Category: Vulnerability Assessment
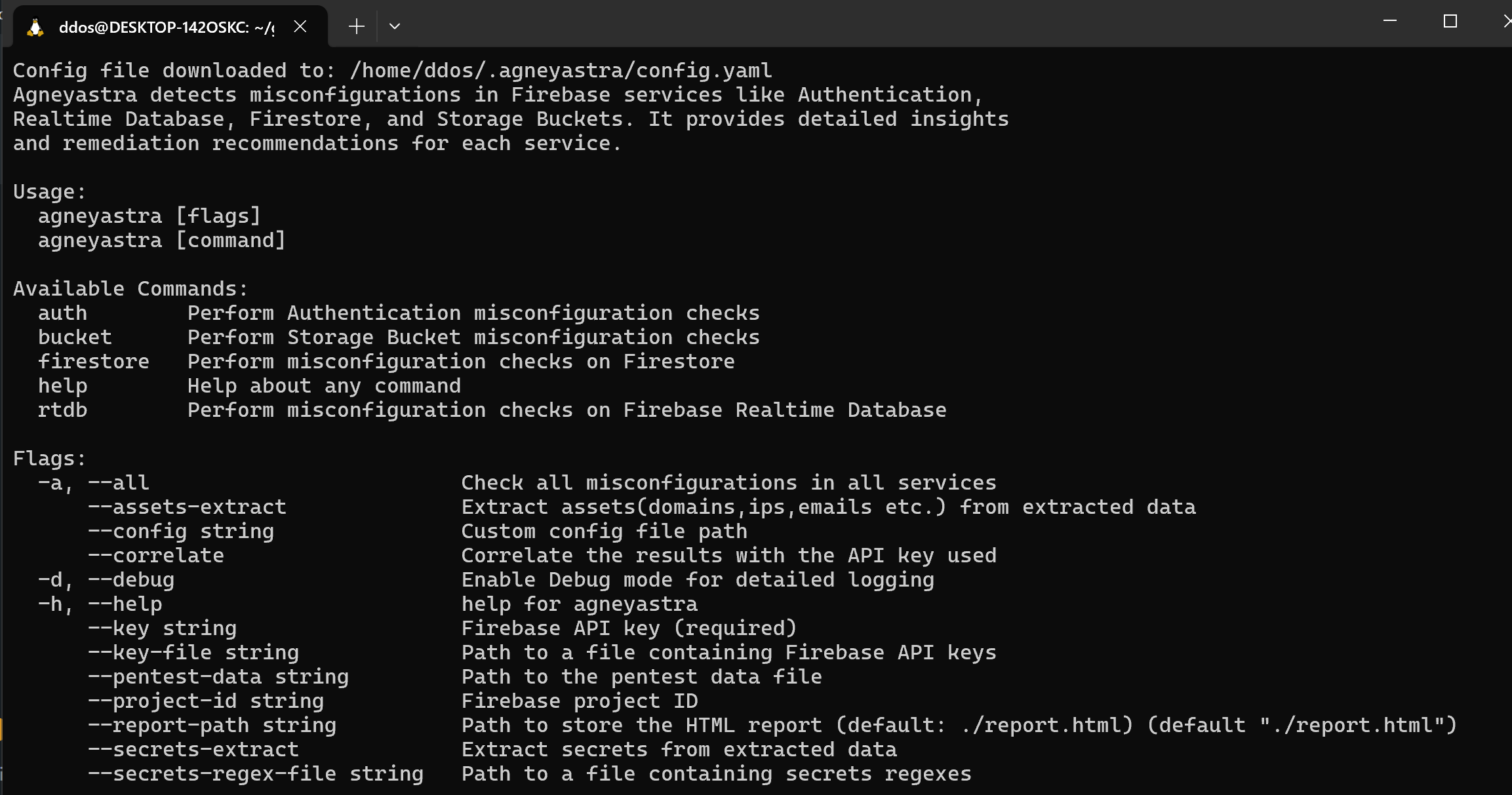
Firebase, a versatile platform by Google, powers countless web and mobile applications with its extensive suite of services including real-time databases, authentication, cloud storage, and hosting. Its ubiquity and ease of use make it...
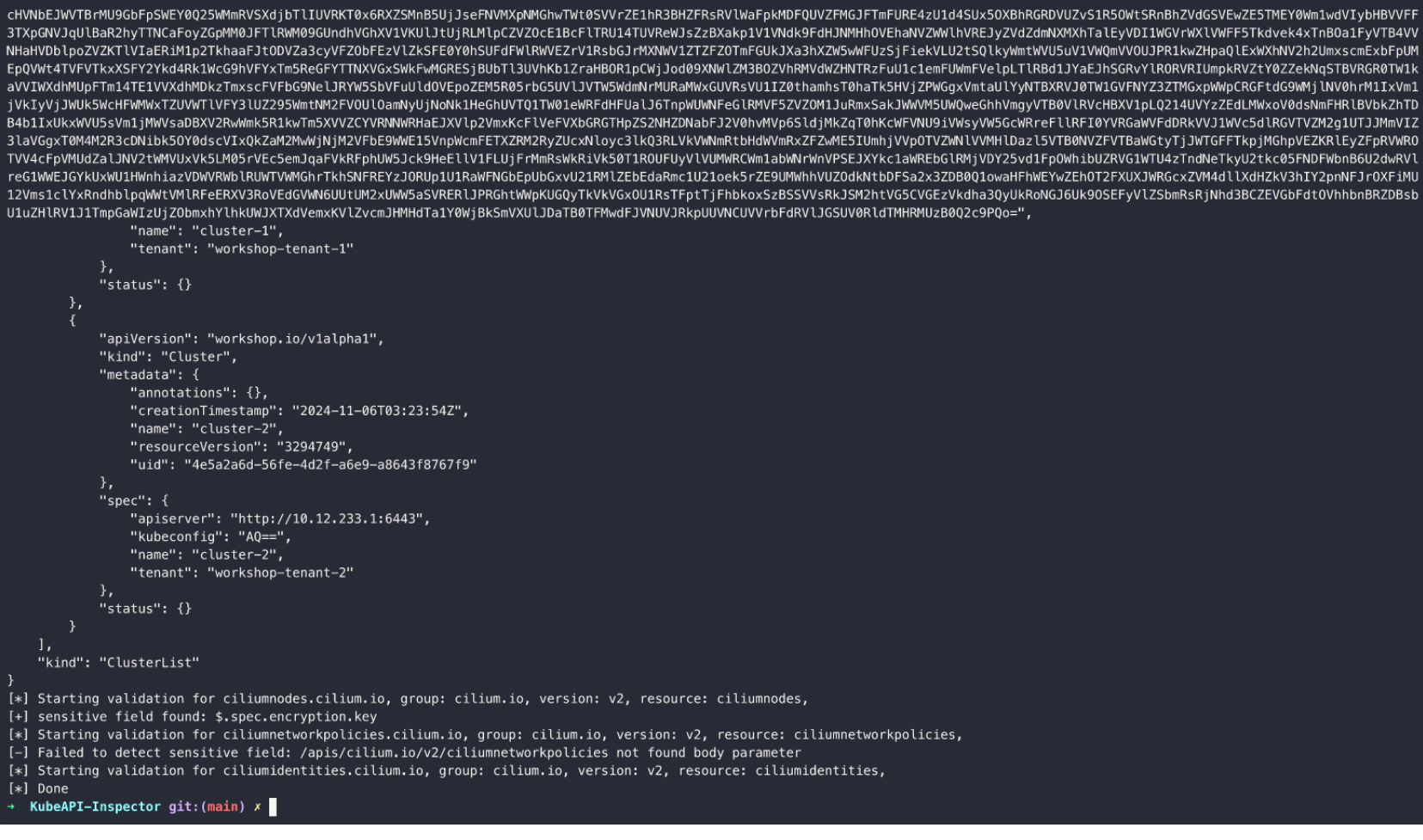
A tool specifically designed for Kubernetes environments aims to efficiently and automatically discover hidden vulnerable APIs within clusters. It reveals and demonstrates a common error through a workshop format, which could lead to API...
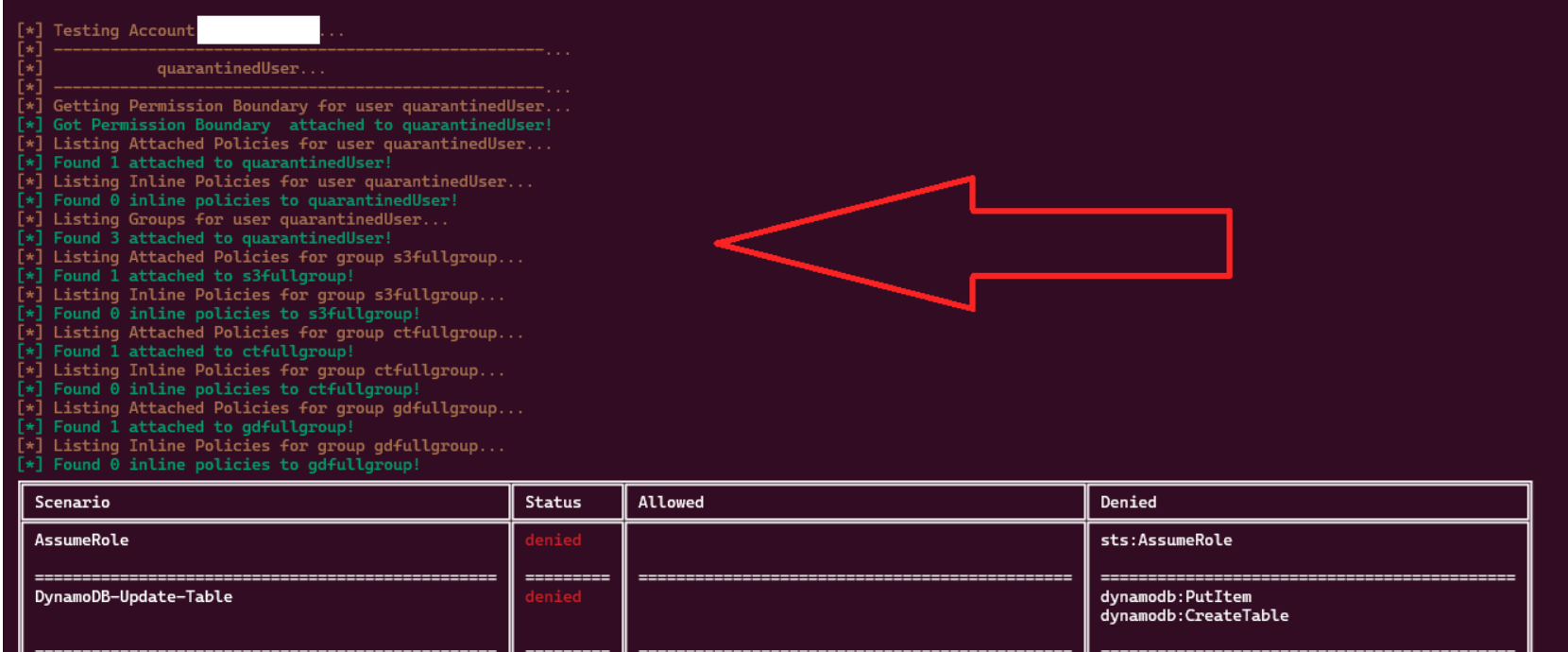
DetentionDodger is a tool designed to find users whose credentials have been leaked/compromised and the impact they have on the target. Install Local Installation To install, the only thing needed, is to install the...
In recent years, attacks targeting the Web Application Platform have been increasing rapidly. sisakulint is a static and fast SAST for GitHub Actions. This great tool can automatically validate yaml files according to the guidelines...
KubeStalk KubeStalk is a tool to discover Kubernetes and related infrastructure-based attack surfaces from a black-box perspective. This tool is a community version of the tool used to probe for unsecured Kubernetes clusters around...
SupplyShield is an open-source application security orchestration framework designed to secure your software supply chain from vulnerabilities, malicious dependencies, and unapproved base images. It provides a comprehensive solution to automate the detection, prioritization, and...
An AI-powered, self-hosted GitHub bot designed to detect and mitigate supply chain attacks in pull requests. SadGuard combines intelligent code analysis with executable behavior monitoring to secure your software pipeline. SadGuard was inspired by...
Introducing Varunastra, an innovative tool designed to enhance the security of Docker environments. Named after The Varunastra (वरुणास्त्र), it is the water weapon according to the Indian scriptures, incepted by Varuna, god of hydrosphere....
Metlo Metlo is an open-source API security platform Create an Inventory of all your API Endpoints. Proactively test your APIs before they go into production. Detect API attacks in real-time. Features Endpoint Discovery –...
Subdominator Meet Subdominator, your new favorite CLI tool for detecting subdomain takeovers. It’s designed to be fast, accurate, and dependable, offering a significant improvement over other available tools. Benchmark ? A benchmark was run across...
xeol A scanner for end-of-life (EOL) packages in container images, filesystems, and SBOMs What is EOL software? End of Life (EOL) means the vendor has decided the software in question has reached the end...
SBSCAN SBSCAN is a penetration testing tool specifically designed for the Spring framework, capable of scanning specified sites for Spring Boot sensitive information and verifying related Spring vulnerabilities. Most Comprehensive Dictionary for Sensitive Paths:...
ZeusCloud is an open-source cloud security platform. Discover, prioritize, and remediate your risks in the cloud. Build an asset inventory of your AWS accounts. Continuously monitor your environments for misconfigurations and attack paths. Customize...
RouterOS configuration analyzer to find security misconfigurations and vulnerabilities. Sara does not bypass authentication, exploit vulnerabilities, or alter RouterOS configurations. It works in read-only mode, requiring no administrative privileges. If you are unsure about the interpretation...
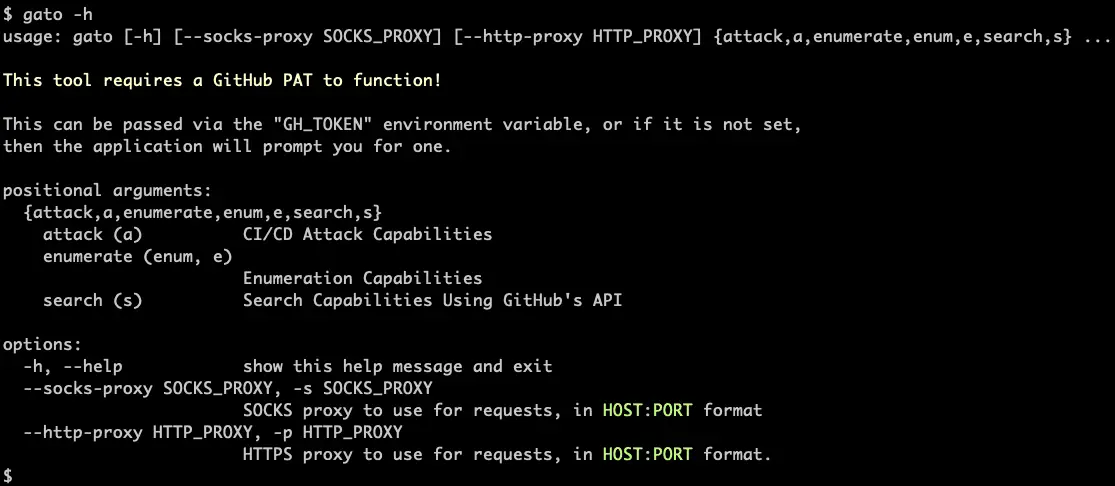
Gato (Github Attack TOolkit) Gato, or GitHub Attack Toolkit, is an enumeration and attack tool that allows both blue teamers and offensive security practitioners to evaluate the blast radius of a compromised personal access...
Twilio Security Scanner A security scanning tool for Twilio accounts that helps detect misconfigurations and security risks, including: Public serverless functions and assets Unencrypted HTTP webhooks in phone numbers and messaging services API keys...