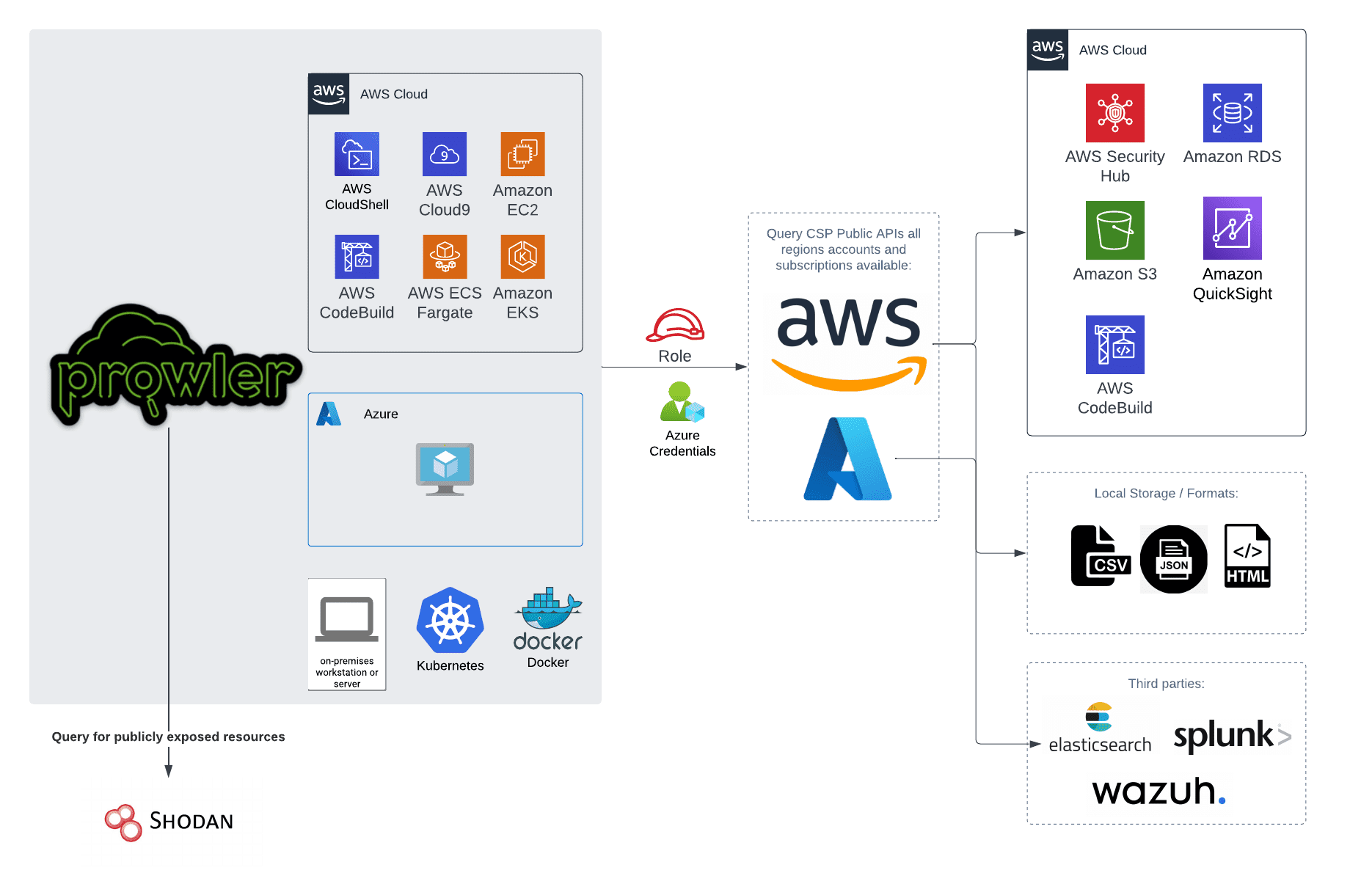
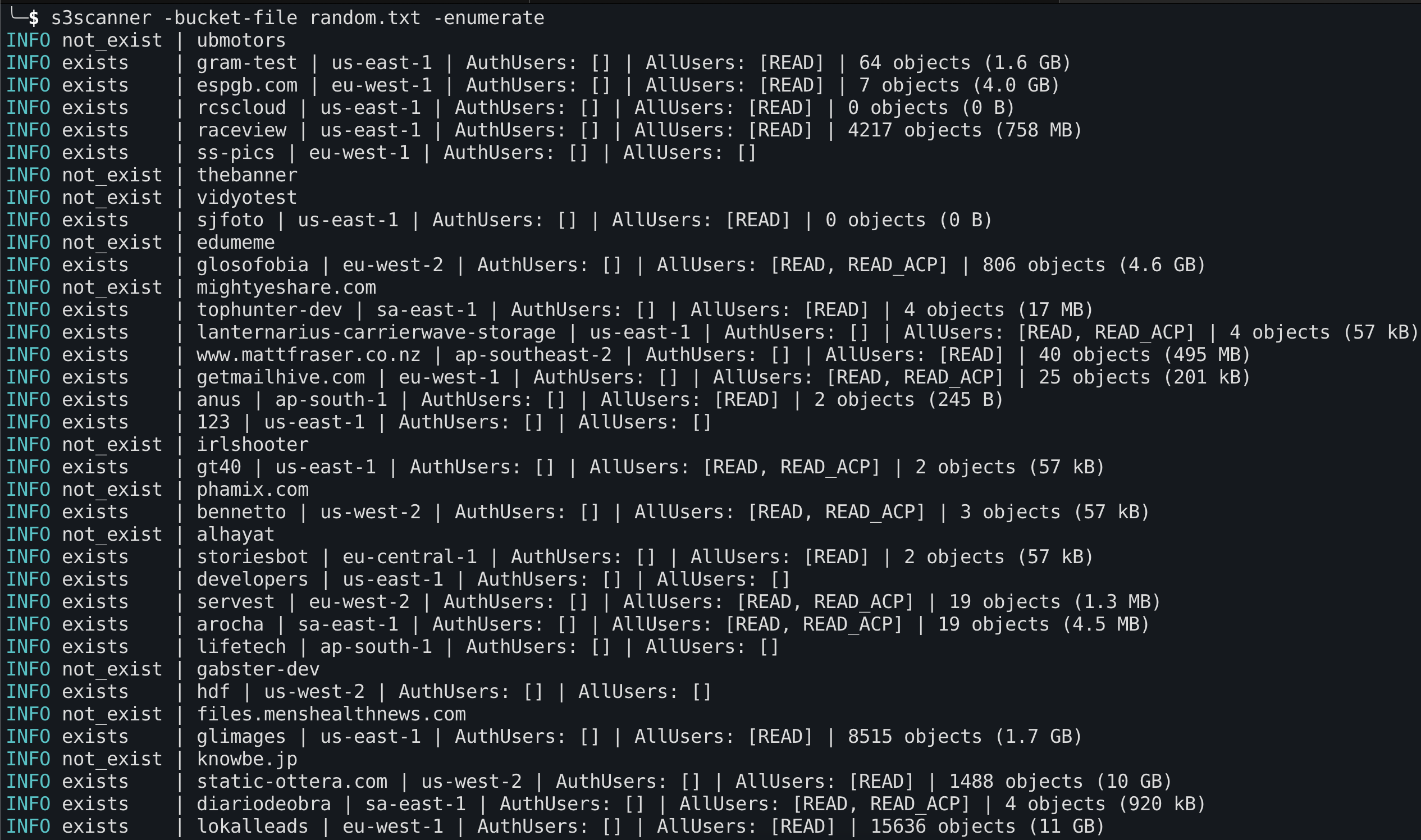
Apache Tomcat Scanner: scan for Apache Tomcat server vulnerabilities
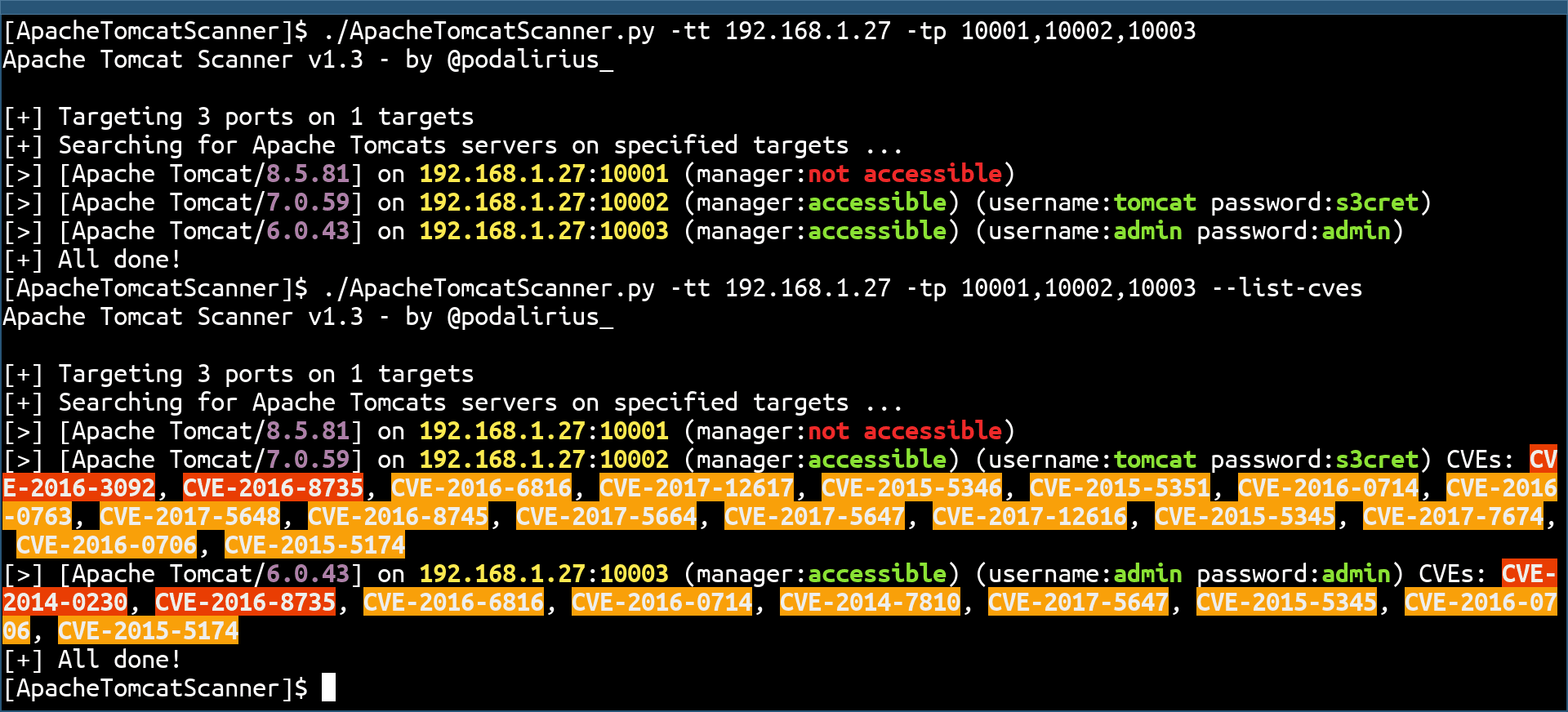
Apache Tomcat Scanner A python script to scan for Apache Tomcat server vulnerabilities. Features Multithreaded workers to search for Apache tomcat servers. Multiple target sources accepted: Retrieving list of computers from a Windows domain...