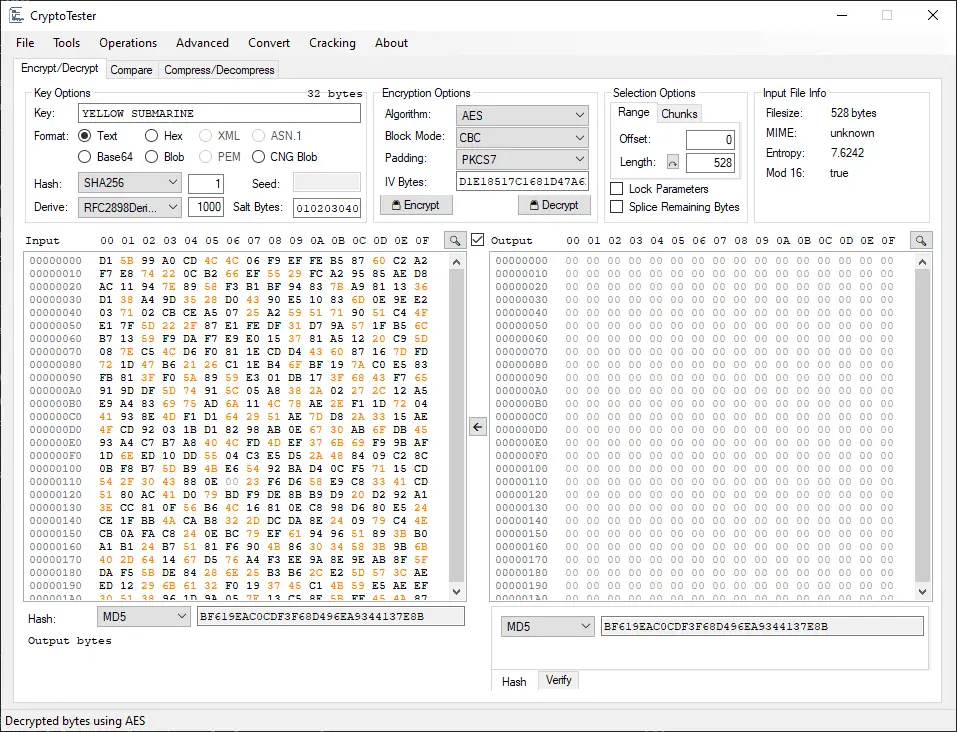
CryptoTester: utility for playing with cryptography, geared toward ransomware analysis
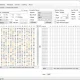
CryptoTester A utility for playing with cryptography, geared toward ransomware analysis. Hex Views All hex views used in CryptoTester offer a few enhanced capabilities. Null bytes are colored a lighter gray Bytes representing ASCII...