BLOODALCHEMY Malware Targets Asian Governments
New cyber threats often result from the evolution and modification of existing malware. Recent research has revealed that the new malware BLOODALCHEMY, used in attacks on government organizations in South and Southeast Asia, is closely linked to well-known threats such as Deed RAT, ShadowPad, and PlugX.
“The origin of BloodAlchemy and Deed RAT is ShadowPad and given the history of ShadowPad being utilized in numerous APT campaigns, it is crucial to pay special attention to the usage trend of this malware,” noted the Japanese cybersecurity company ITOCHU Cyber & Intelligence.
The infection flow of BloodAlchemy
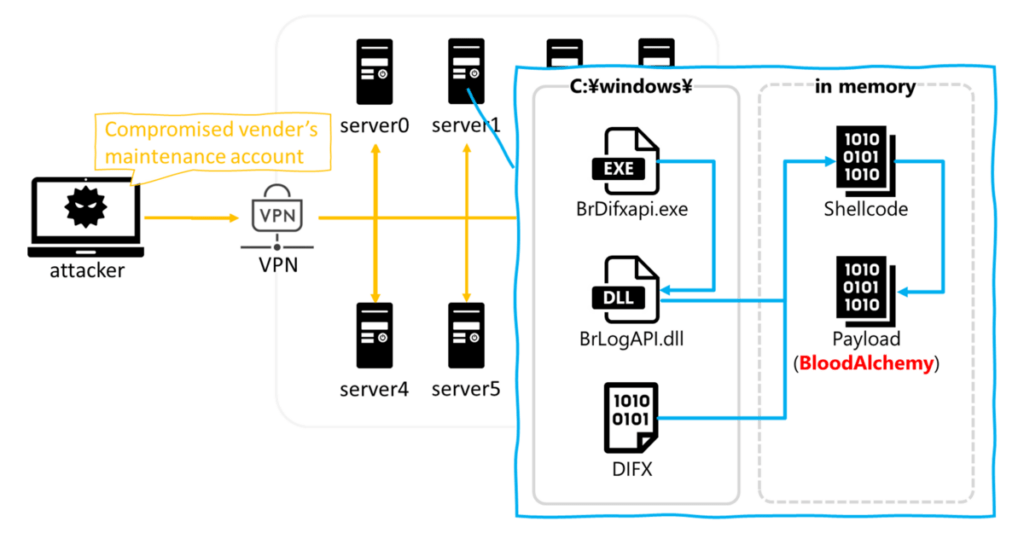
The BLOODALCHEMY malware was first documented by researchers at Elastic Security Labs in October 2023, when they investigated a malicious campaign targeting ASEAN countries. This malware, a C-based backdoor, is embedded into the signed benign process “BrDifxapi.exe” using the DLL Sideloading technique.
“While unconfirmed, the presence of so few effective commands indicates that the malware may be a subfeature of a larger intrusion set or malware package, still in development, or an extremely focused piece of malware for a specific tactical usage,” remarked Elastic researchers in their report from last year.
Attacks using BLOODALCHEMY involve compromising an account on a VPN device for initial access and uploading “BrDifxapi.exe,” which is then used to load “BrLogAPI.dll.” This loader executes BLOODALCHEMY code in memory after extracting it from a file named “DIFX.”
The malware employs a special operational mode to evade sandbox analysis, maintain persistence in the system, establish contact with the attackers’ server, and control the infected device via remote commands.
As previously noted, ITOCHU’s analysis revealed code similarities between BLOODALCHEMY and Deed RAT, a multifunctional malware previously used by the hacker group Space Pirates. Deed RAT is considered a subsequent iteration of ShadowPad, which itself is an evolution of PlugX.
“The first notable similarity is the unique payload header data structures in BLOODALCHEMY and Deed RAT,” explained ITOCHU. “There were also similarities in the code loading process and the DLL file used for its execution.”
It is worth noting that both PlugX (Korplug) and ShadowPad (PoisonPlug) have been extensively used by Chinese hacker groups for many years.
This information emerges amid the expanding activities of the Chinese hacker group Sharp Panda (also known as Sharp Dragon), which has begun targeting government organizations in Africa and the Caribbean as part of an ongoing cyber-espionage campaign.





