Category: Ethical Hacking
nysm: A stealth post-exploitation container With the rise in popularity of offensive tools based on eBPF, going from credential stealers to rootkits hiding their own PID, a question came to our mind: Would it...
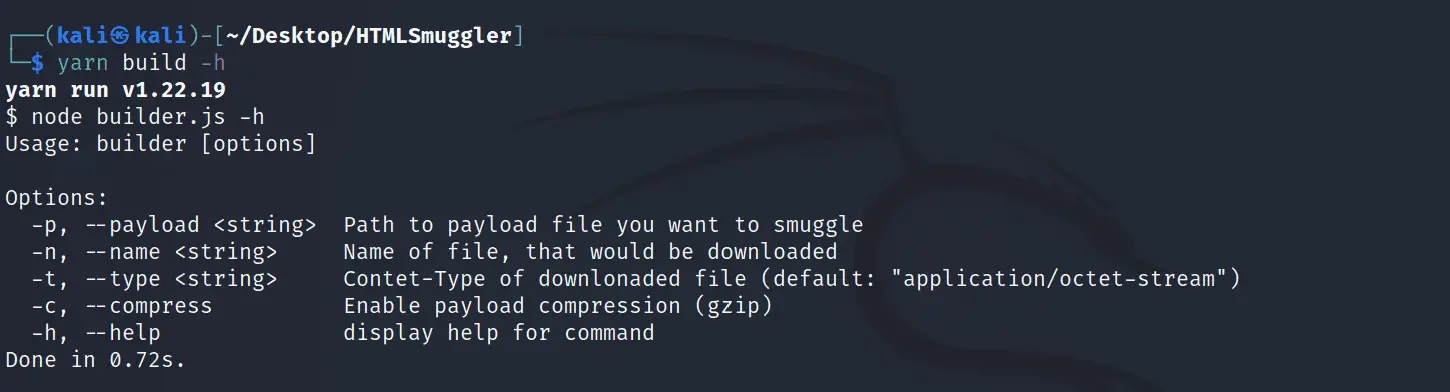
HTMLSmuggler HTMLSmuggler – JS payload generator for IDS bypass and payload delivery via HTML smuggling. The primary objective of HTML smuggling is to bypass network security controls, such as firewalls and intrusion detection systems,...
PySQLRecon PySQLRecon is a Python port of the awesome SQLRecon project by @sanjivkawa. See the commands section for a list of capabilities. Commands All of the main modules from SQLRecon have equivalent commands. Commands noted with [PRIV] require elevated...
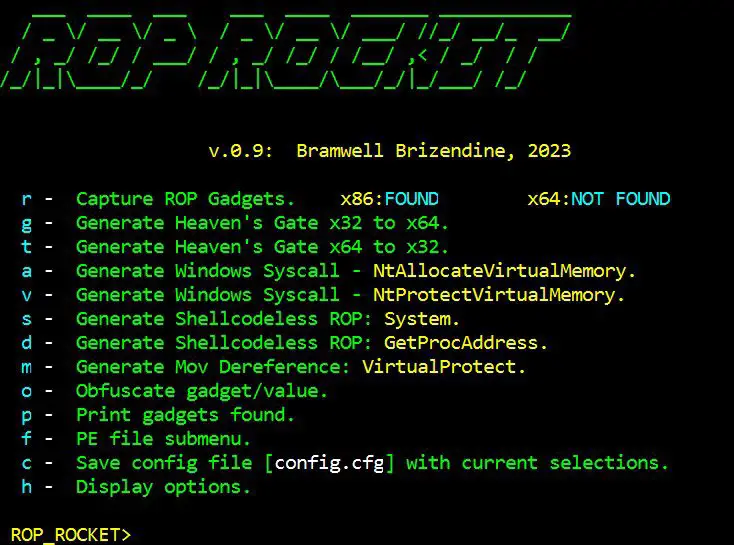
Introducing the ROP ROCKET This new, advanced ROP framework made its debut at DEF CON 31 with some unprecedented capabilities. ROCKET generates several types of chains, and it provides new patterns or techniques. Please...
go-secdump Package go-secdump is a tool built to remotely extract hashes from the SAM registry hive as well as LSA secrets and cached hashes from the SECURITY hive without any remote agent and without...
Krueger Krueger is a Proof of Concept (PoC) .NET post-exploitation tool for remotely killing Endpoint Detection and Response (EDR) as apart of lateral movement procedures. Krueger accomplishes this task by utilizing Windows Defender Application...
NufSed C2 A next-generation, Python-based Command & Control (C2) framework equipped with chaos-key encryption, dynamic port assignment, and cross-platform payload generation. NufSed C2 is designed to simplify red team operations while increasing stealth and flexibility across...
Java Archive Implant Toolkit Inject malicious payloads into JAR files. Configuration JarPlant supports injection of custom values with the implants. A set of common configuration properties are defined with the template and built-in implants....
SeamlessPass SeamlessPass is a tool designed to obtain Microsoft 365 access tokens using on-premises Active Directory Kerberos tickets for organizations with Seamless SSO (Desktop SSO) enabled. These tokens can be used for further interaction...
Hannibal Hannibal is a x64 Windows Agent written in fully position independent C (plus a tiny bit of C++). It is based off the Stardust template created by @C5pider. Use case Hannibal is intended to be...
Pytune Pytune is a post-exploitation tool for enrolling a fake device into Intune with mulitple platform support. Microsoft Intune is a cloud-based endpoint management solution designed to manage a variety of devices, including PCs...
Pentest Muse Building an AI agent that can automate parts of pentesting jobs and provide live suggestions to pentesters. Requirements Python 3.12 or later Necessary Python packages as listed in requirements.txt OpenAI API key Modes...
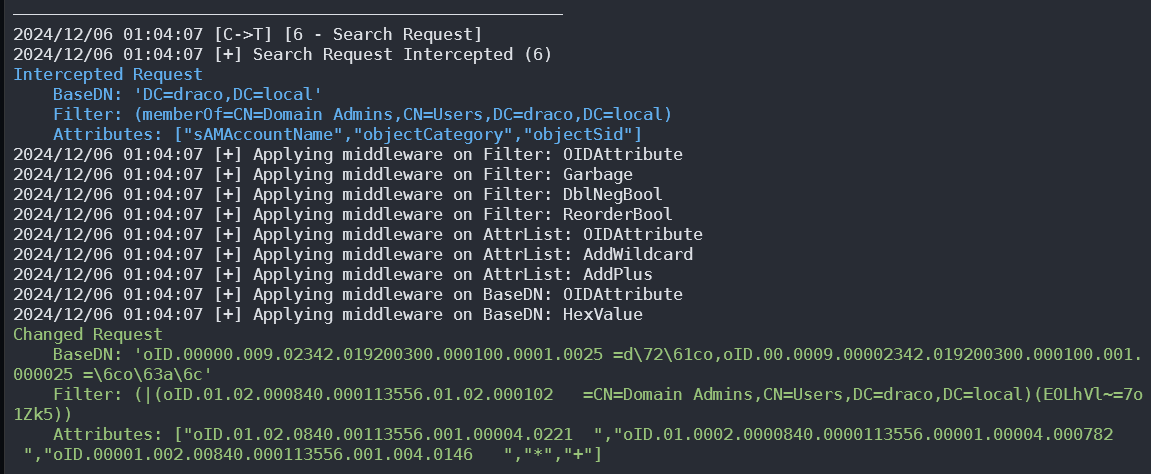
ldapx Flexible LDAP proxy that can be used to inspect & transform all LDAP packets generated by other tools on the fly. Usage Where: -f will apply Filter middlewares to all applicable requests -a will apply...
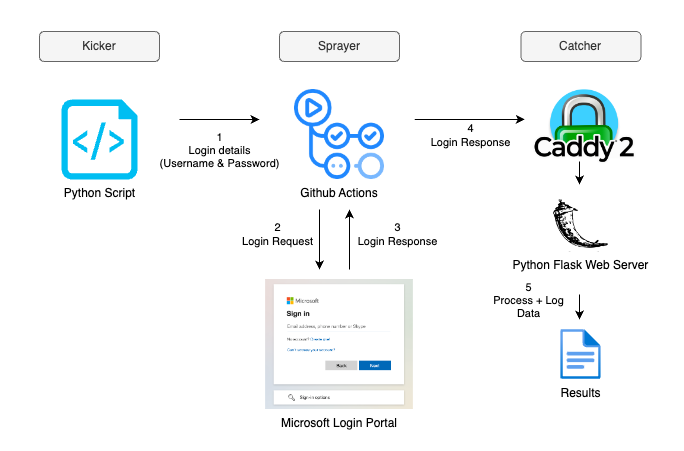
Git-Rotate Leveraging GitHub Actions for IP Rotation – for more information see the following blog post. The Sprayer and Catcher components are currently configured to target the Microsoft login portal and handle the response data. You’ll need to modify...
legba Legba is a multiprotocol credentials bruteforcer / password sprayer and enumerator built with Rust and the Tokio asynchronous runtime in order to achieve better performances and stability while consuming fewer resources than similar...
bore A modern, simple TCP tunnel in Rust that exposes local ports to a remote server, bypassing standard NAT connection firewalls. That’s all it does: no more and no less. # On your local machine...