Varalyze: The All-in-One Threat Intelligence Suite Revolutionizing Security Triage
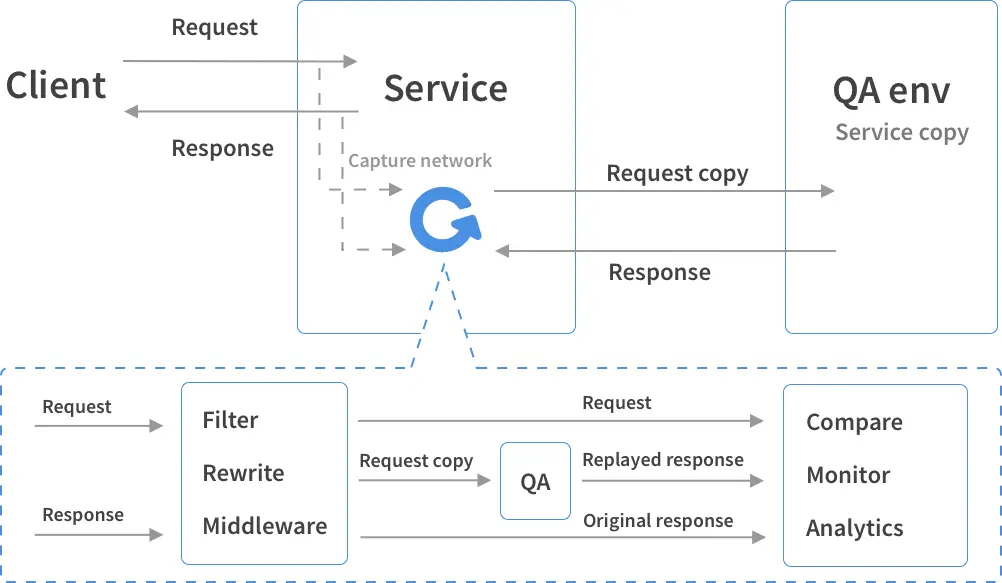
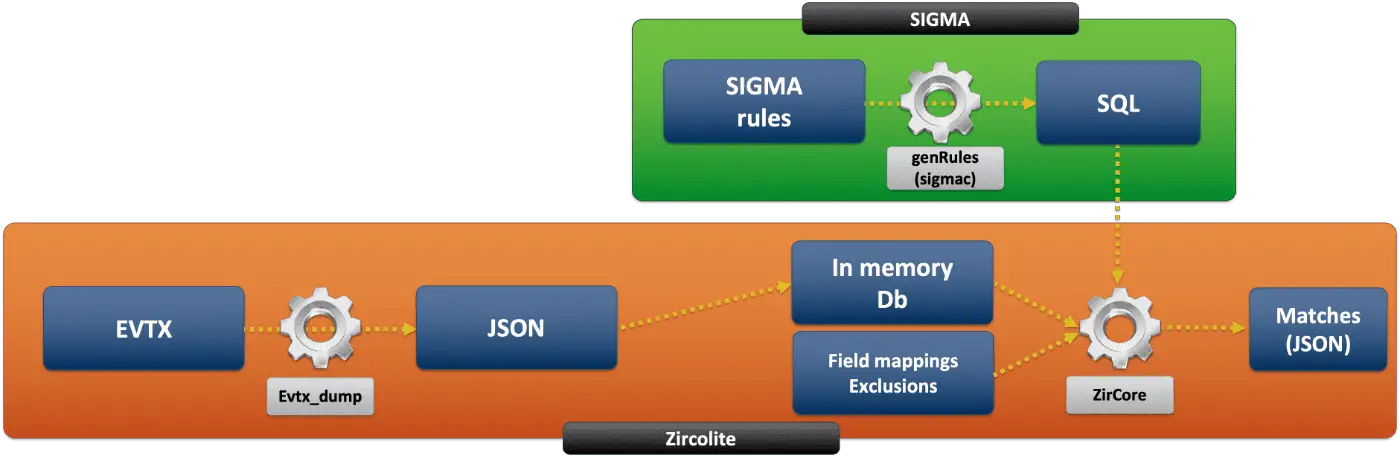
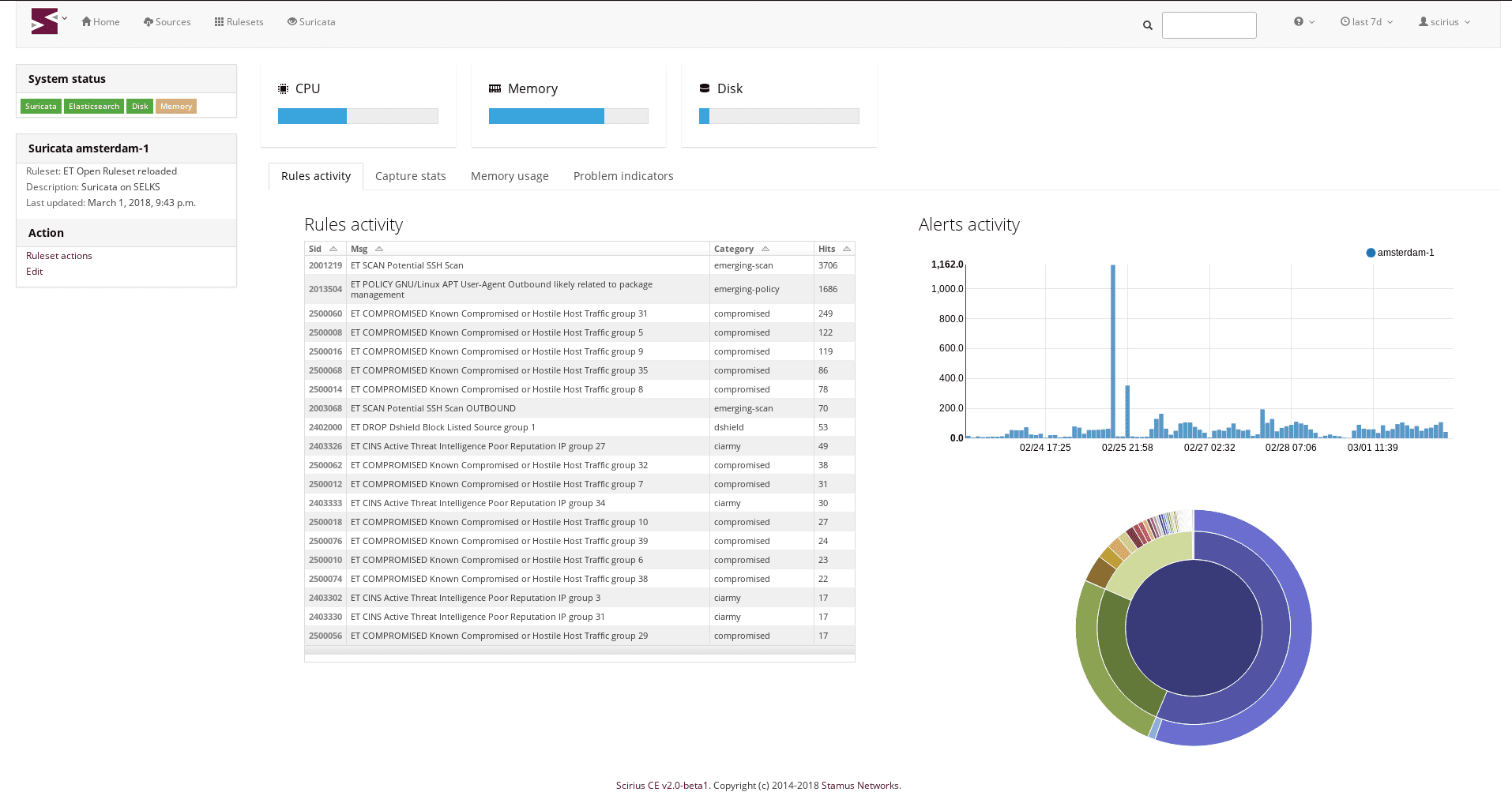
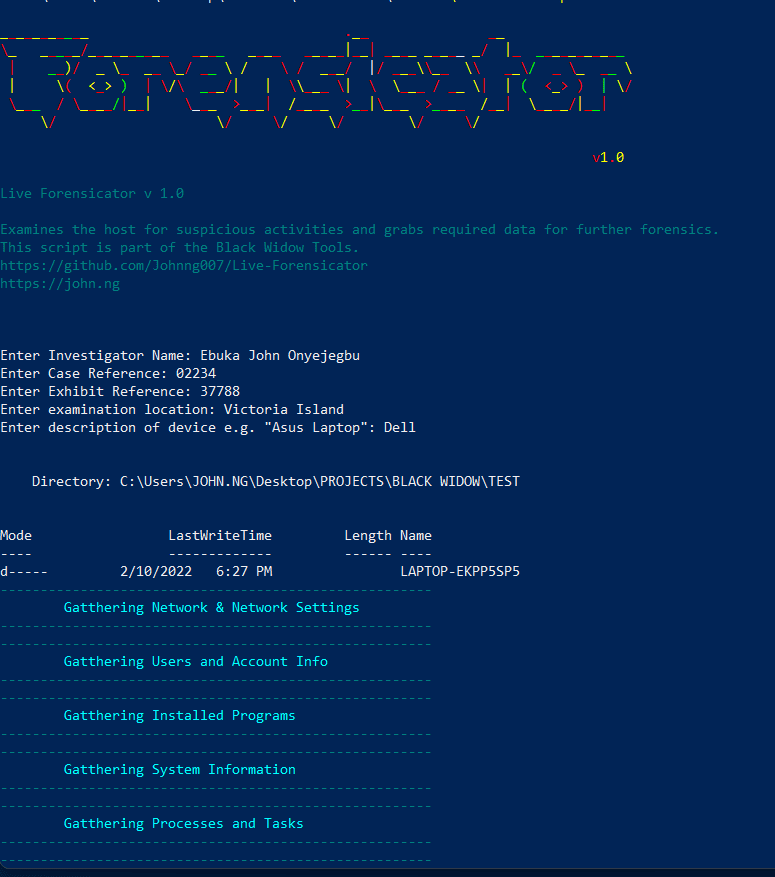
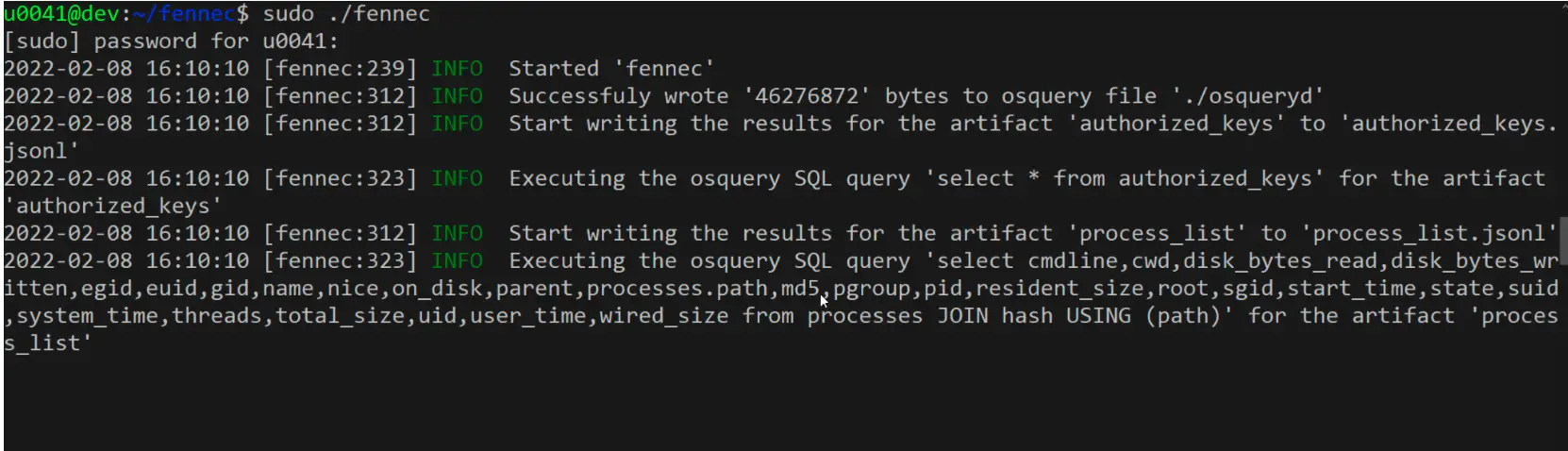
Varalyze is a threat intelligence tool suite that combines a diverse range of web-based applications into one seamless platform through the use of APIs and python libraries. This allows for comprehensive security event triaging due...