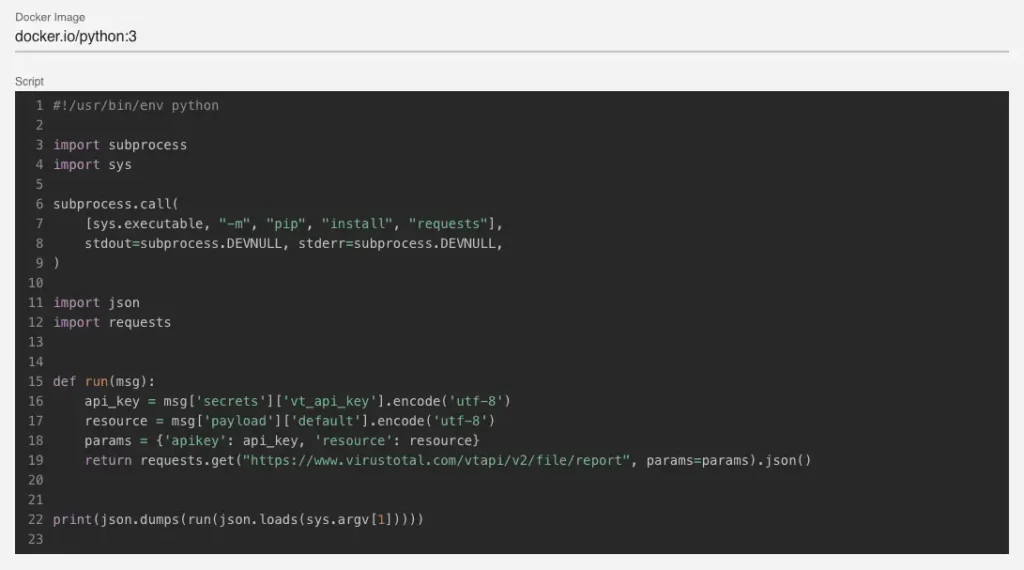
Automations are scripts that automate tasks or enrich artifacts. Automations are run in their own Docker containers. This enables them to be created in different scripting languages and run securely in their own environment.
Users

Catalyst has two different types of users, normal users accessing the platform via OIDC authentication and API keys for an external script. A fine-grained access model is available for both types and allows to define of possible actions for each user.
Install & Use
Copyright (c) 2021-present Jonas Plum





