Category: Network Defense
WhoYouCalling Monitors network activity made by a process through the use of Windows Event Tracing (ETW) and Full Packet Capture (FPC). Filters a generated .pcap file with BPF based on the detected network activity made by...
What is Acra Acra helps you easily secure your databases in distributed, microservice-rich environments. It allows you to selectively encrypt sensitive records with strong multi-layer cryptography, detect potential intrusions and SQL injections and cryptographically compartmentalize...
LuLu is the free open-source macOS firewall that aims to block unauthorized (outgoing) network traffic unless explicitly approved by the user: Full details and usage instructions can be found here. Feature 100% free As...
IPBan Service IPBan is a simple yet powerful solution for Windows and Linux to prevent botnets and hackers from breaching your computers. Protecting your security is the primary goal, but there are also performance...
The Update Framework (TUF) The Update Framework (TUF) is written in Python and intended to conform to version 1.0 of the TUF specification. This implementation is in use in production systems but is also...
Conjur Conjur provides secrets management and machine identity for modern infrastructure: Machine Authorization Markup Language (“MAML”), a role-based access policy language to define system components & their roles, privileges, and metadata A REST web...
What is Suricata The Suricata Engine is an Open Source Next Generation Intrusion Detection and Prevention Engine. This engine is not intended to just replace or emulate the existing tools in the industry but...
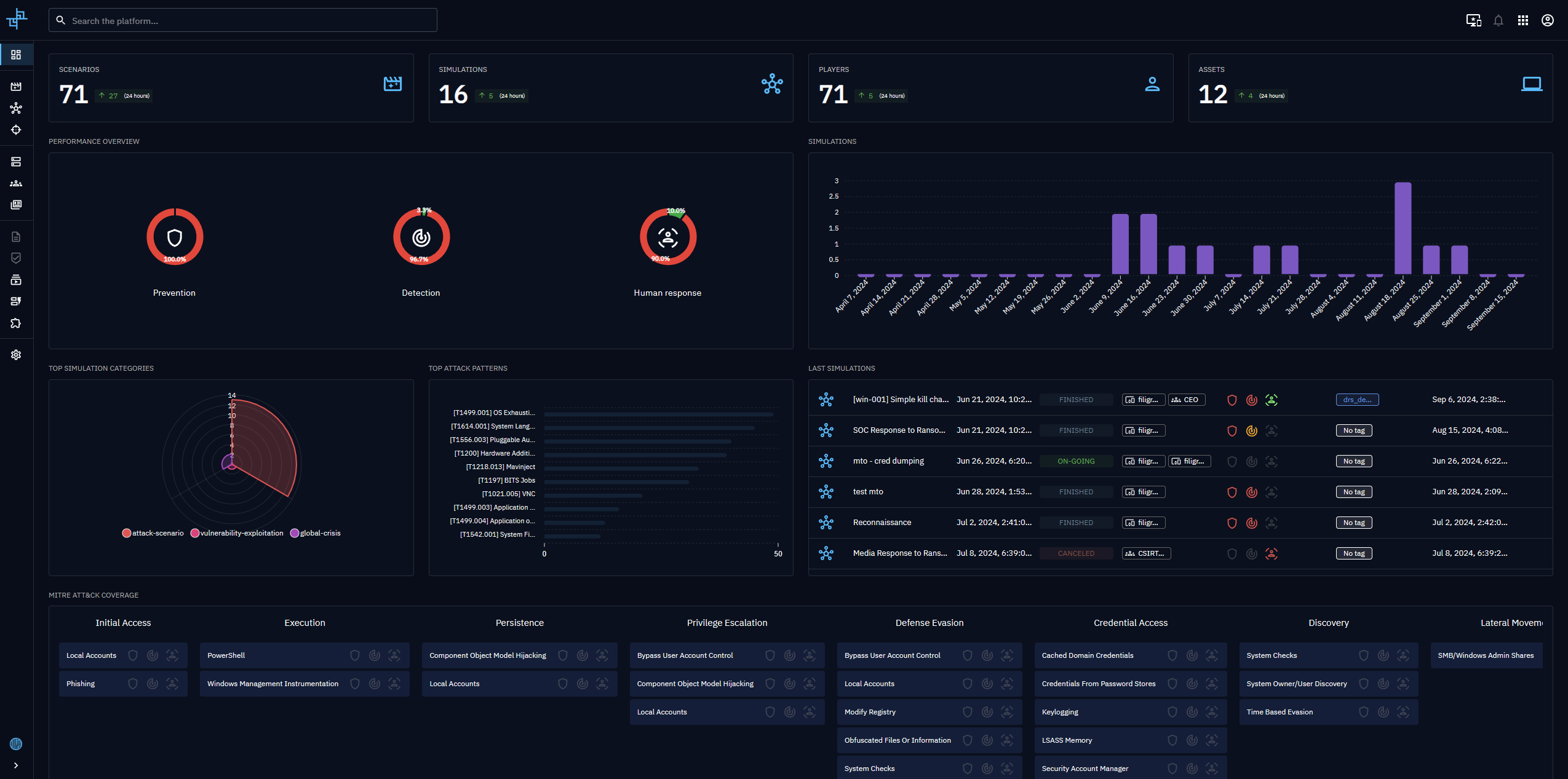
OpenBAS OpenBAS is an open-source platform allowing organizations to plan, schedule, and conduct cyber adversary simulation campaigns and tests. The goal is to create a powerful, reliable, and open-source tool to effectively plan and...
Cloudsplaining Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report. Cloudsplaining identifies violations of least privilege in AWS IAM policies and generates a...
grapheneX In computing, hardening is usually the process of securing a system by reducing its surface of vulnerability, which is larger when a system performs more functions; in principle a single-function system is more...
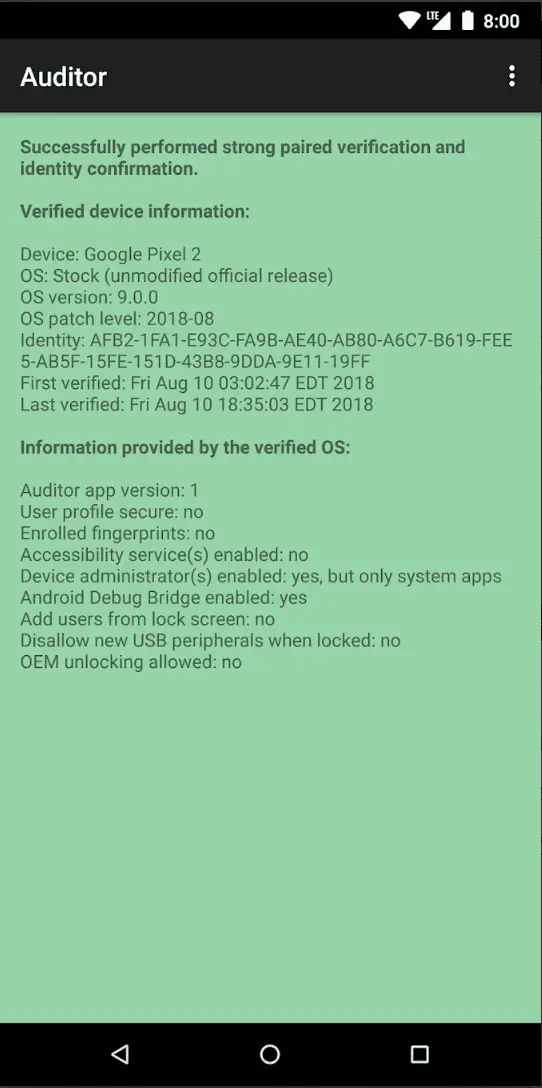
The Auditor app uses hardware-based security features to validate the identity of a device, along with the authenticity and integrity of the operating system. It ensures the device is running a verified operating system with a...
NamedPipeMaster NamedPipeMaster is a versatile tool for analyzing and monitoring in named pipes. It includes Ring3NamedPipeConsumer for direct server interaction, Ring3NamedPipeMonitor for DLL-based API hooking and data collection, and Ring0NamedPipeFilter for comprehensive system-wide monitoring....
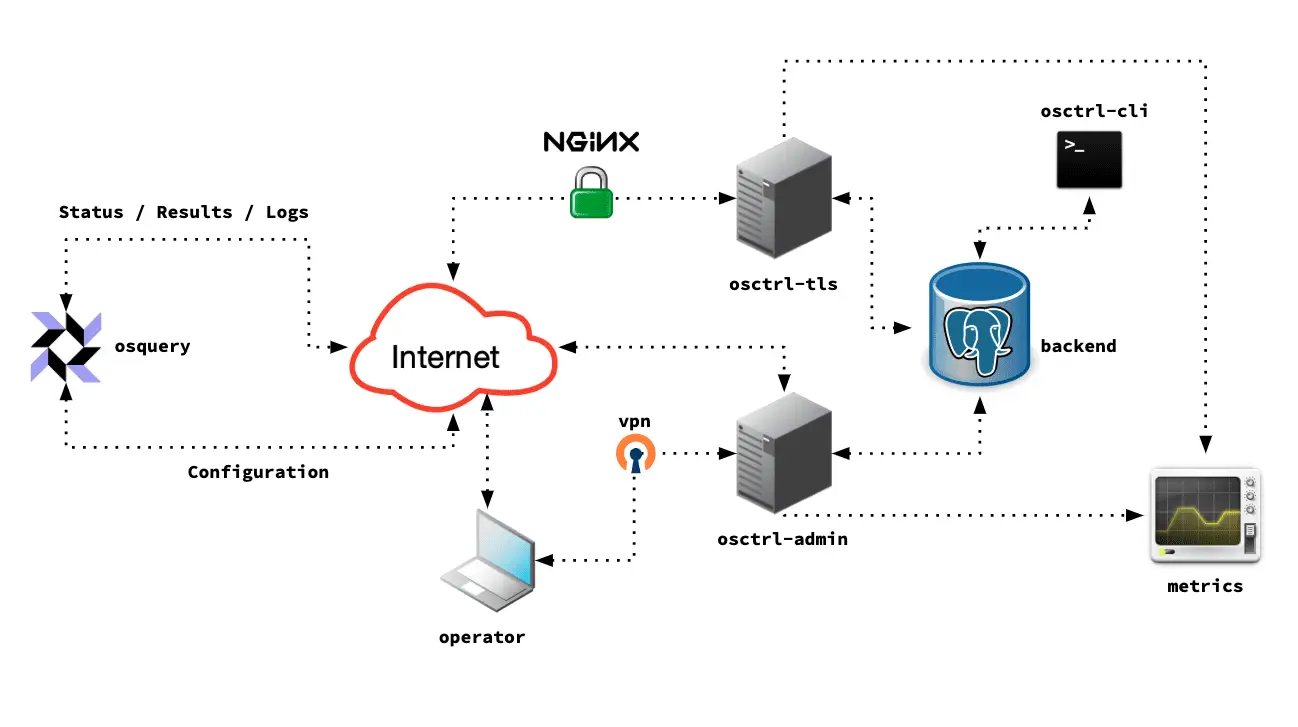
osctrl osctrl is a fast and efficient osquery management solution, implementing its remote API as a TLS endpoint. With osctrl, you can monitor all your systems running osquery, distribute its configuration fast, collect all the status and result logs,...
NetAlertX – Network scanner & notification framework Get visibility of what’s going on on your WIFI/LAN network. Schedule scans for devices, port changes and get alerts if unknown devices or changes are found. Write...
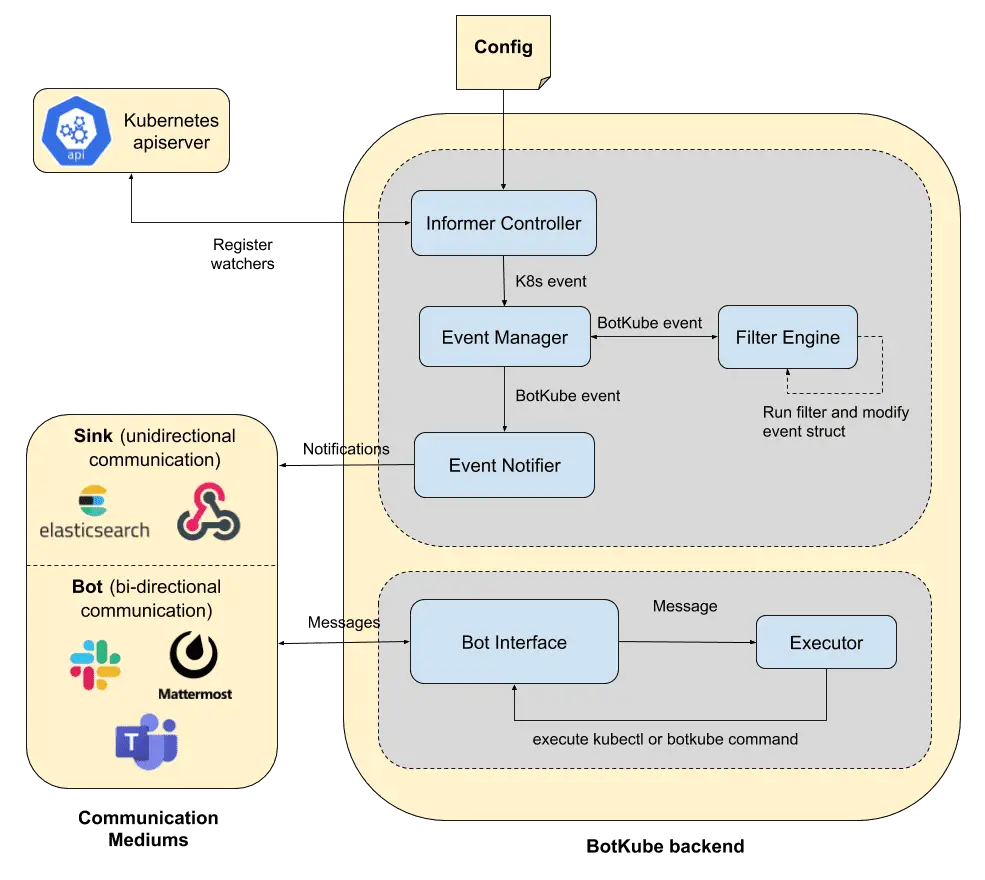
BotKube BotKube integration with Slack, Mattermost, or Microsoft Teams helps you monitor your Kubernetes cluster, debug critical deployments, and gives recommendations for standard practices by running checks on the Kubernetes resources. You can also ask BotKube to execute...
The Bastion Bastions are a cluster of machines used as the unique entry point by operational teams (such as sysadmins, developers, database admins, …) to securely connect to devices (servers, virtual machines, cloud instances,...