Category: Network Attacks
SOAPHound SOAPHound is a .NET data collector tool, which collects Active Directory data via the Active Directory Web Services (ADWS) protocol. SOAPHound is an alternative to several open-source security tools that are commonly used...
AngryOxide AngryOxide was developed as a way to learn Rust, netlink, kernel sockets, and WiFi exploitation all at once. The overall goal of this tool is to provide a single-interface survey capability with advanced...
pmkidcracker This program is a tool written in Python to recover the pre-shared key of a WPA2 WiFi network without any de-authentication or requiring any clients to be on the network. It targets the...
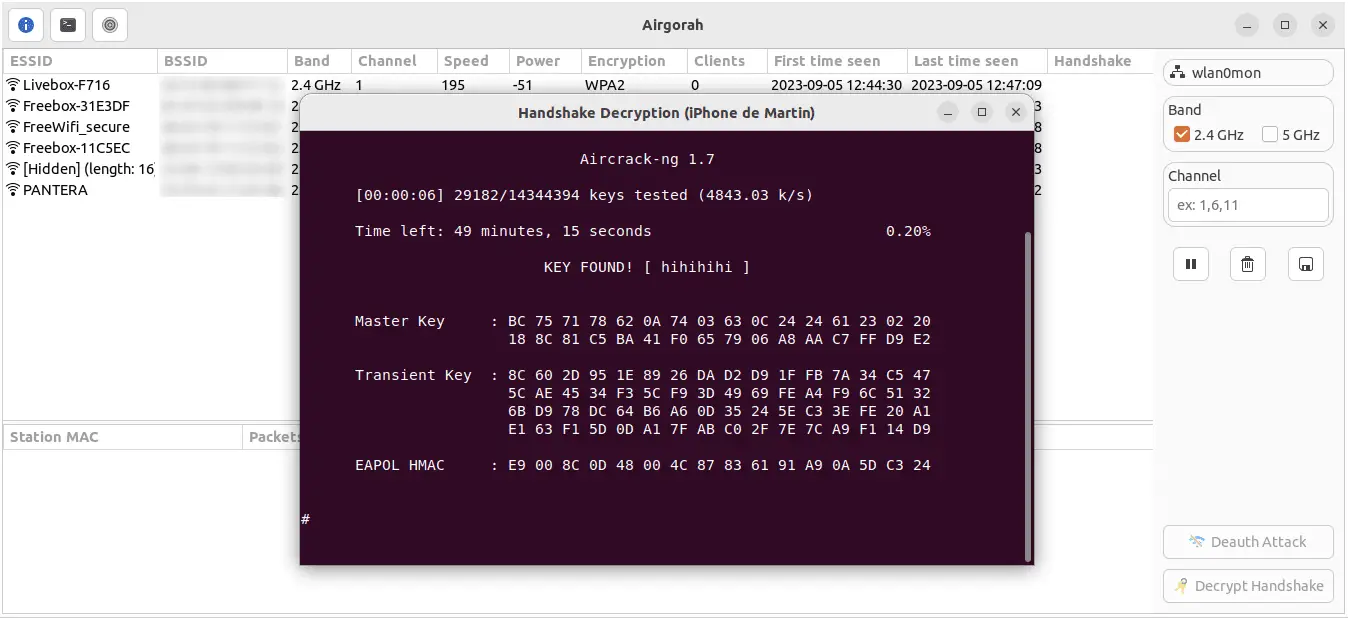
airgorah Airgorah is a WiFi auditing software that can discover the clients connected to an access point, perform deauthentication attacks against specific clients or all the clients connected to it, capture WPA handshakes, and crack...
legba Legba is a multiprotocol credentials bruteforcer / password sprayer and enumerator built with Rust and the Tokio asynchronous runtime in order to achieve better performances and stability while consuming fewer resources than similar...
WEF – WiFi Exploitation Framework This project started over 2021 as a personal tool to easily audit networks without writing long commands or setting all values one by one, in order to automate the...
bettercap bettercap is a powerful, easily extensible, and portable framework written in Go which aims to offer to security researchers, red teamers and reverse engineers an easy to use, all-in-one solution with all the features they...
chisel Chisel is a fast TCP tunnel, transported over HTTP, secured via SSH. Single executable including both client and server. Written in Go (golang). It is mainly useful for passing through firewalls, though it...
Inveigh Inveigh is a cross-platform .NET IPv4/IPv6 machine-in-the-middle tool for penetration testers. This repo contains the primary C# version as well as the legacy PowerShell version. Overview Inveigh conducts spoofing attacks and hash/credential captures...
What is Impacket? Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and for some protocols (e.g. SMB1-3 and MSRPC)...
sniffglue sniffglue is a network sniffer written in rust. Network packets are parsed concurrently using a thread pool to utilize all cpu cores. Project goals are that you can run sniffglue securely on untrusted...
msInvader msInvader is an adversary simulation tool built for blue teams, designed to simulate adversary techniques within M365 and Azure environments. Its purpose is to generate attack telemetry that aids teams in building, testing,...
Snaffler Snaffler is a tool for pentesters to help find delicious candy needles (creds mostly, but it’s flexible) in a bunch of horrible boring haystacks (a massive Windows/AD environment). It might also be useful for other...
Responder an LLMNR, NBT-NS, and MDNS poisoner. It will answer to specific NBT-NS (NetBIOS Name Service) queries based on their name suffix (see: http://support.microsoft.com/kb/163409). By default, the tool will only answer to File Server Service request, which...
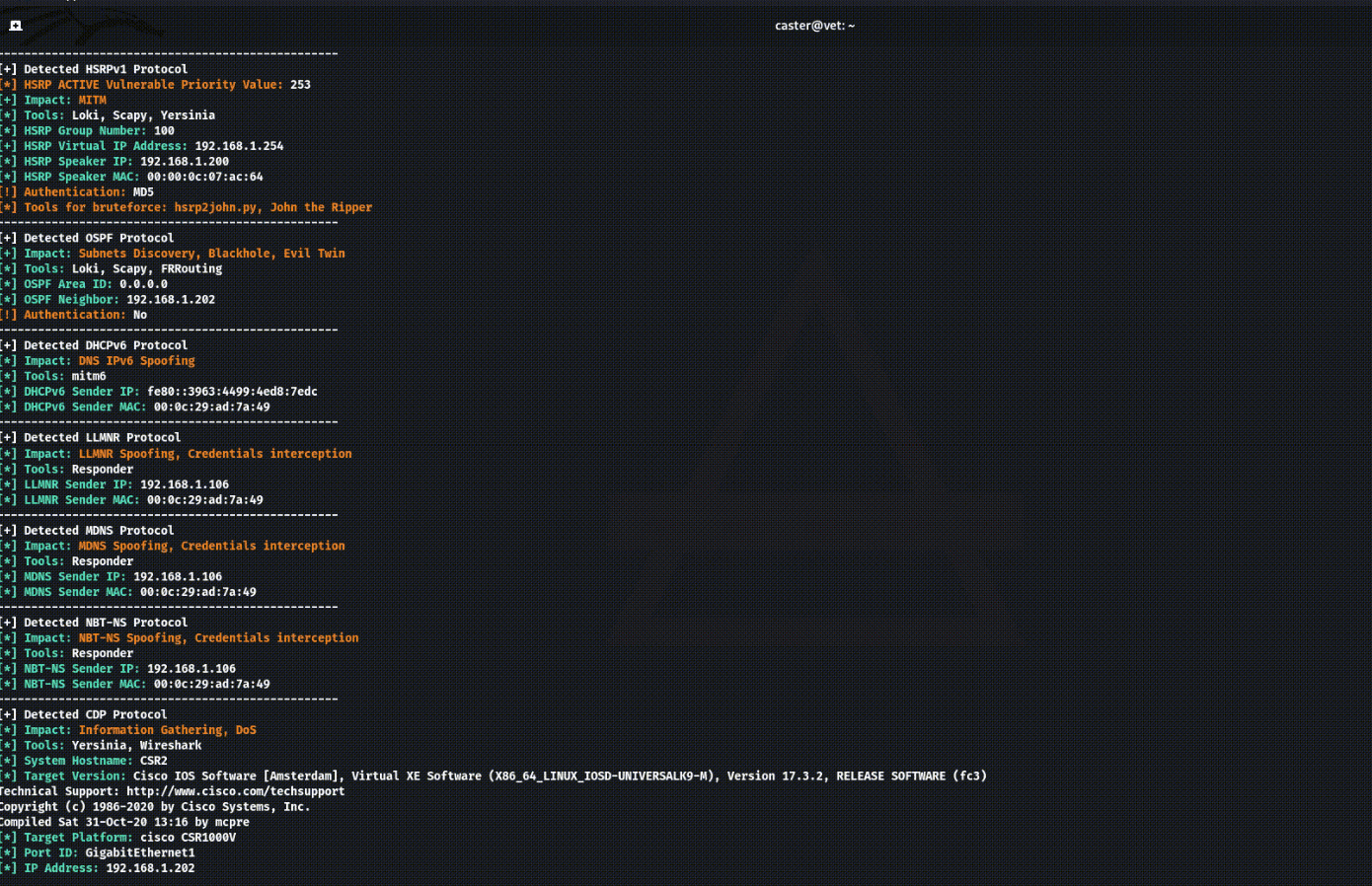
Above Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security professionals. Mechanics Above is an invisible network sniffer for finding vulnerabilities in network equipment. It is based entirely on...
gost – GO Simple Tunnel Features Listening on multiple ports Multi-level forward proxies – proxy chain Standard HTTP/HTTPS/HTTP2/SOCKS4(A)/SOCKS5 proxy protocols support Probing resistance support for web proxy TLS encryption via negotiation support for SOCKS5...