Ransomware for Sale: Your Data Held Hostage
From June 2023 to February 2024, specialists from Sophos‘s cyber intelligence division identified 19 different types of ransomware being offered for sale on four dark web forums for relatively modest sums, ranging from $20 to 0.5 bitcoins (approximately $13,000 at the time of the study).
Experts draw a parallel between these tools and the cheap imported firearms that flooded the U.S. market in the 1960s and 1970s. Despite the unreliability of such solutions, they provide novice cybercriminals with significant advantages—namely, a low entry threshold into the criminal business and relatively weak traceability. This allows individuals to engage in extortion independently, without the need to interact with affiliate networks that typically take a significant share of the profits.
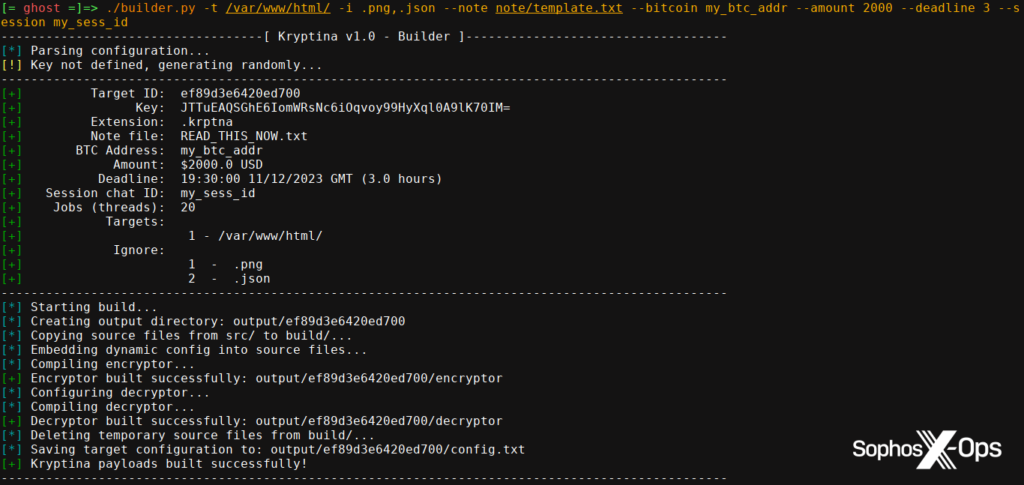
According to Sophos specialists, malicious programs such as EvilExtractor can indeed prove unreliable. Some even contain built-in “backdoors”—hidden functions that allow malefactors to remotely control infected systems or access data from both users and inexperienced “colleagues.”
Nevertheless, young hackers are likely willing to accept all associated risks since using such tools can be their first step toward more lucrative activities within well-known cybercriminal groups.
Although the effectiveness of inexpensive ransomware in real attacks remains unverified, researchers note that EvilExtractor, for example, was used last year in attacks in the U.S. and Europe. Reports also exist of three other variants successfully deployed by criminals.
Most incidents go unnoticed and undisclosed, as they are predominantly aimed at small companies and private individuals who cannot afford costly protective measures.
An analysis of activity on shadow forums, where cheap ransomware is sold, revealed their “amateurish” nature. Unlike the most notorious darknet marketplaces, here users freely ask naïve questions and share information, including guides on developing and deploying software. Among the most popular materials is a manual written by a well-known ransomware operator nicknamed Bassterlord.
Researchers cite a forum participant who planned to conduct targeted phishing to gain system access, then collect as much valuable data as possible and launch a ransomware program. He sought advice from other community members regarding potential high-value targets for such an attack and recommendations for its execution, as it was his first attempt.
Sophos underscores the seriousness of the accessibility of malicious software on shadow internet forums. This phenomenon poses significant challenges for cybersecurity experts, as most such attacks remain unnoticed and underreported. This leaves an information gap that the community needs to address.





