Category: Network Defense
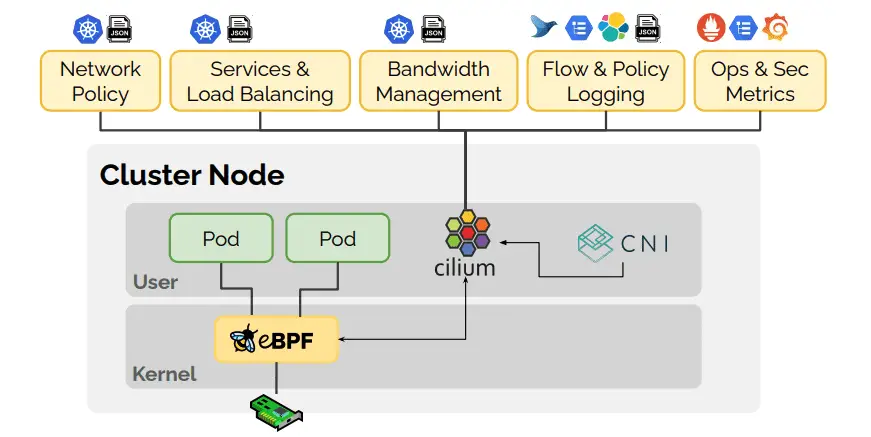
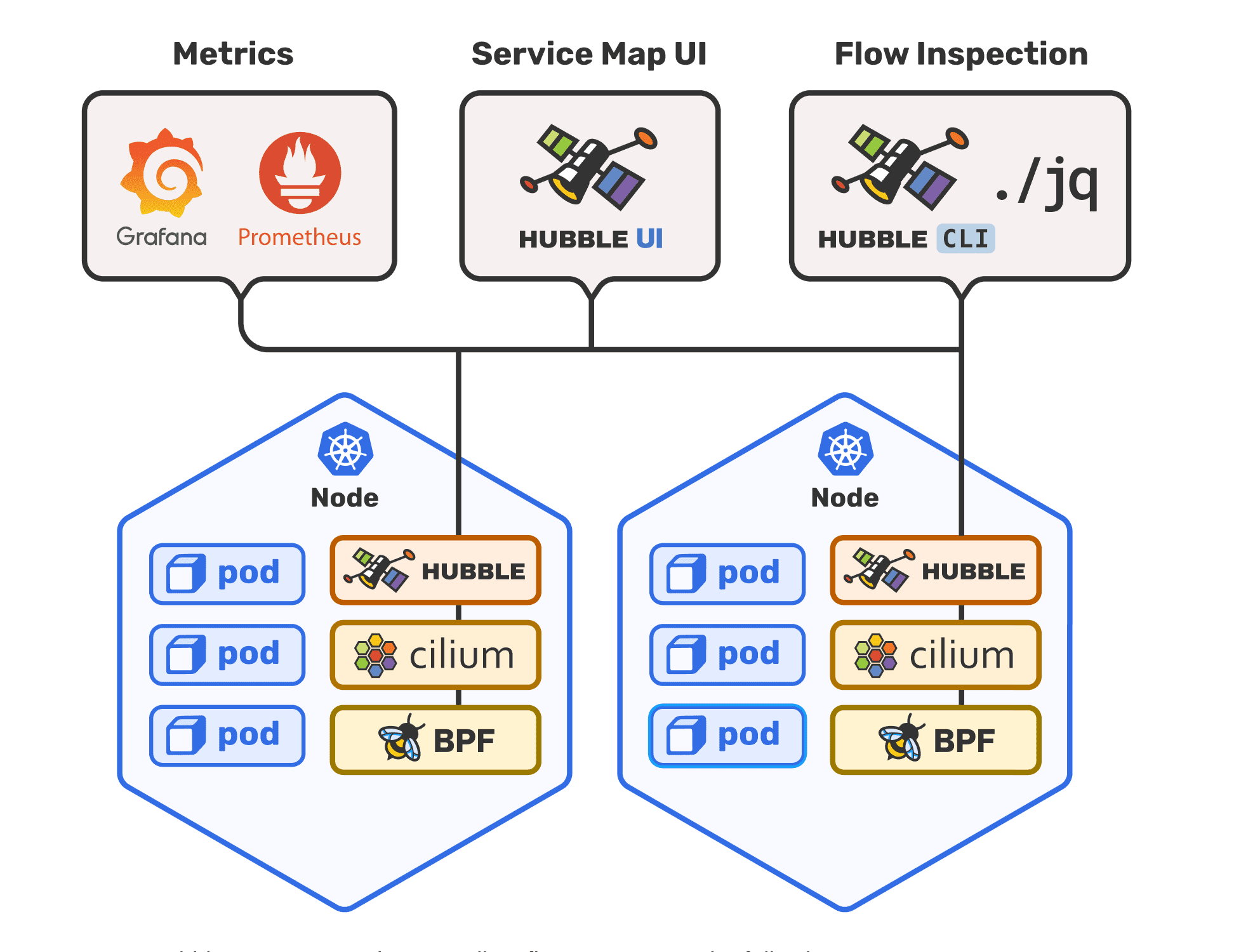
cilium: eBPF-based Networking, Security, and Observability Cilium is open source software for providing and transparently securing network connectivity and load-balancing between application workloads such as application containers or processes. Cilium operates at Layer 3/4...
pmacct pmacct is a small set of multi-purpose passive network monitoring tools. It can account, classify, aggregate, replicate and export forwarding-plane data, ie. IPv4 and IPv6 traffic; collect and correlate control-plane data via BGP...
Open Source API Firewall API Firewall is a high-performance proxy with API request and response validation based on OpenAPI/Swagger schema. It is designed to protect REST API endpoints in cloud-native environments. It provides API...
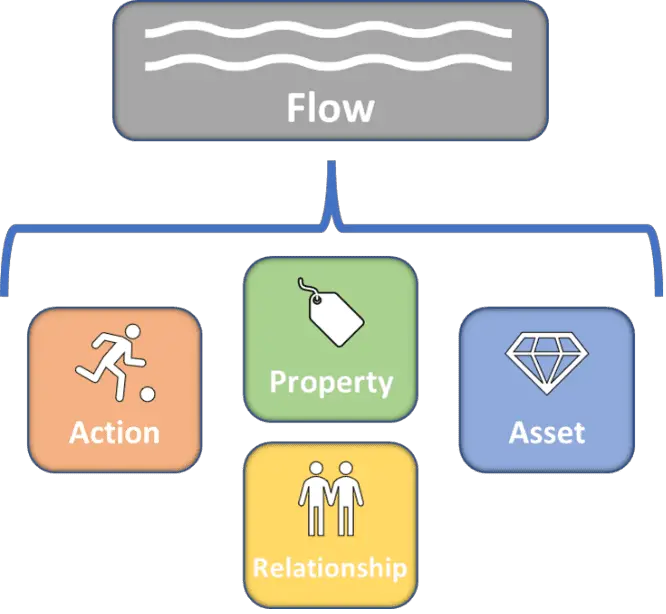
Attack Flow The Attack Flow project helps defenders move from tracking adversary behaviors individually to the sequence of techniques adversaries use to achieve their goals. Understanding the context within those sequences, as well as...
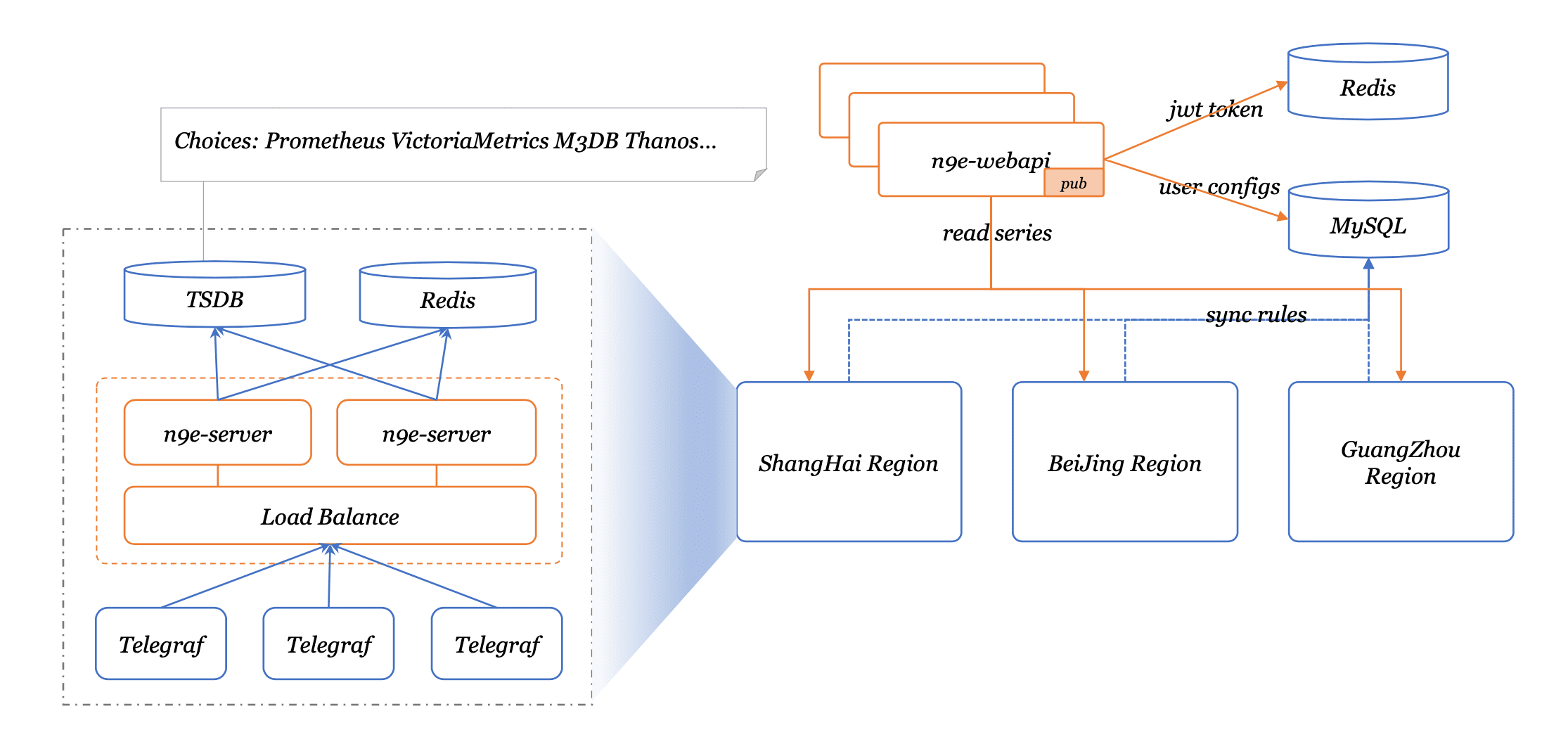
Nightingale Nightingale is an enterprise-level cloud-native monitoring system, which can be used as a drop-in replacement for Prometheus for alerting and management. Nightingale is a cloud-native monitoring system by All-In-On design, that supports enterprise-class...
Stealth Guardian Performing adversary simulation exercises is a time-consuming task, especially when developing new attack mechanisms and testing those against defence systems that have been deployed to the target. With this tool, we have...
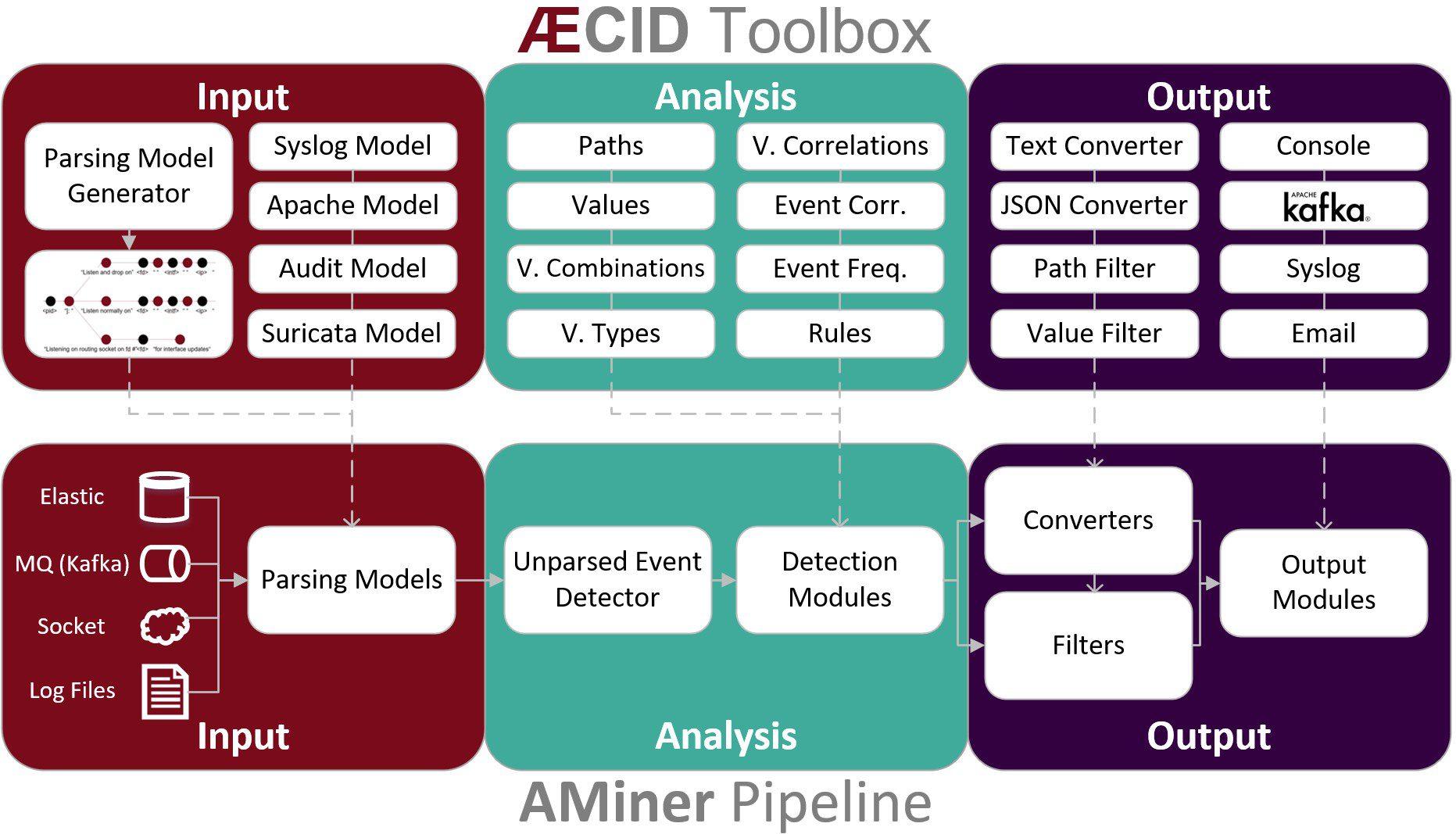
logdata-anomaly-miner This tool parses log data and allows to definition of analysis pipelines for anomaly detection. It was designed to run the analysis with limited resources and the lowest possible permissions to make it...
Hubble Hubble is a fully distributed networking and security observability platform for cloud-native workloads. It is built on top of Cilium and eBPF to enable deep visibility into the communication and behavior of services as well as...
Polaris Securing workloads in Kubernetes is an important part of overall cluster security. The overall goal should be to ensure that containers are running with as minimal privileges as possible. This includes avoiding privilege...
AHWT – another hardening tool for Windows operating systems The program is a script generator with a collection of parameters and recommendations from CIS Benchmarks and DoD STIGs with some adjustments. All parameters are...
openappsec open-appsec (openappsec.io) builds on machine learning to provide preemptive web app & API threat protection against OWASP-Top-10 and zero-day attacks. It can be deployed as an add-on to Kubernetes Ingress, NGINX, Envoy (soon), and API Gateways....
Real Intelligence Threat Analytics Real Intelligence Threat Analytics (RITA) is an open-source framework for network traffic analysis. The framework ingests Bro Logs, and currently supports the following analysis features: Beaconing Detection: Search for signs of...
Snort++ Snort 3 is the next generation Snort IPS (Intrusion Prevention System). This version of Snort++ includes new features as well as all Snort 2.X features and bug fixes for the base version...
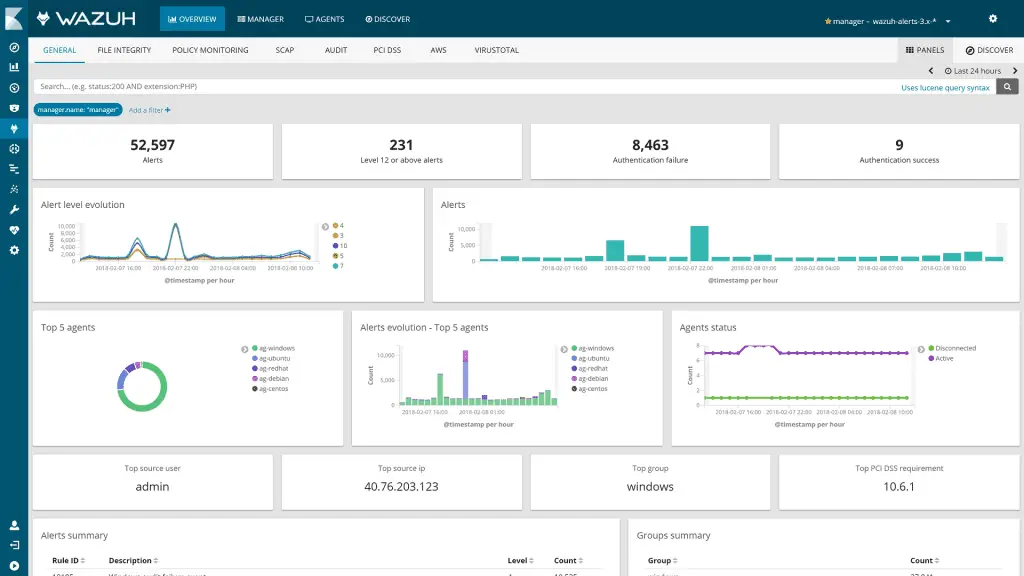
Wazuh Wazuh helps you gain deeper security visibility into your infrastructure by monitoring hosts at an operating system and application level. This solution, based on lightweight multi-platform agents, provides the following capabilities: Log...
Falco Falco is a cloud-native security tool. It provides near real-time threat detection for cloud, container, and Kubernetes workloads by leveraging runtime insights. Falco can monitor events defined via customizable rules from various sources, including the...
ADSpider Tool for monitoring Active Directory changes in real-time without getting all objects. Instead, it uses replication metadata and Update Sequence Number (USN) to filter the current properties of objects. How to use git...