Above
Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security professionals.
Mechanics
Above is an invisible network sniffer for finding vulnerabilities in network equipment. It is based entirely on network traffic analysis, so it does not make any noise in the air. He’s invisible. Completely based on the Scapy library.
The main task that Above solves is to search for L2/L3 protocols inside the network and to find vulnerabilities in configurations based on sniffed traffic.
Supported protocols
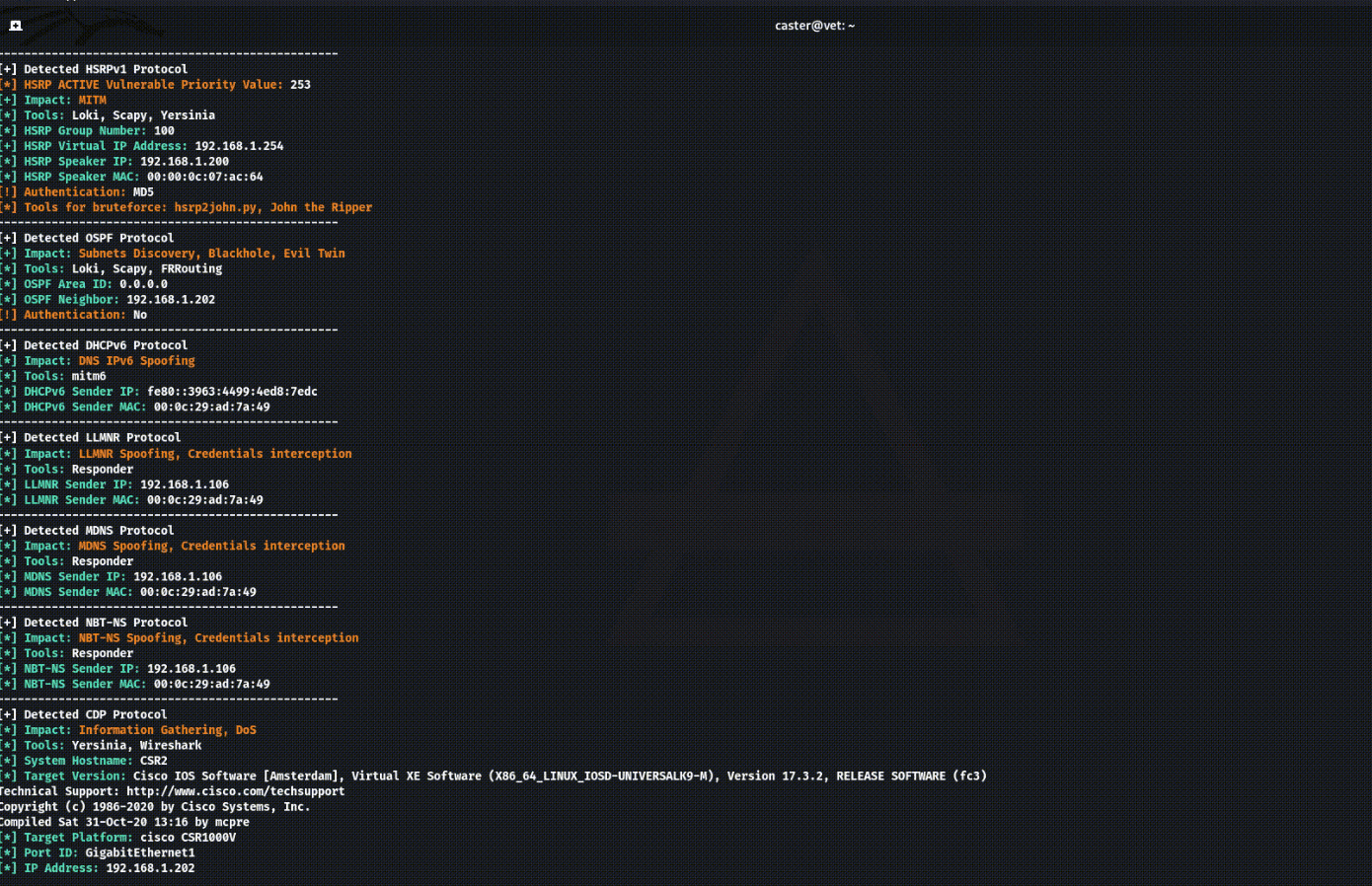
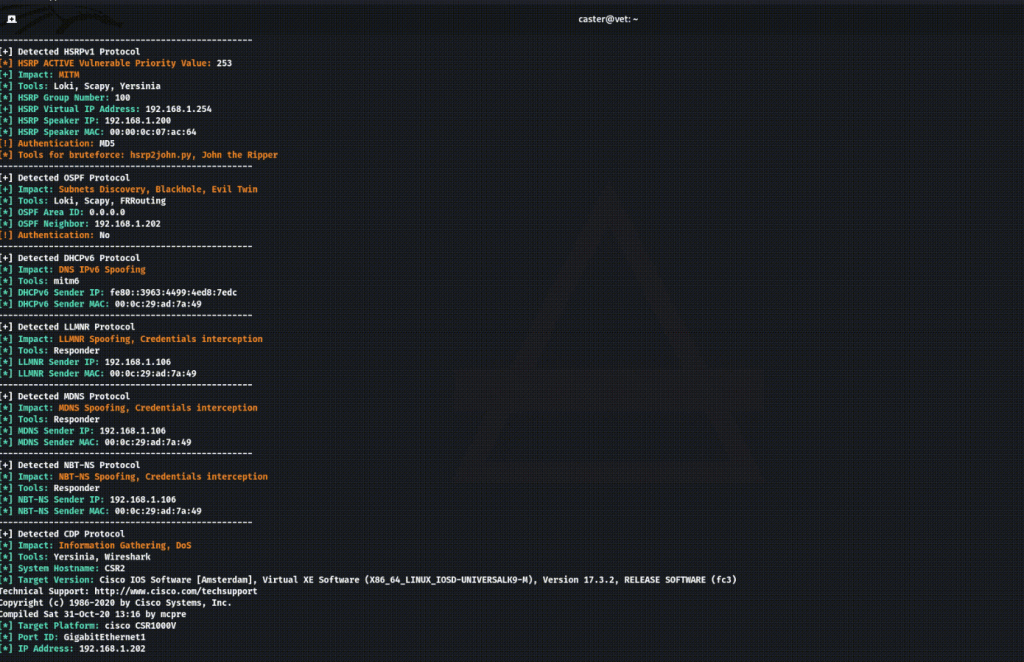
Detects up to 12 protocols:
- CDP (Cisco Discovery Protocol)
- DTP (Dynamic Trunking Protocol)
- Dot1Q (VLAN Tagging)
- OSPF (Open Shortest Path First)
- EIGRP (Enhanced Interior Gateway Routing Protocol)
- VRRPv2 (Virtual Router Redundancy Protocol)
- HSRPv1 (Host Standby Redundancy Protocol)
- STP (Spanning Tree Protocol)
- LLMNR (Link Local Multicast Name Resolution)
- NBT-NS (NetBIOS Name Service)
- MDNS (Multicast DNS)
- DHCPv6 (Dynamic Host Configuration Protocol v6)
Operating Mechanism
Above works in two modes:
- Hot sniffing on your interface specifying a timer
- Analyzing traffic dumps in cold mode (Offline)
The tool is very simple in its operation and is driven by arguments:
- Interface. Specifying the network interface on which sniffing will be performed
- Timer. Time during which traffic analysis will be performed
- Output pcap: Above will record the listened traffic to pcap file, its name you specify yourself
- Input pcap: The tool takes an already prepared .pcap as input and looks for protocols in it
Information about protocols
The information obtained will be useful not only to the attacker but also to the security engineer, he will know what he needs to pay attention to.
When Above detects a protocol, it outputs the necessary information to indicate the attack vector or security issue:
-
Impact – What kind of attack can be performed on this protocol;
-
Tools – What tool can be used to launch an attack;
-
Technical information – Required information for the attacker, sender IP addresses, FHRP group IDs, OSPF/EIGRP domains, etc.
This information can also be used by a security engineer to improve network security
Install & Use
Copyright (C) 2024 wearecaster