Apache Hadoop & Flink Hacked: Rootkits Lurk Beneath “Invisible” Malware
Cybersecurity researchers have identified a new type of attack that exploits weaknesses in the configuration of Apache’s Hadoop and Flink software, deploying cryptocurrency miners on target systems.
“This attack is particularly intriguing due to the attacker’s use of packers and rootkits to conceal the malware,” note researchers from Aqua Security in their report published on January 8th. The malware erases the contents of specific directories and alters system configurations to evade detection.
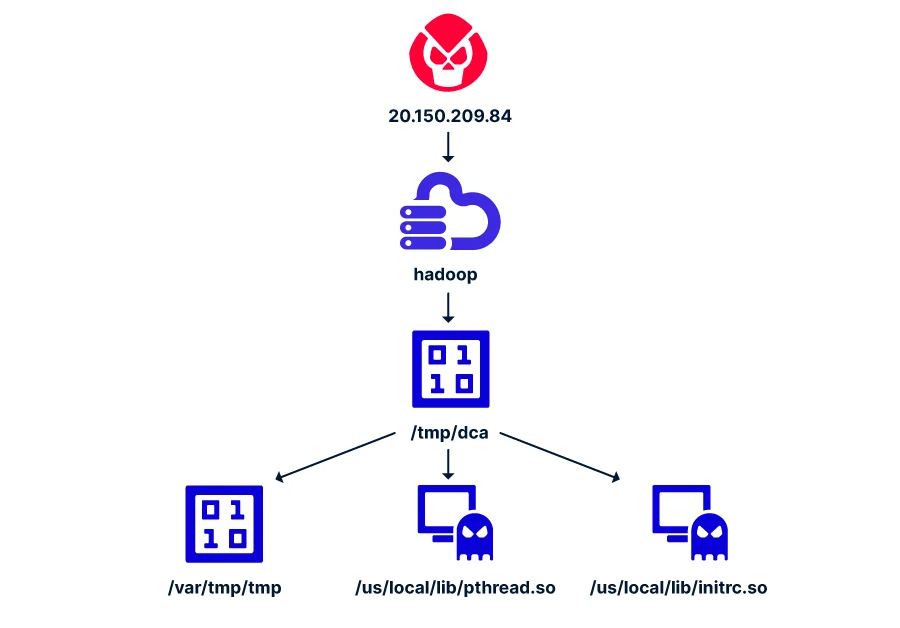
The attack flow
The infection chain for Apache Hadoop exploits a misconfiguration in the YARN (Yet Another Resource Negotiator) resource manager, responsible for tracking resources in the cluster and scheduling applications.
Specifically, this flaw allows a remote, unauthenticated attacker to execute arbitrary code through a specially crafted HTTP request, depending on the user privileges on the node where the code is executed.
Similar attacks on Apache Flink also target a misconfiguration that allows remote attackers to execute code without any authentication.
These vulnerabilities are not new and have previously been exploited by financially motivated groups such as TeamTNT, known for their attacks on Docker and Kubernetes for cryptojacking and other malicious activities.
Nevertheless, the latest attacks are notable for their use of rootkits to conceal cryptocurrency mining processes following the initial penetration of Hadoop and Flink applications.
Initially, the attacker sends an unauthenticated request to deploy a new application, followed by a POST request to YARN, asking to launch this new application with a specific command.
This command is designed to clear the /tmp directory of all existing files, download a file named “dca” from a remote server, execute it, and then repeat the deletion of all files in the /tmp directory.
The executed code is a packed ELF binary, which downloads two rootkits and a Monero miner binary file. To achieve persistence, a cron job is created to download and execute a shell script that deploys the “dca” binary file.
Analysis of the perpetrator’s infrastructure reveals that the server for downloading the payload was registered on October 31, 2023.
As a risk mitigation measure, organizations are advised to deploy agent-based security solutions to detect cryptominers, rootkits, obfuscated or packed binary files, and other suspicious activities.





