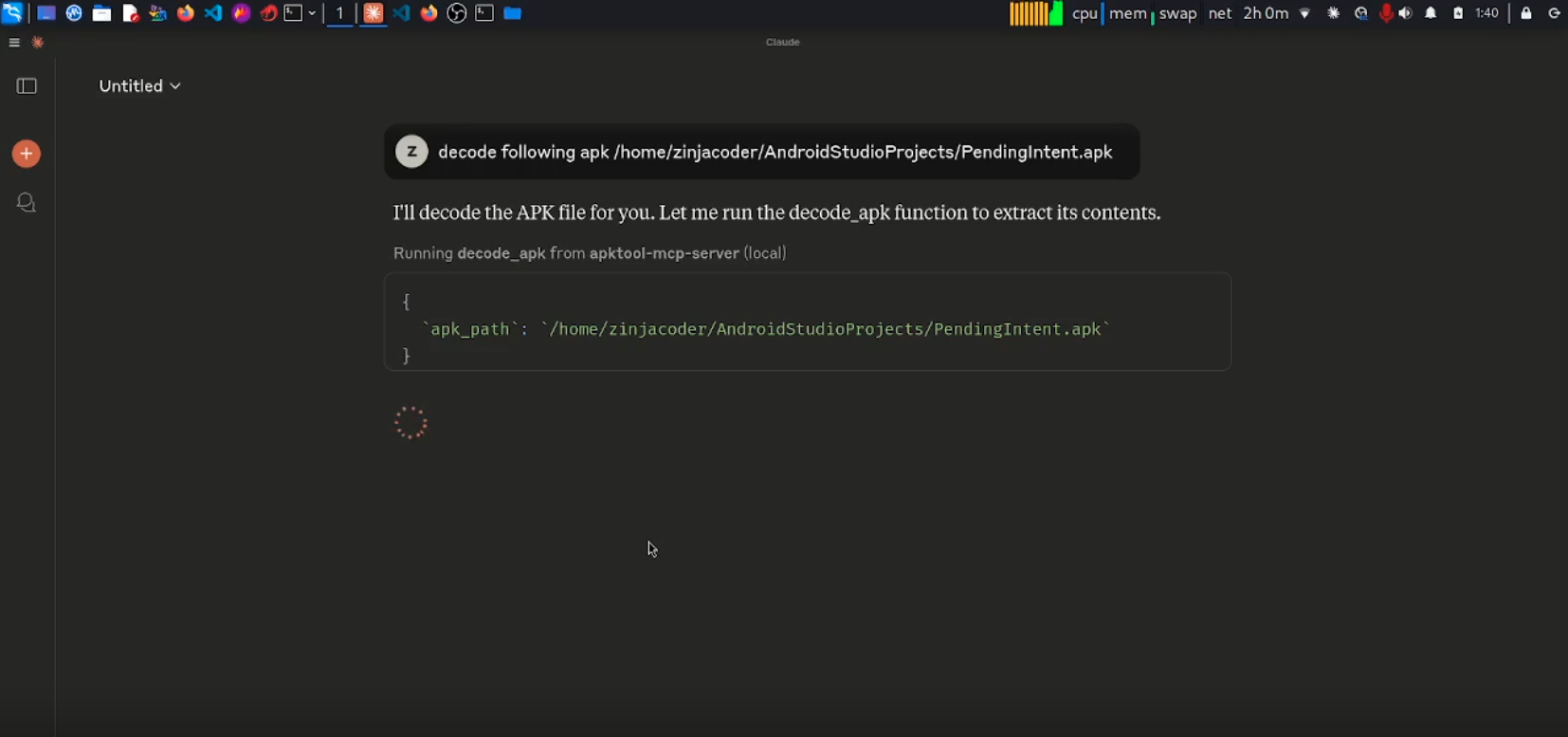
Fully automated MCP server built on top of apktool to analyze Android APKs using LLMs like Claude — uncover vulnerabilities, parse manifests, and reverse engineer effortlessly.
apktool-mcp-server is a MCP server for the Apk Tool that integrates directly with Model Context Protocol (MCP) to provide live reverse engineering support with LLMs like Claude.
Think: “Decompile → Context-Aware Code Review → AI Recommendations” — all in real time.
Current MCP Tools
The following MCP tools are available:
- build_apk() — Build an APK from a decoded APKTool Project.
- get_manifest() — Get the AndroidManifest.xml content from a decoded APK project.
- get_apktool_yml() — Get apktool.yml information from a decoded APK project.
- list_smali_directories() — List all smali directories in a project.
- list_smali_files() — List smali files in a specific smali directory, optinally filtered by package prefix.
- get_smali_file() — Get content of a specific smali file by class name.
- modify_smali_file() — Modify the content of a specific smali file.
- list_resources() — List resources in a project, optionally filtered by resource type.
- get_resource_file() — Get Content of a specific resource file.
- modify_resource_file() — Modify the content of a specific resource file.
- search_in_file() — Search for a pattern in files with specified extensions.
- clean_project() — Clean a project directory to prepare for rebuilding.
- decode_apk() — Decode an APK file using APKTool, extracting resources and smali code.
Sample Prompts
Basic Code Understanding
- “List all smali directories for the dvac project.”
- “Show me all the smali files under the package prefix com.vulnerable.component in the dvac project.”
- “Get the smali code for the class com.vulnerable.component.MainActivity.”
- “Compare MainActivity.smali with its previous version and show differences.”
- “Search for usage of startActivity in smali files of dvac project.”
Vulnerability Detection
- “Analyze declared permissions in the dvac AndroidManifest.xml and flag dangerous ones.”
- “Search for hardcoded URLs or IPs in all .xml and .smali files in the project.”
- “Find all uses of PendingIntent.getActivity in smali files.”
- “Check for exported activities or receivers in dvac’s AndroidManifest.xml.”
- “List all smali files that access android.permission.SEND_SMS or READ_CONTACTS.”
Reverse Engineering Helpers
- “Decode this APK: dvac.apk and create a project called dvac.”
- “Create a new APKTool project called test-harness.”
- “Clean the dvac project before rebuild.”
- “Extract DEX files from dvac project for external analysis.”
- “Modify MainActivity.smali to insert a log line at the beginning of onCreate().”
Static Analysis
- “Get the complete AndroidManifest.xml from dvac project.”
- “Show the contents of apktool.yml for the dvac project.”
- “List all resource files of type layout.”
- “Search for the word password in all resource and smali files.”
- “Check which permissions are used and compare them against typical over-permissioning risks.”
AI Code Modification
- “Modify the onCreate() method in MainActivity.smali to add a toast message.”
- “Replace all http:// links with https:// in strings.xml.”
- “Add the android:exported=false attribute to all activities in the AndroidManifest.xml.”
- “Patch the method validateLogin in LoginManager.smali to always return true.”
- “Add logging statements to every method in MainActivity.smali.”
Documentation & Metadata
- “List all decoded APKTool projects in the workspace.”
- “Show me the apktool.yml config to review the version, original APK metadata, and compression settings.”
- “Get all available Android devices connected via ADB. (To be migrated to ADB MCP Server.)”
- “Get metadata about the project dvac from its apktool.yml.”
- “Check which APKTool version is currently installed on the server.”