The China-linked cyber-espionage group APT41 has launched a new surveillance campaign targeting government IT services in Africa—an unexpected turn for a region previously considered an unlikely target.
Researchers at Kaspersky Lab uncovered the operation after detecting anomalous activity on the workstations of an unnamed organization. The attackers employed remote administration tools and executed commands to verify connectivity with their command-and-control (C2) servers embedded within the compromised network.
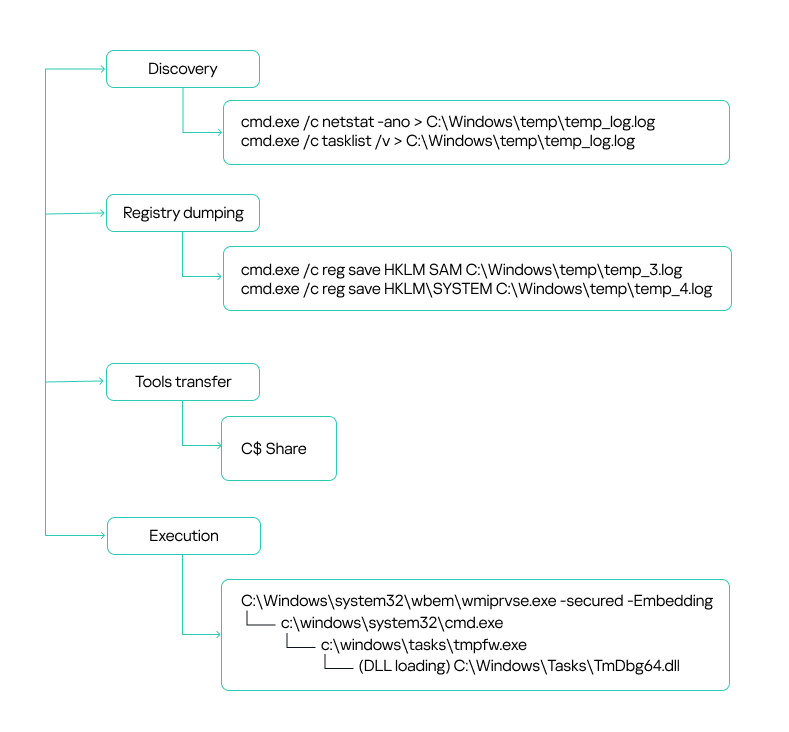
It was later determined that the initial point of compromise stemmed from an unmonitored host, where the Impacket framework—specifically the Atexec and WmiExec modules—was executed under a service account context. Following initial execution, the threat actors appeared dormant for a brief period. Soon after, they resumed activity using stolen credentials with elevated privileges to escalate access and move laterally across the network. This included the deployment of Cobalt Strike via DLL sideloading techniques.
A notable characteristic of the malicious libraries is their built-in locale checks: the malware halts execution if it detects system language settings corresponding to Chinese (Simplified or Traditional), Japanese, or Korean—clearly a tactic to avoid infecting machines in the regions from which the developers likely originate.
Within the victim’s infrastructure, SharePoint Server was repurposed as a covert command hub, camouflaging malicious behavior as routine corporate activity. Commands were transmitted through SharePoint and executed by a C#-based trojan delivered via SMB using executables named “agents.exe” and “agentx.exe.” These binaries interfaced with a web shell named CommandHandler.aspx installed on SharePoint to process the attackers’ instructions.
The attack blended conventional infiltration techniques with a “Living off the Land” strategy—leveraging legitimate enterprise services as command and control instruments. This approach aligns with MITRE ATT&CK techniques T1071.001 and T1047, rendering detection by traditional tools particularly challenging.
Post-reconnaissance, the adversaries concentrated their efforts on high-value endpoints. From these, scripts were launched through “cmd.exe” to fetch malicious HTA files from an external source masquerading as a legitimate GitHub domain. While the payload’s full functionality remains unclear, one observed script established a reverse shell, granting the attackers complete remote access to the system.
The toolkit employed was extensive. A customized version of Pillager harvested credentials from browsers and terminals, extracted files, email correspondence, chat logs, screenshots, and other sensitive data. Another utility, Checkout, gathered download histories and payment details from browsers such as Chrome, Opera, Brave, and others. RawCopy was used to extract raw registry files, while Mimikatz was deployed to dump user credentials.
APT41 demonstrated remarkable adaptability, tailoring malicious modules to the specific architecture of the victim’s environment. Their arsenal blended legitimate administrative tools with proprietary malware, emulating insider behavior and evading detection.
This campaign marks a strategic geographic pivot for APT41, signaling China’s increasing cyber focus on regions previously outside its operational scope. According to Trend Micro, early indicators of this shift emerged as far back as late 2022. The use of internal enterprise platforms for both command execution and data exfiltration underscores the evolution of advanced persistent threats, where the boundary between red teaming and live cyberattacks has all but disappeared.




