Category: Network Defense
eHIDS A Linux Host-based Intrusion Detection System based on eBPF. Implementations & Functionalities: TCP network data capture UDP network data capture DNS information capture in uprobe mode Process data capture Uprobe way to achieve...
SecuSphere Welcome to SecuSphere, your one-stop solution for all DevSecOps needs. Our centralized platform is expertly designed to manage and optimize your vulnerability management, CI/CD pipeline integration, security assessments, and DevSecOps practices. SecuSphere is...
CureIAM Clean up of over permissioned IAM accounts on GCP infra in an automated way CureIAM is an easy-to-use, reliable, and performant engine for Least Privilege Principle Enforcement on GCP cloud infra. It enables...
LDAP Watchdog LDAP Watchdog is a tool designed to monitor and record changes in an LDAP directory in real time. It provides a mechanism to track and visualize modifications, additions, and removals to user...
RequestShield RequestShield is a 100% Free and Open Source tool designed to analyze HTTP access.logs and identify suspicious HTTP requests and potential security threats. It uses factors like geolocation, abuse history, request volume, and...
tetragon Cilium’s new Tetragon component enables powerful real-time, eBPF-based Security Observability and Runtime Enforcement. Tetragon detects and is able to respond in real-time to security-significant events, such as Process execution events Changes to privileges...
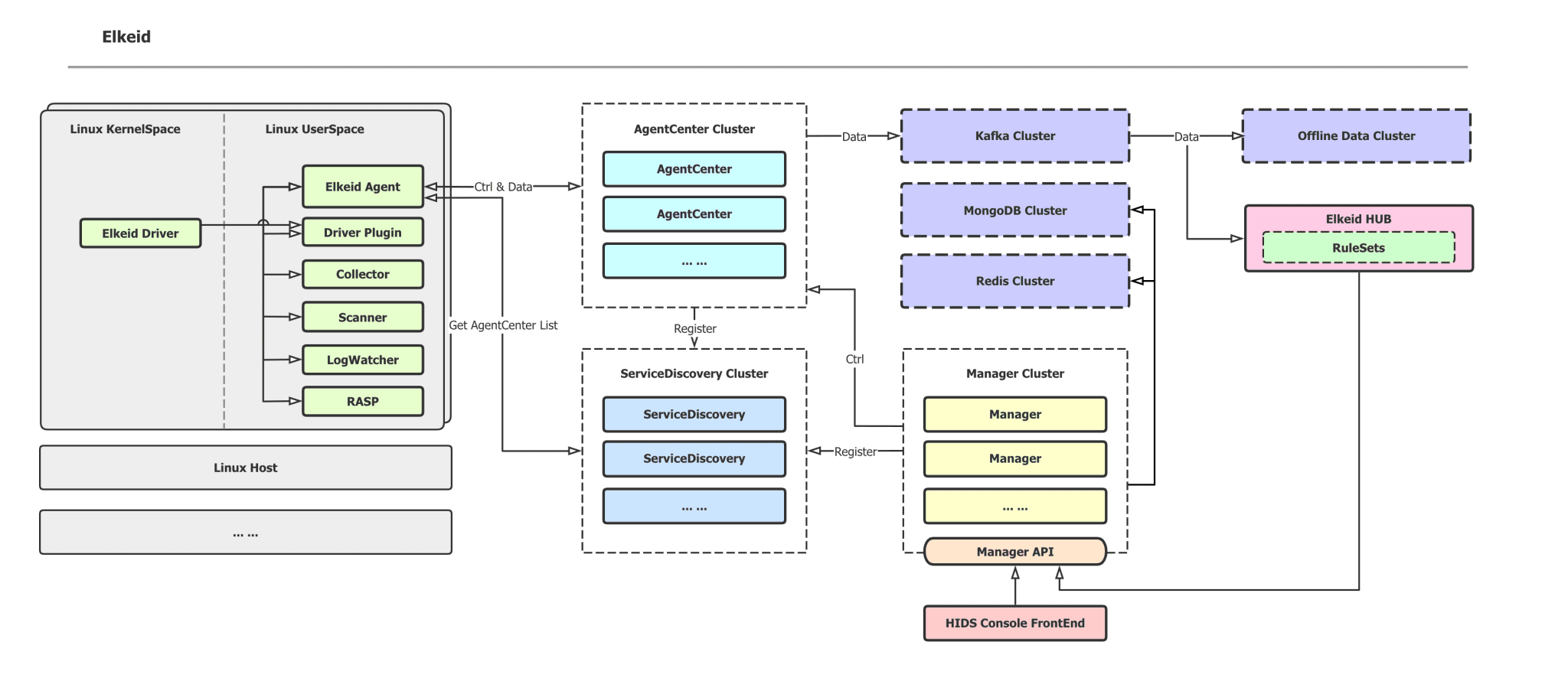
Elkeid Elkeid is a Cloud-Native Host-Based Intrusion Detection solution project to provide next-generation Threat Detection and Behavior Audition with modern architecture. Elkeid Agent Linux userspace agent, responsible for managing various plugins, and communication with...
hcltm Threat Modeling with HCL Overview There are many different ways in which a threat model can be documented. From a simple text file to more in-depth word documents, to fully instrumented threat models...
lynis Lynis is a security auditing tool for systems based on UNIX like Linux, macOS, BSD, and others. It performs an in-depth security scan and runs on the system itself. The primary goal is to test...
ntopng ntopng is the next-generation version of the original ntop, a network traffic probe that shows the network usage, similar to what the popular top Unix command does. ntopng is based on libpcap and...
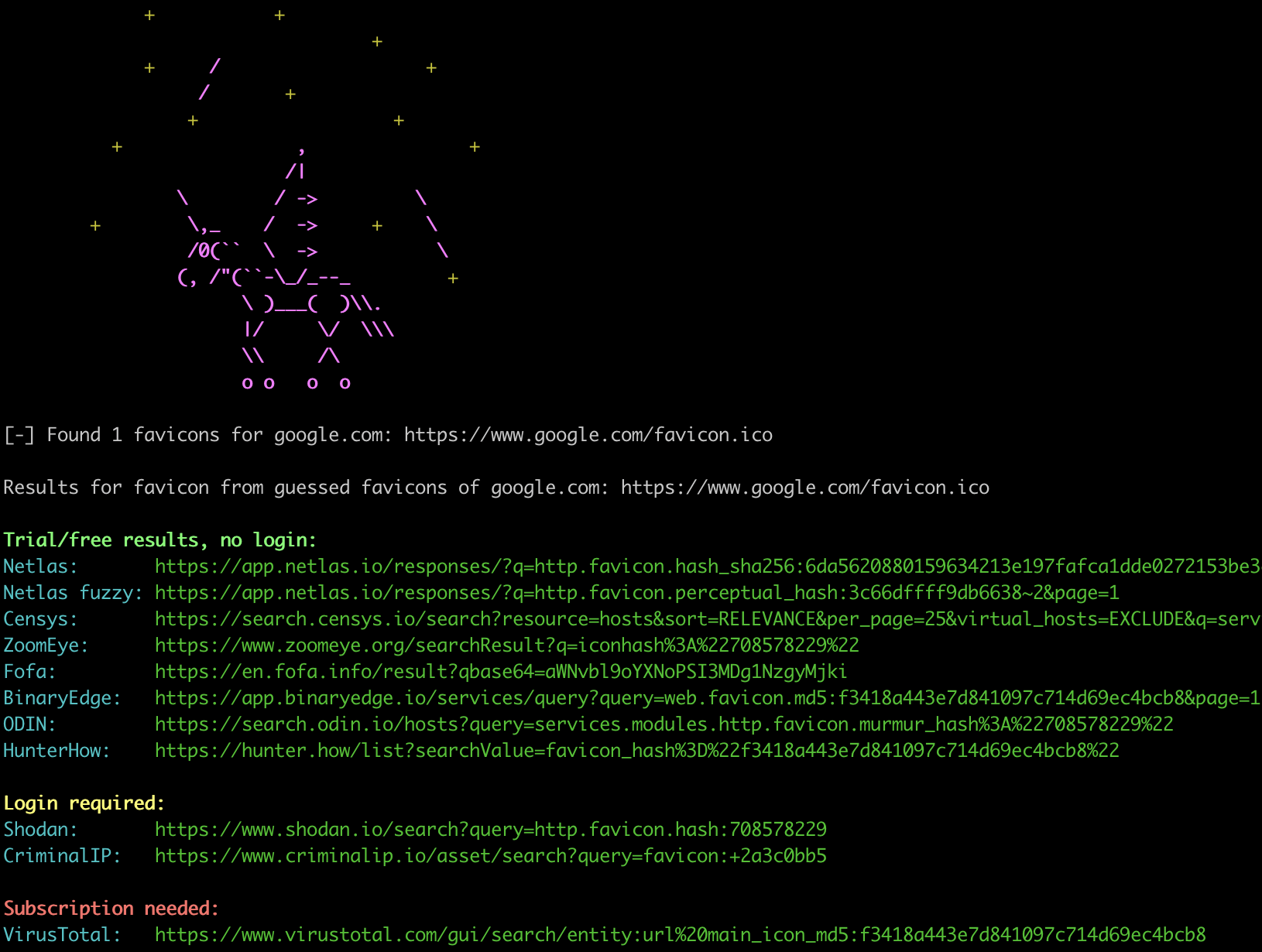
FAVICORN All-sources tool to search websites by favicons. Favicorn takes a favicon and provides search result links across 10 platforms, and not only. Supported platforms Name Login required ZoomEye yes Shodan yes Fofa no...
checksec Checksec is a bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source). It was originally written by Tobias Klein. The checksec tool can be used...
Zeek Network Security Monitor Zeek is a powerful framework for network analysis and security monitoring. It is a powerful system that on top of the functionality it provides out of the box, also offers...
Cacti Cacti is a complete network graphing solution designed to harness the power of RRDTool‘s data storage and graphing functionality. Cacti provide a fast poller, advanced graph templating, multiple data acquisition methods, and user...
NETworkManager Connect and manage remote systems with Remote Desktop, PowerShell, PuTTY, TigerVNC or AWS (Systems Manager) Session Manager. Analyze and troubleshoot your network and systems with features such as the WiFi Analyzer, IP Scanner,...
AIL framework AIL framework – Framework for Analysis of Information Leaks AIL is a modular framework to analyse potential information leaks from unstructured data sources like pastes from Pastebin or similar services or unstructured...