attack flow: helps defenders move from tracking adversary behaviors
Attack Flow
The Attack Flow project helps defenders move from tracking adversary behaviors individually to the sequence of techniques adversaries use to achieve their goals. Understanding the context within those sequences, as well as the relationships among them, enables additional defensive capabilities that make defenders much more effective. The project seeks to demonstrate how attack flows can explain defensive posture to executives, aid defenders to understand lessons learned from an incident, and support red-teamers to easily compose realistic adversary emulation scenarios.
Resources
| Resource | Description |
|---|---|
| Attack Flow Specification | An overview of the Attack Flow format and corresponding data dictionary. |
| Attack Flow JSON Schema | The JSON of the Attack Flow schema. |
| Attack Flow JSON Example Document | A JSON example of an Attack Flow. |
| Attack Flow Designer | A GUI tool for building Attack Flows. (See “Getting Started” below) |
Getting Started
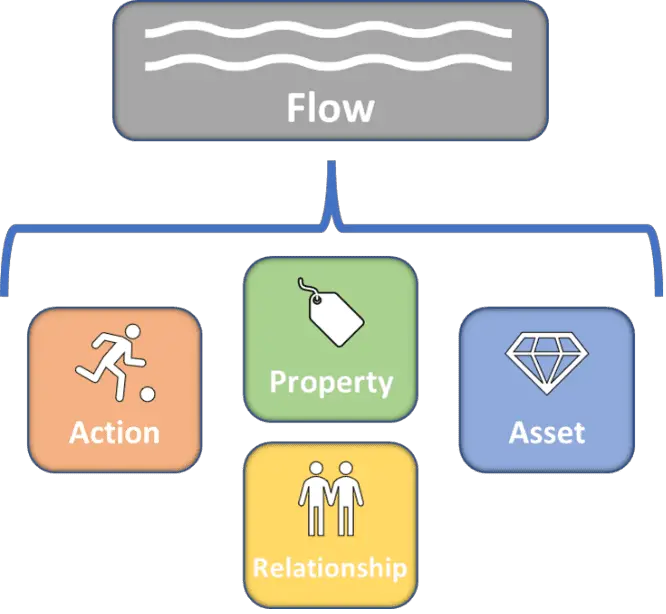
At a high level, Attack Flow is a machine-readable representation of a sequence of actions and assets along with knowledge properties about those actions and assets. This representation is composed of five main objects: the flow itself, a list of actions, a list of assets, a list of knowledge properties, and a list of causal relationships between the actions and assets. Each of these five objects includes a set of required and optional fields. Attack Flow uses MITRE ATT&CK to describe specific adversary behaviors.
Once you familiarize yourself with the Attack Flow specification, try using the Attack Flow Designer GUI to view or create your own Attack Flow. To get started:
- Go to the release page and download attack_flow_designer.zip as well as corpus.zip.
- Unzip these two files.
- In the attack_flow_designer directory, double click on index.html to open it in a web browser.
- Inside the Attack Flow Designer, go to File → Open Attack Flow. Navigate to the corpus directory and open one of the *.afd files.
- To create your own Attack Flow, refresh the page. Right-click in the Attack Flow workspace to create a node. Drag and drop from the plug icon to connect nodes together (subject to the rules of the Attack Flow specification).
- Save your Attack Flow in one of two formats:
- File → Save Attack Flow: saves the file with the *.afd extension. This file is suitable for opening up for editing in the Attack Flow Designer.
- File → Publish Attack Flow: saves a *.json file that conforms to the Attack Flow specification; this file is interoperable with other Attack Flow tools.
Getting Involved
There are several ways that you can get involved with this project and help advance threat-informed defense:
- Review the schema, use the designer, and tell us what you think. We welcome your review and feedback on the data model and our methodology.
- Help us prioritize additional example flows to create. Let us know what examples you would like to turn into an Attack Flow. Your input will help us prioritize how we expand our corpus.
- Share your use cases. We are interested in developing additional tools and resources to help the community understand and make threat-informed decisions in their risk management programs. If you have ideas or suggestions, we consider them as we explore additional research projects.
Use
Copyright 2021 MITRE Engenuity.





