Category: Network Defense
CrowdSec The CrowdSec Security Engine is an open-source, lightweight software that detects and blocks malicious actors from accessing your systems at various levels, using log analysis and threat patterns called scenarios. CrowdSec is a modular framework,...
Cloud Custodian Cloud Custodian is a rules engine for managing public cloud accounts and resources. It allows users to define policies to enable a well-managed cloud infrastructure, that’s both secure and cost-optimized. It consolidates...
FastNetMon FastNetMon – A high-performance DoS/DDoS load analyzer built on top of multiple packet capture engines (NetFlow, IPFIX, sFLOW, SnabbSwitch, netmap, PF_RING, PCAP). What can we do? We can detect hosts in our networks...
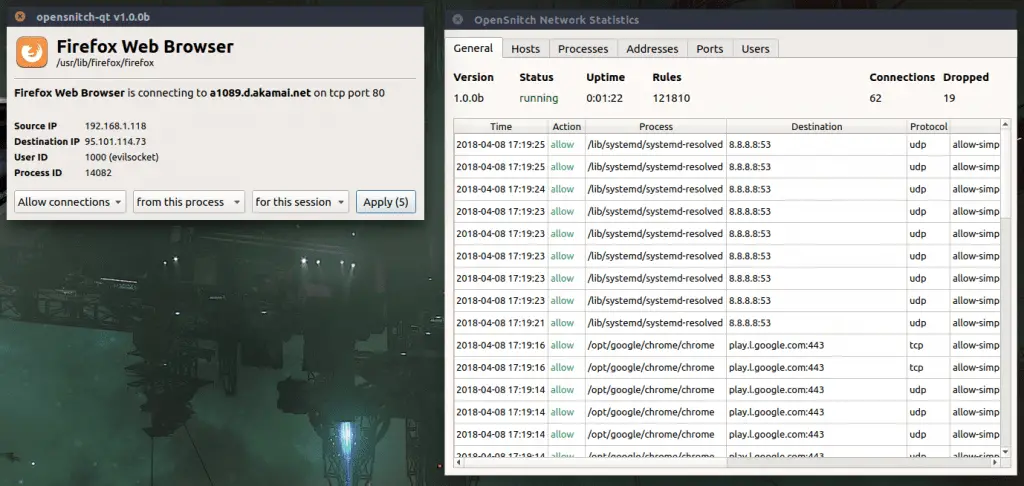
OpenSnitch OpenSnitch is a GNU/Linux port of the Little Snitch application firewall. How Does It Work OpenSnitch is an application-level firewall, meaning then while running, it will detect and alert the user for every...
Parsec Parsec allows you to easily share your work and data in the cloud in total privacy thanks to end-to-end cryptographic security. Key features: Works as a virtual drive on you computer. You can...
Security Scorecards Goals Automate analysis and trust decisions on the security posture of open source projects. Use this data to proactively improve the security posture of the critical projects the world depends on. Checks...
teler-waf teler-waf is a comprehensive security solution for Go-based web applications. It acts as an HTTP middleware, providing an easy-to-use interface for integrating IDS functionality with teler IDS into existing Go applications. By using teler-waf, you can...
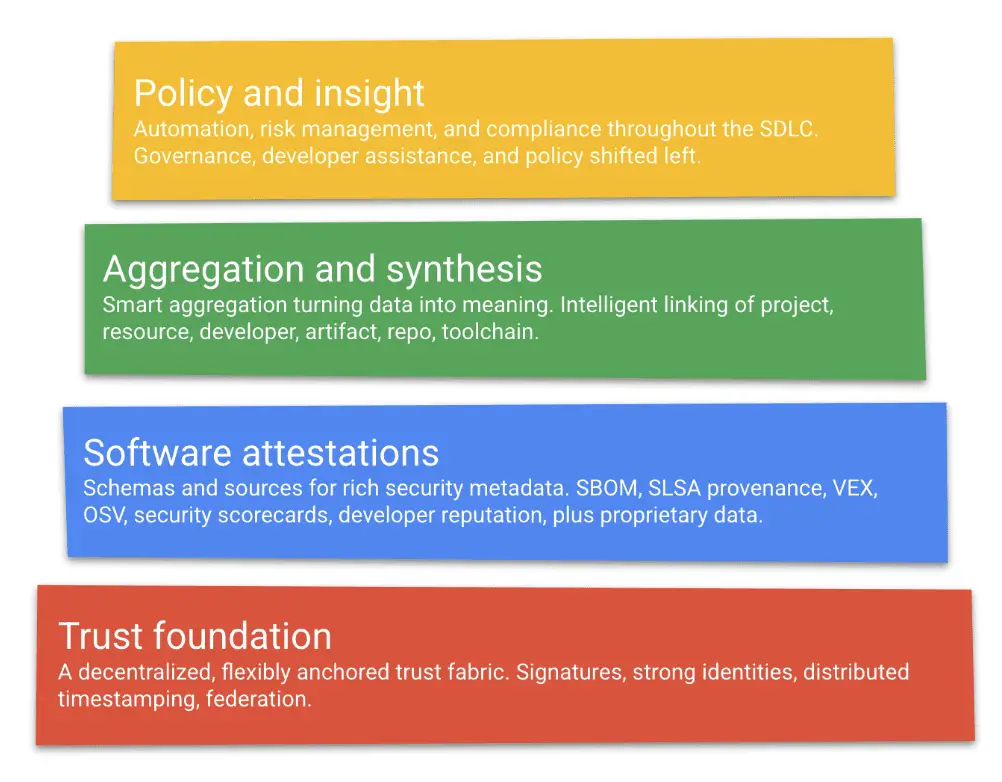
GUAC: Graph for Understanding Artifact Composition Graph for Understanding Artifact Composition (GUAC) aggregates software security metadata into a high-fidelity graph database—normalizing entity identities and mapping standard relationships between them. Querying this graph can drive...
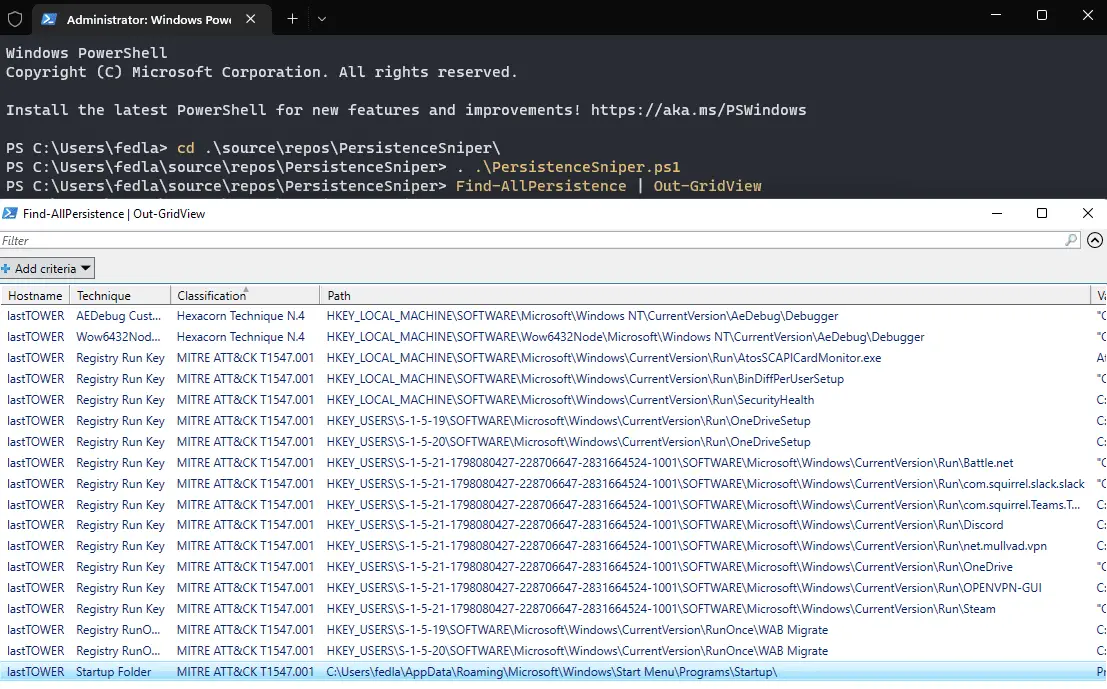
PersistenceSniper PersistenceSniper is a Powershell script that can be used by Blue Teams, Incident Responders, and System Administrators to hunt persistences implanted in Windows machines. The script is also available on Powershell Gallery. The...
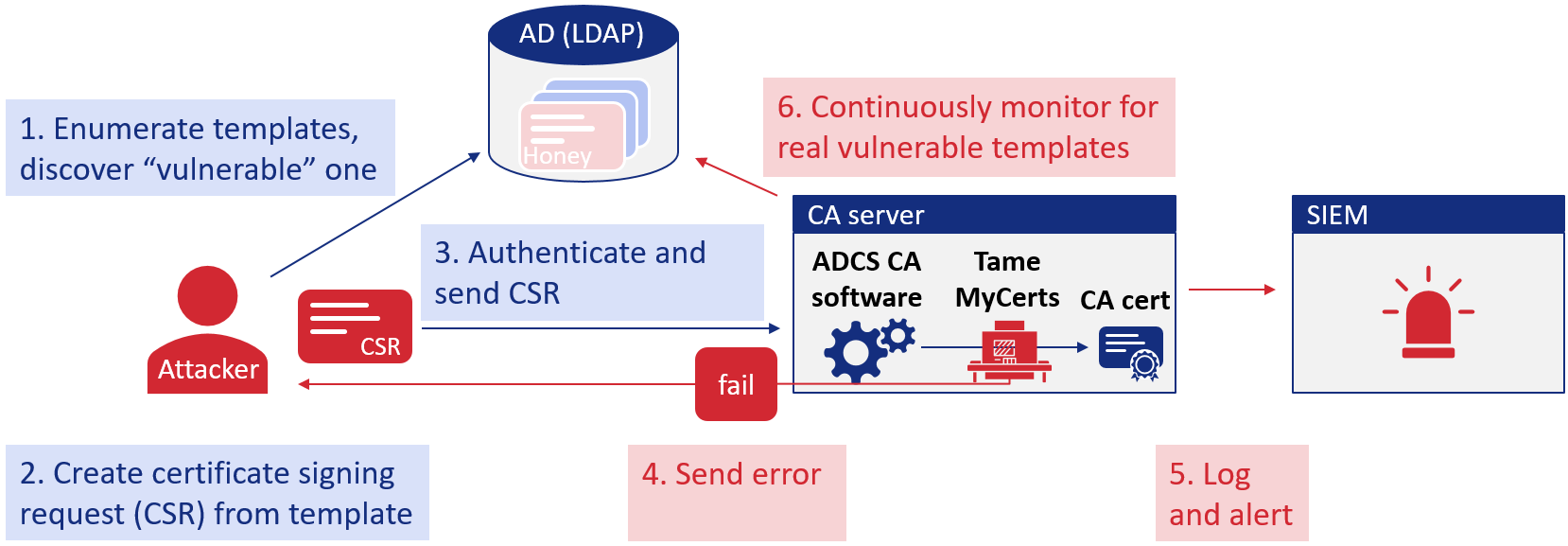
Certiception Certiception is a honeypot for Active Directory Certificate Services (ADCS), designed to trap attackers with a realistic and attractive bait that triggers highly relevant alerts. Developed by the SRLabs Red Team, Certiception creates a...
kflowd kflowd runs as an agent on Linux endpoints to monitor processes via eBPF kernel subsystem for filesystem and TCP and UDP networking events, enabling immediate threat and anomaly detection on suspicious activities. Advanced...
Blackdagger Blackdagger represents a significant advancement in automation technology, offering a comprehensive solution for orchestrating complex workflows in DevOps, DevSecOps, MLOps, MLSecOps, and Continuous Automated Red Teaming (CART) environments. At its core, Blackdagger simplifies...
LDAP Firewall LDAP Firewall is an open-source tool for Windows servers that lets you audit and restrict incoming LDAP requests. Its primary use cases are to protect Domain Controllers, block LDAP-based attacks, and tightly...
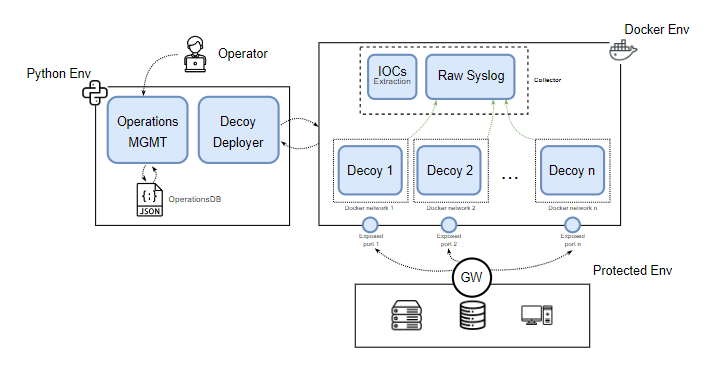
DOLOS-T DOLOS-T is an orchestration platform for cyber deception operations that allows the deployment of realistic decoys and services with high and medium interaction to detect threats in the operational infrastructure. It can be...
vArmor vArmor is a cloud-native container sandbox system. It leverages Linux’s AppArmor LSM, BPF LSM and Seccomp technologies to implement enforcers. It can be used to strengthen container isolation, reduce the kernel attack surface, and increase the difficulty and...
FalconHound FalconHound is a blue team multi-tool. It allows you to utilize and enhance the power of BloodHound in a more automated fashion. It is designed to be used in conjunction with an SIEM...