Suzaku: A sigma-based threat hunting and fast forensics timeline generator for cloud logs
Suzaku is a threat hunting and fast forensics timeline generator for cloud logs. (Imagine Hayabusa but for cloud logs instead of Windows event logs.) It is currently under active development with basic native sigma detection support for AWS CloudTrail logs. After AWS, we plan on supporting Azure and GCP logs.
With cloud logs, there are thousands of different API calls and more events then anyone could sift through manually. Suzaku is designed to not just find the attacks amongst the noise, but also to provide you with a DFIR timeline that contains only the events and data you need to perform a fast-forensics investigation. We also plan on creating summaries, search capabilities, etc… in order to quickly discover what happened at a high level as well as not miss any events that an attacker performed after you discover them.
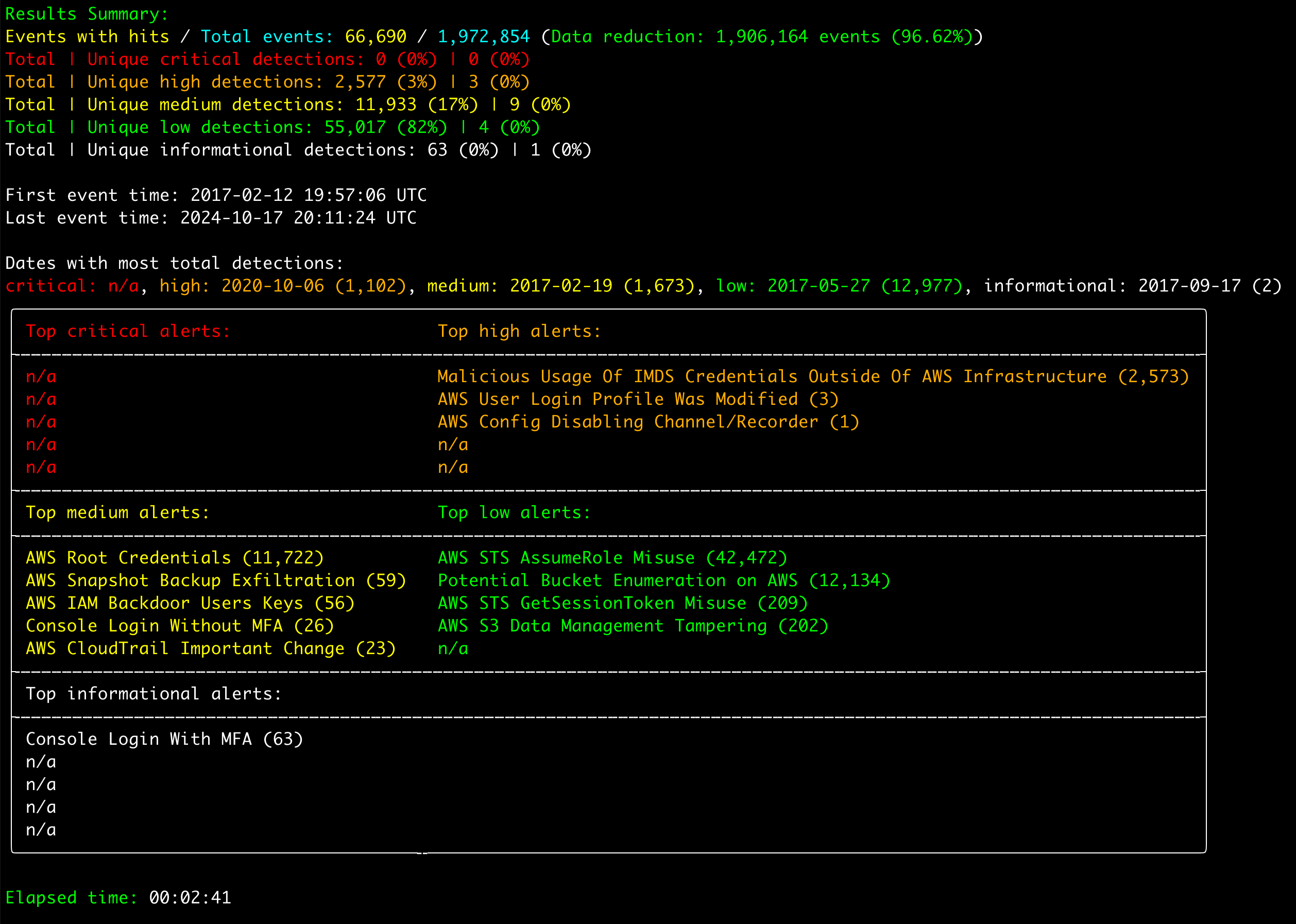
Results Summary
Companion Projects
- suzaku-rules – our repository of sigma rules. New upstream sigma rules are added automatically. We also host our own rules here.
- suzaku-sample-data – a repository of various cloud logs with attack evidence inside them used for testing Suzaku as well as for writing new detection rules.
Features
- Cross-platform support: Windows, Linux, macOS.
- Developed in Rust to be memory safe and fast.
- Scans
.jsonor compressed.json.gzfiles. - Creates single easy-to-analyze timelines for forensic investigations and incident response.
- Threat hunting based on IoC signatures written in easy to read/create/edit YML-based Sigma rules.
- Save results to CSV, JSON and JSONL.