Category: Ethical Hacking
Native Bypass CredGuard NativeBypassCredGuard is a tool designed to bypass Credential Guard by patching WDigest.dll using only NTAPI functions (exported by ntdll.dll). It is available in two flavours: C# and C++. The tool locates...
Phantun A lightweight and fast UDP to TCP obfuscator. Phantun is a project that obfuscated UDP packets into TCP connections. It aims to achieve maximum performance with minimum processing and encapsulation overhead. It is...
Donut Donut is a shellcode generation tool that creates x86 or x64 shellcode payloads from .NET Assemblies. This shellcode may be used to inject the Assembly into arbitrary Windows processes. Given an arbitrary .NET...
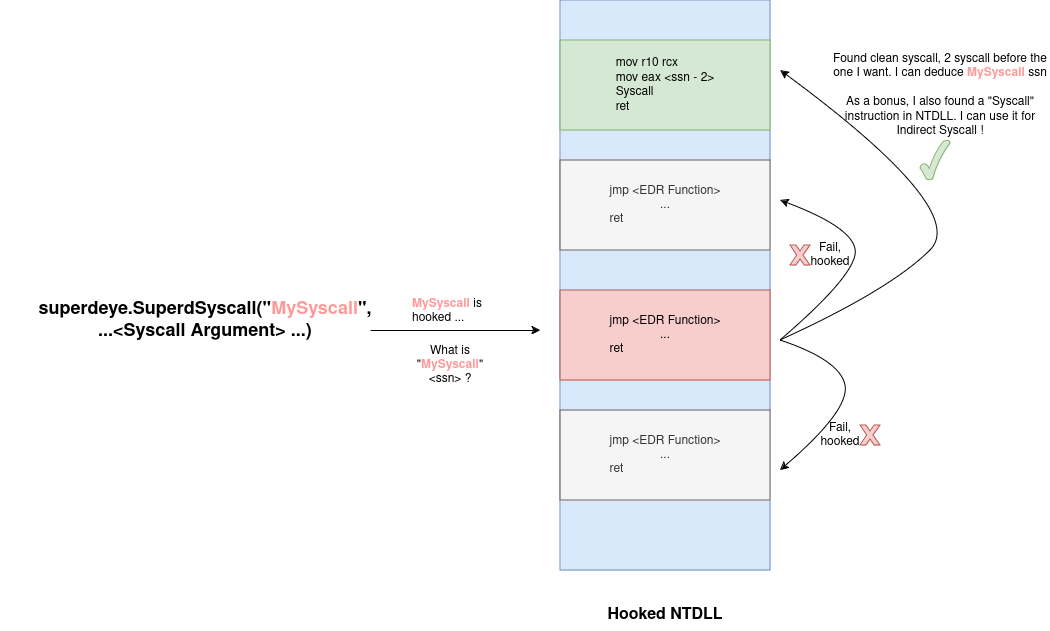
SuperdEye SuperdEye is the implementation of HellHall (a revised version of TartarusGate) in pure Go and Go Assembler. The purpose is to scan hooked NTDLL and retrieve the Syscall number to then do an...
Chisel-Strike A .NET XOR encrypted cobalt strike aggressor implementation for the chisel to utilize faster proxy and advanced socks5 capabilities. Why write this? In my experience, I found socks4/socks4a proxies quite slow in comparison...
autobloody autobloody is a tool to automatically exploit Active Directory privilege escalation paths shown by BloodHound combining pathgen.py and autobloody.py. This tool automates the AD privesc between two AD objects, the source (the one we own) and...
bloodyAD BloodyAD is an Active Directory Privilege Escalation Framework. This tool can perform specific LDAP/SAMR calls to a domain controller in order to perform AD privesc. It supports authentication using cleartext passwords, pass-the-hash, pass-the-ticket,...
Muraena Muraena is an almost-transparent reverse proxy aimed at automating phishing and post-phishing activities. The tool re-implements the 15-years old idea of using a custom reverse proxy to dynamically interact with the origin to be...
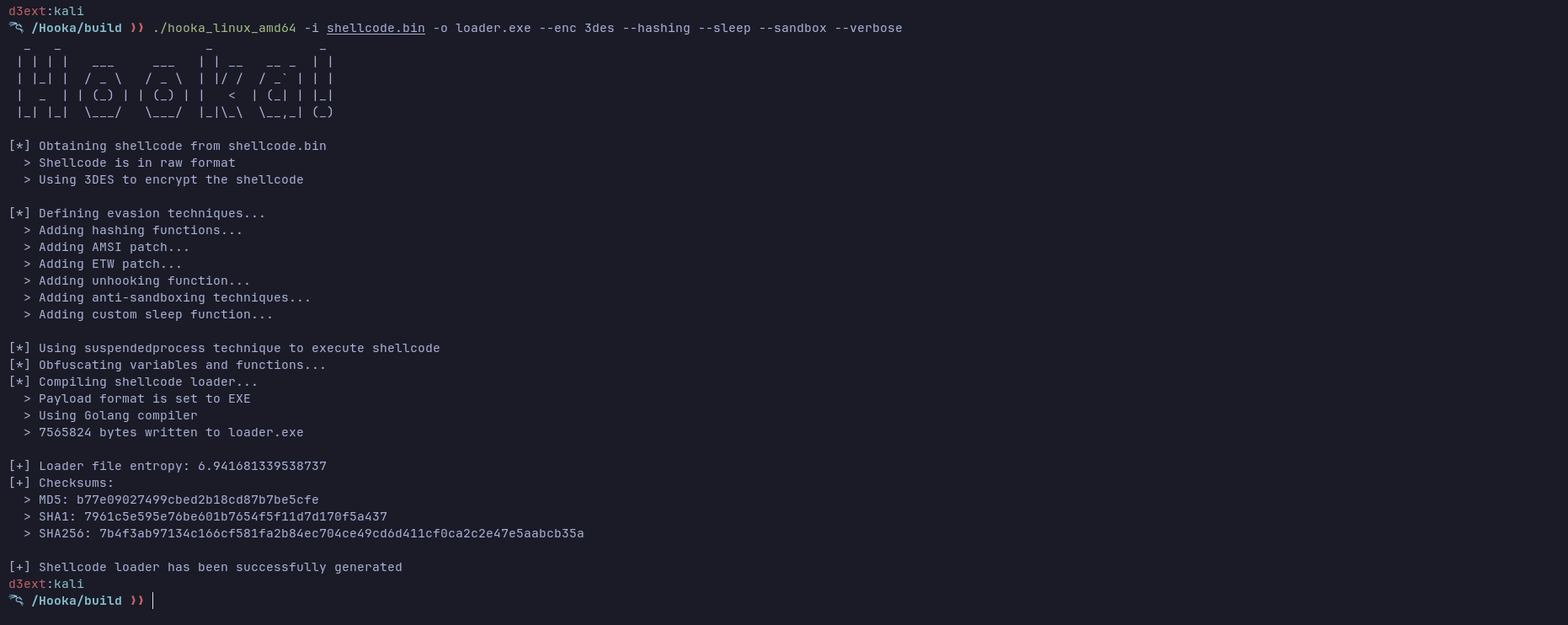
Hooka Hooka is able to generate shellcode loaders with multiple capabilities. It is also based on other tools like BokuLoader, Freeze or Shhhloader, and it tries to implement more evasion features. Why in Golang? Why not? Feature This...
WEF – WiFi Exploitation Framework This project started over 2021 as a personal tool to easily audit networks without writing long commands or setting all values one by one, in order to automate the...
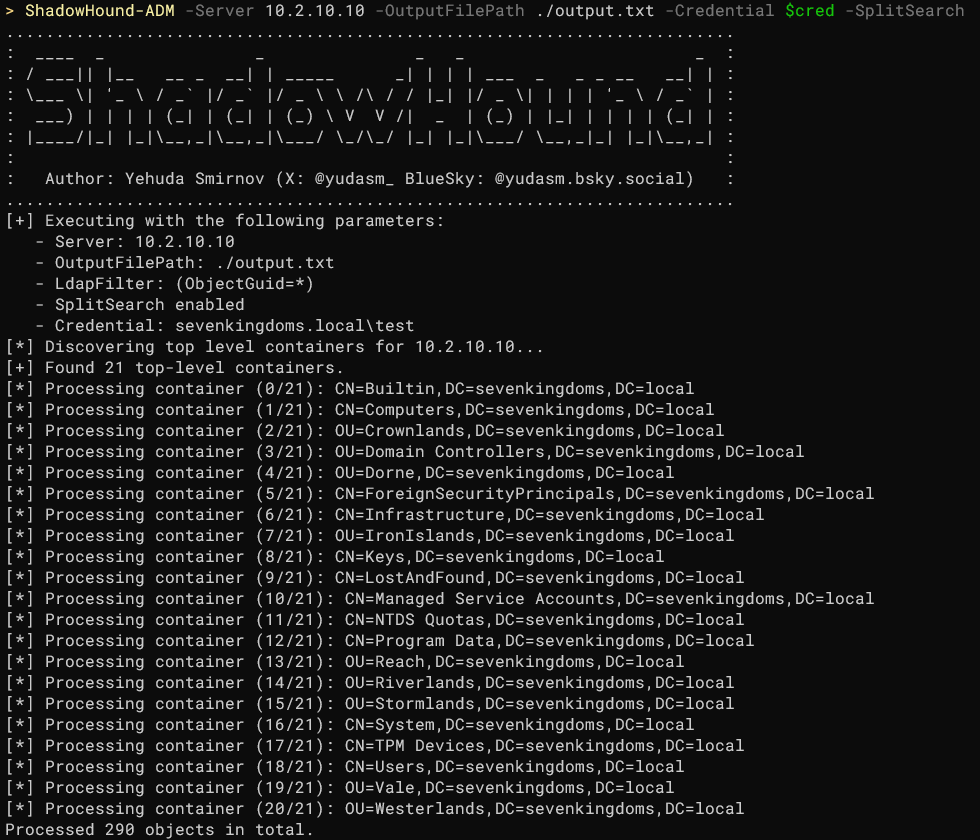
ShadowHound ShadowHound is a set of PowerShell scripts for Active Directory enumeration without the need for introducing known-malicious binaries like SharpHound. It leverages native PowerShell capabilities to minimize detection risks and offers two methods...
The Exegol project Exegol is a community-driven hacking environment, powerful and yet simple enough to be used by anyone in day to day engagements. Script kiddies use Kali Linux, real pentesters use Exegol, megachads...
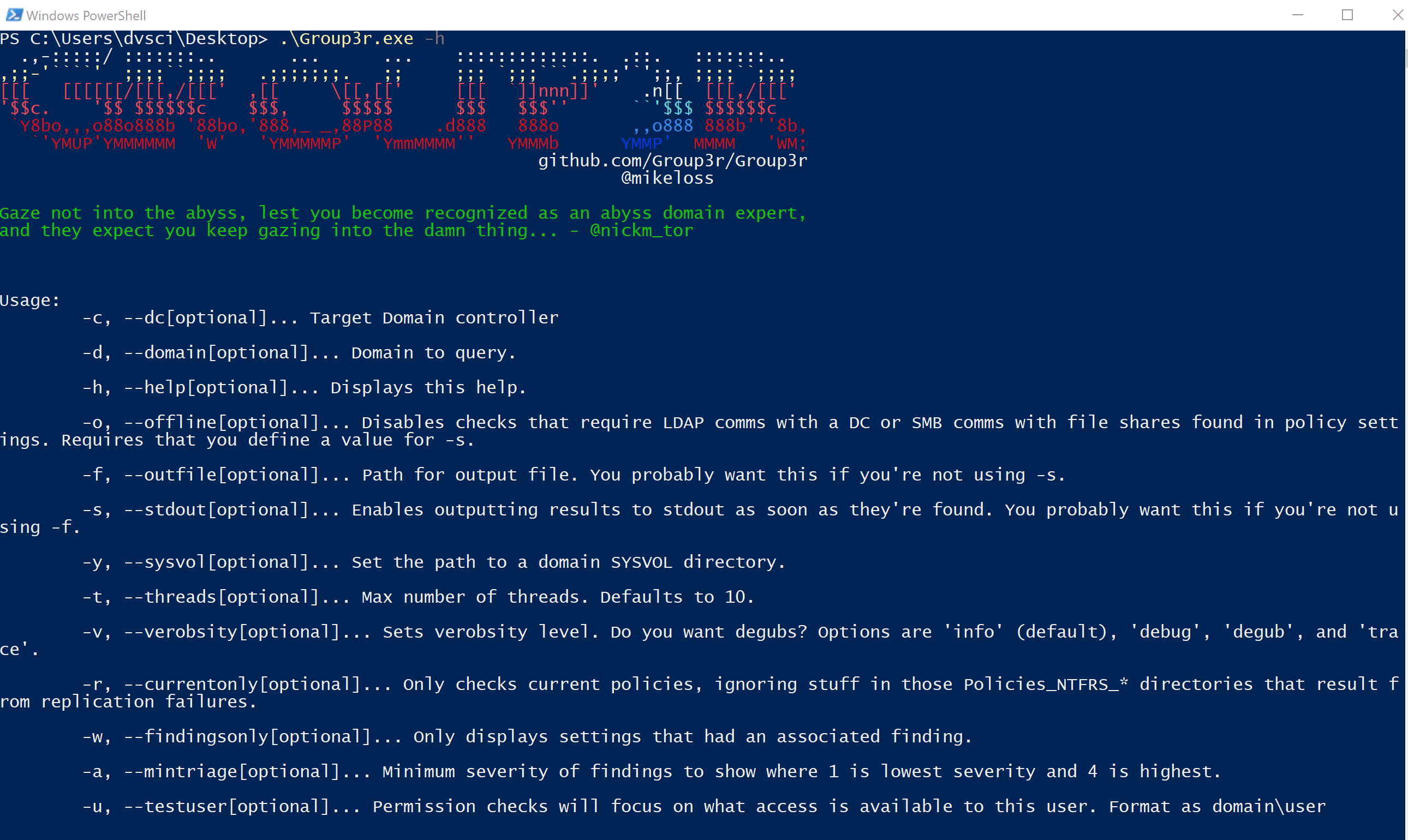
Group3r Like its ancestors, Group3r is a tool for pentesters and red teamers to rapidly enumerate relevant settings in AD Group Policy and to identify exploitable misconfigurations in the same. It does this by...
Eclipse Eclipse is a PoC that performs Activation Context hijack to load and run an arbitrary DLL in any desired process. Initially, this technique was created as a more flexible alternative to DLL Sideloading + DLL...
Cloak Cloak is a pluggable transport that works alongside traditional proxy tools like OpenVPN to evade deep-packet-inspection-based censorship. Cloak is not a standalone proxy program. Rather, it works by masquerading proxy tool’s traffic as normal...
NachoVPN NachoVPN is a Proof of Concept that demonstrates exploitation of SSL-VPN clients, using a rogue VPN server. It uses a plugin-based architecture so that support for additional SSL-VPN products can be contributed by...