SharePoint Under Siege: China-Linked Storm-2603 Unleashes Warlock Ransomware After Zero-Day Exploitation
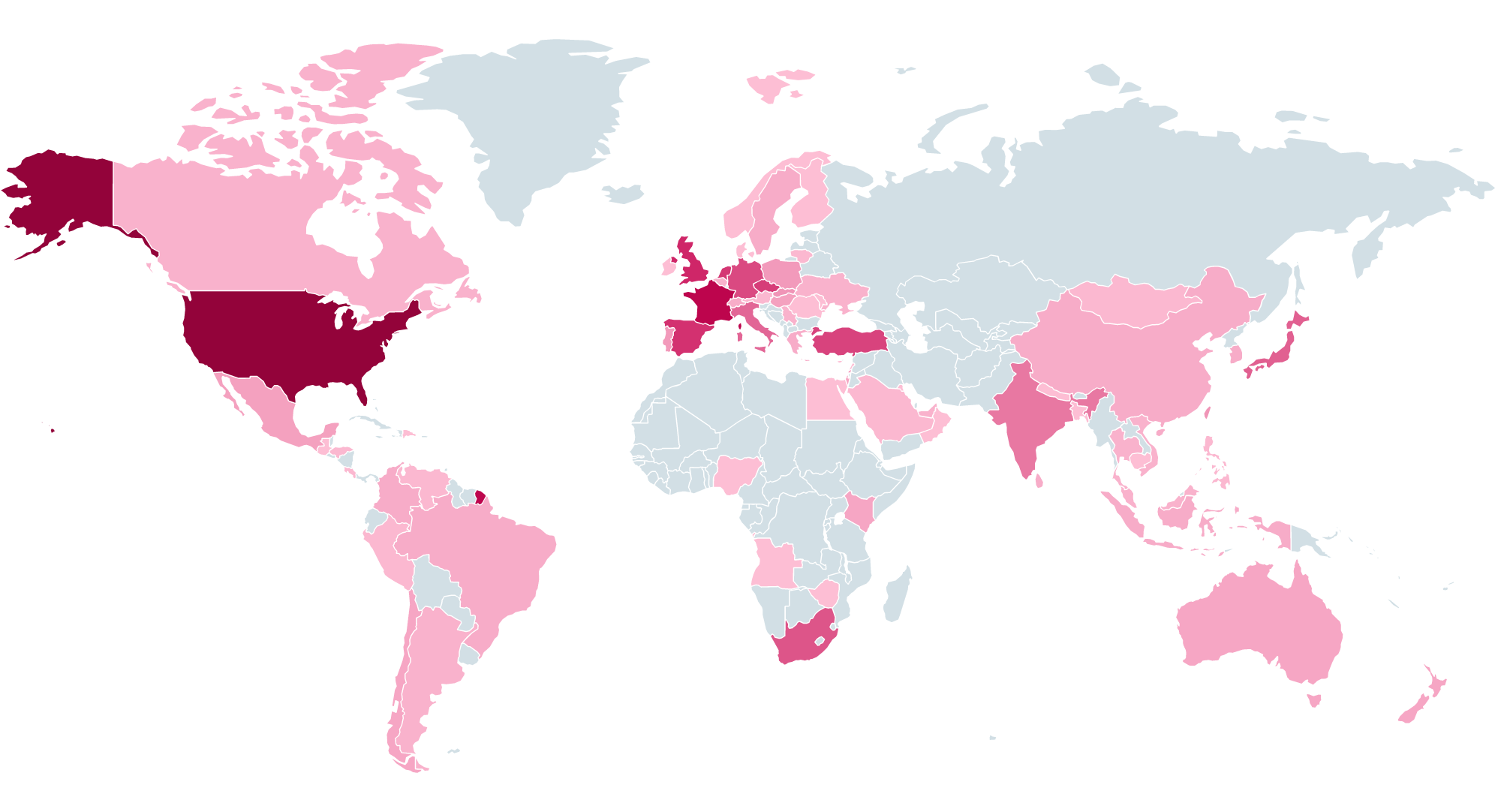
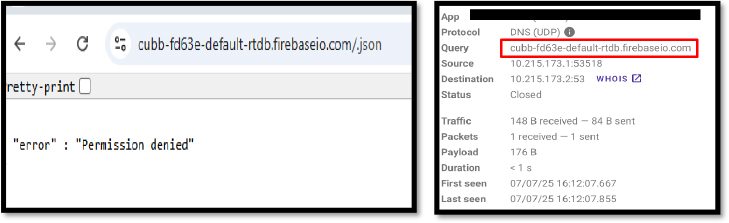
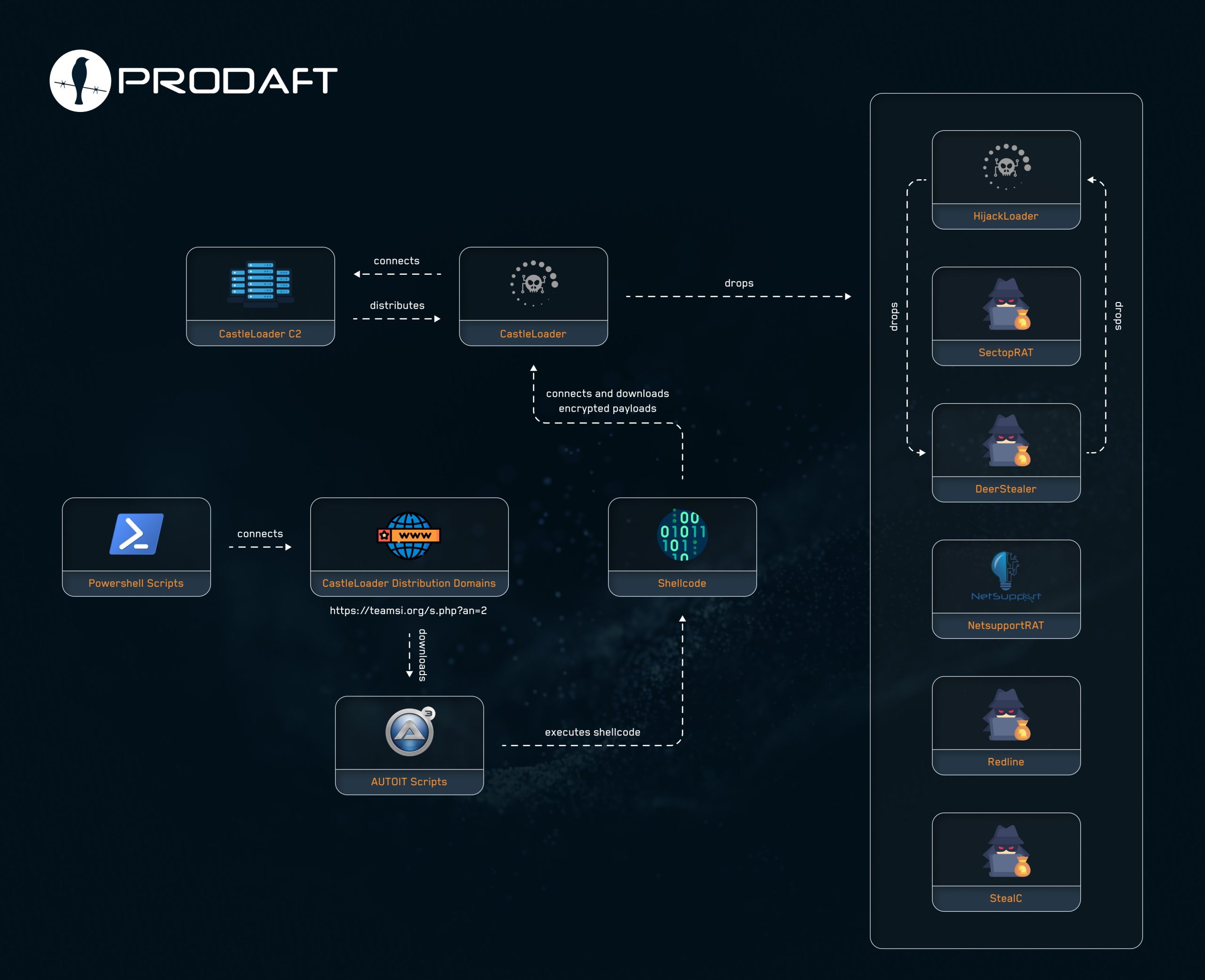
The wave of attacks targeting vulnerabilities in Microsoft SharePoint continues to escalate, reaching levels of sophistication and scale not witnessed since the mass infections orchestrated by LockBit. According to Microsoft, the breaches are attributed...