28 Android VPNs Found to be Secret Proxies
Twenty-eight free VPN applications on Google Play were found to employ a malicious SDK, transforming Android devices into residential proxies, likely utilized for cybercrimes and bot operations.
The team at HUMAN discovered that these malicious applications utilized an SDK from LumiApps, which included the Proxylib library for proxy organization. In total, 28 applications were identified that covertly turned Android devices into proxy servers, 17 of which were disguised as free VPN applications.
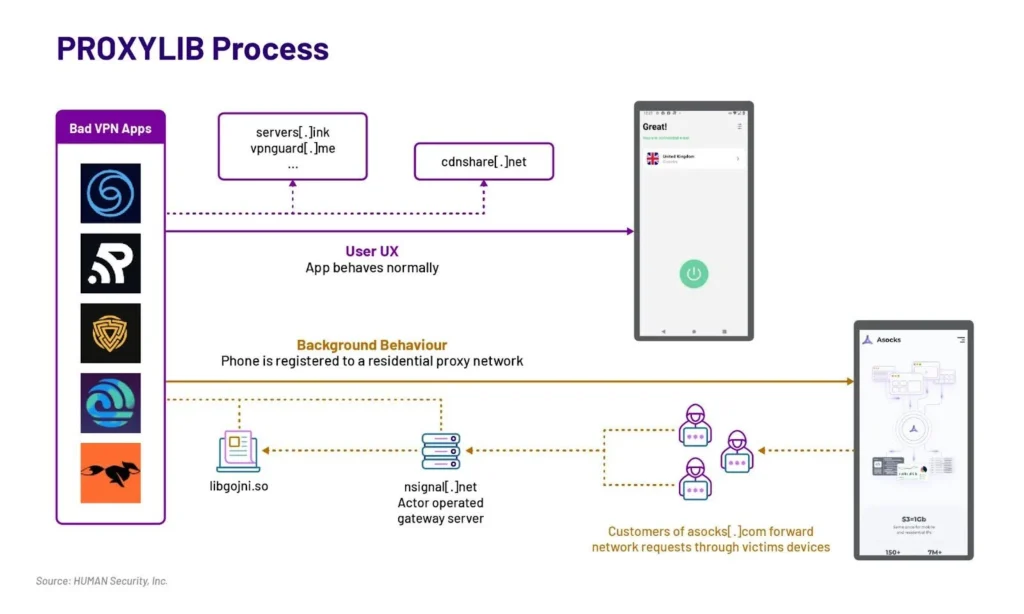
LumiApps, an Android app monetization platform, claims its SDK employs the device’s IP address to load web pages in the background, the data from which are then transmitted to companies. According to LumiApps, this process is designed to not interfere with the user experience and fully comply with legislation (GDPR/CCPA).
However, it remains unclear whether the developers of the free applications were aware that the SDK converted user devices into proxy servers, potentially used for criminal activities, including advertising fraud, spam, phishing, credential stuffing, and brute-force attacks.
HUMAN suggests a connection between the malicious applications and the residential proxy service provider Asocks, based on discovered connections to the provider’s website. Additionally, the Asocks service is often promoted by cybercriminals on hacking forums.
Following HUMAN’s report, Google removed all applications utilizing the LumiApps SDK from the Play Store and updated Google Play Protect to detect LumiApp libraries used in applications.
Yet, many of the identified applications have reappeared on Google Play, presumably after their developers removed the LumiApps SDK. In some instances, applications were published under different developer accounts, indicating possible prior account suspensions.
Experts recommend updating previously used applications to the latest versions that do not utilize the said SDK or, preferably, removing them entirely.





