Category: Ethical Hacking
Best EDR Of The Market (BEOTM) BestEDROfTheMarket is a naive user-mode EDR (Endpoint Detection and Response) project, designed to serve as a testing ground for understanding and bypassing EDR’s user-mode detection methods that are...
SOAPHound SOAPHound is a .NET data collector tool, which collects Active Directory data via the Active Directory Web Services (ADWS) protocol. SOAPHound is an alternative to several open-source security tools that are commonly used...
Cookie-Monster Steal browser cookies for Edge, Chrome, and Firefox through a BOF or exe! Cookie-Monster will extract the WebKit master key, locate a browser process with a handle to the Cookies and Login Data...
LOLSpoof LOLSpoof is an interactive shell program that automatically spoofs the command line arguments of the spawned process. Just call your incriminate-looking command line LOLBin (e.g. powershell -w hidden -enc ZwBlAHQALQBwAHIAbwBjAGUA….) and LOLSpoof will...
Frameless BITB A new approach to Browser In The Browser (BITB) without the use of iframes, allows the bypass of traditional framebusters implemented by login pages like Microsoft. This POC code is built for...
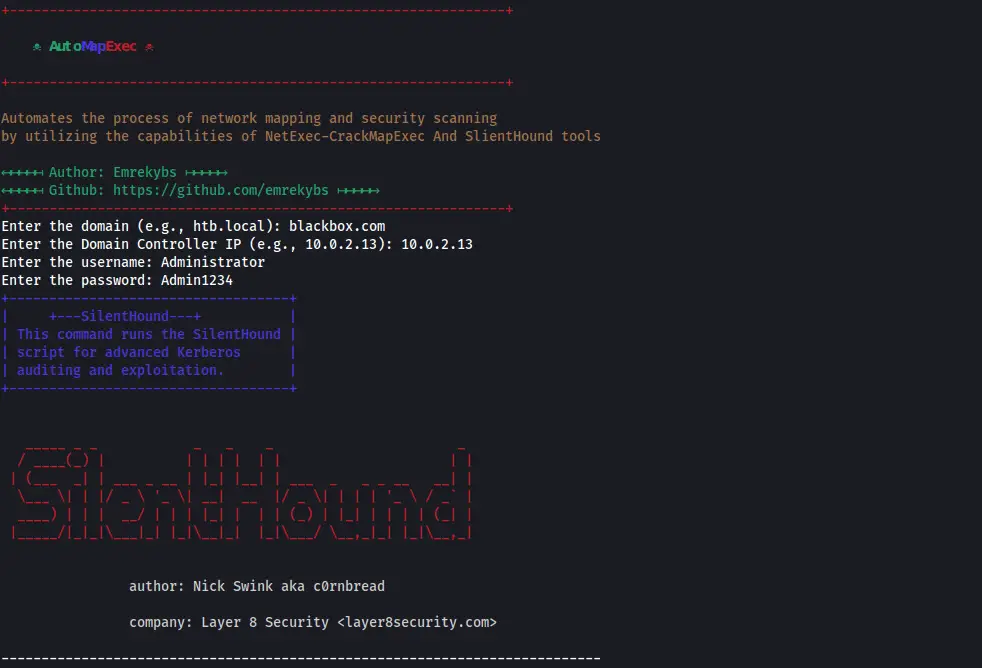
AD-AssessmentKit These tools are ideal for network administrators and cybersecurity professionals seeking to assess and enhance the security posture of AD environments and network infrastructures. AD-SecurityAudit.sh It focuses on initial reconnaissance and vulnerability identification...
DynastyPersist A CTF Tool for Linux persistence (KOTH, Battlegrounds) A powerful and versatile Linux persistence script designed for various security assessment and testing scenarios. This script provides a collection of features that demonstrate different...
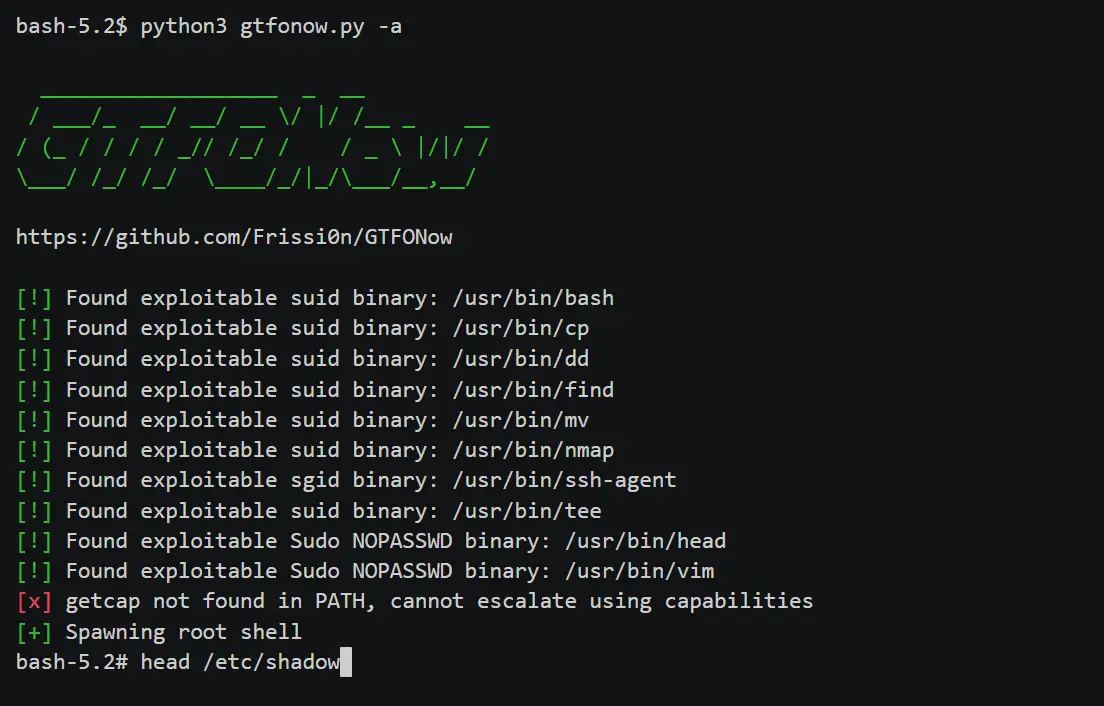
GTFONow Automatic privilege escalation on Unix systems by exploiting misconfigured setuid/setgid binaries, capabilities, and sudo permissions. Designed for CTFs but also applicable in real-world pentests. Features Automatically exploit misconfigured sudo permissions. Automatically exploit misconfigured...
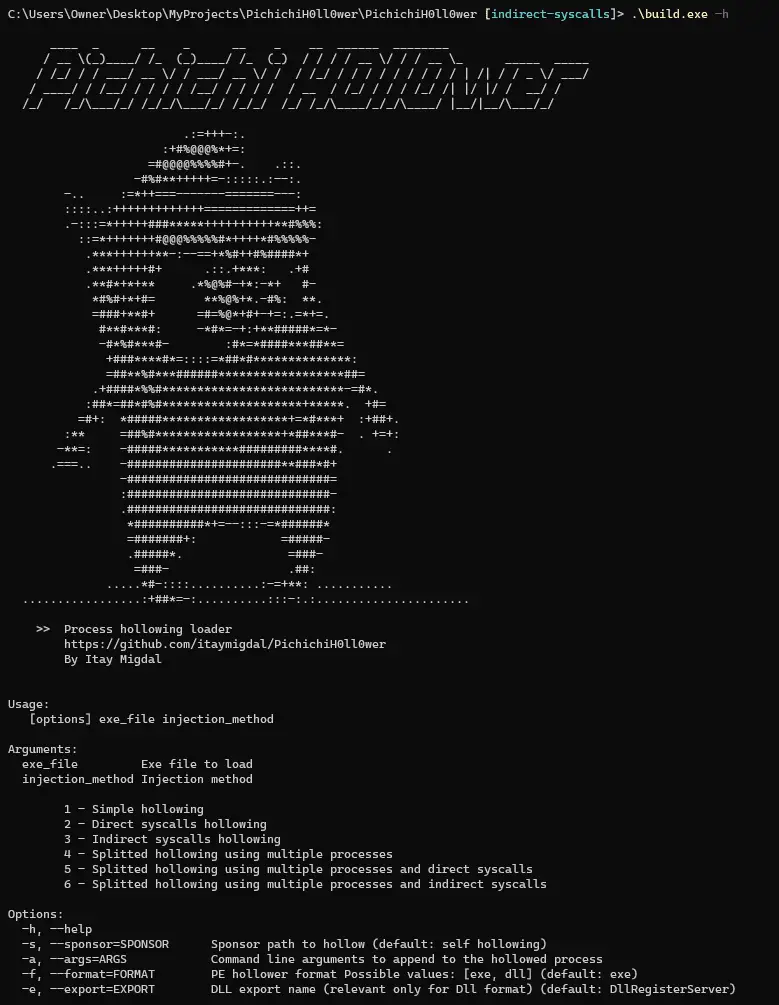
PichichiH0ll0wer Process hollowing loader written in Nim for PEs only PichichiH0ll0wer has some features to protect your payload. Features Configurable builder Payload encrypted and compressed (and optionally splitted) in the hollow loader Supports splitted...
EDRSilencer Inspired by the closed-source FireBlock tool FireBlock from MdSec NightHawk, I created my version. This tool was created to block the outbound traffic of running EDR processes using Windows Filtering Platform (WFP) APIs....
pmkidcracker This program is a tool written in Python to recover the pre-shared key of a WPA2 WiFi network without any de-authentication or requiring any clients to be on the network. It targets the...
SSH-Snake: Automated SSH-Based Network Traversal SSH-Snake is a powerful tool designed to perform automatic network traversal using SSH private keys discovered on systems, to create a comprehensive map of a network and its dependencies,...
CloudPrivs CloudPrivs is a tool that leverages the existing power of SDKs like Boto3 to brute force privileges of all cloud services to determine what privileges exist for a given set of credentials. This...
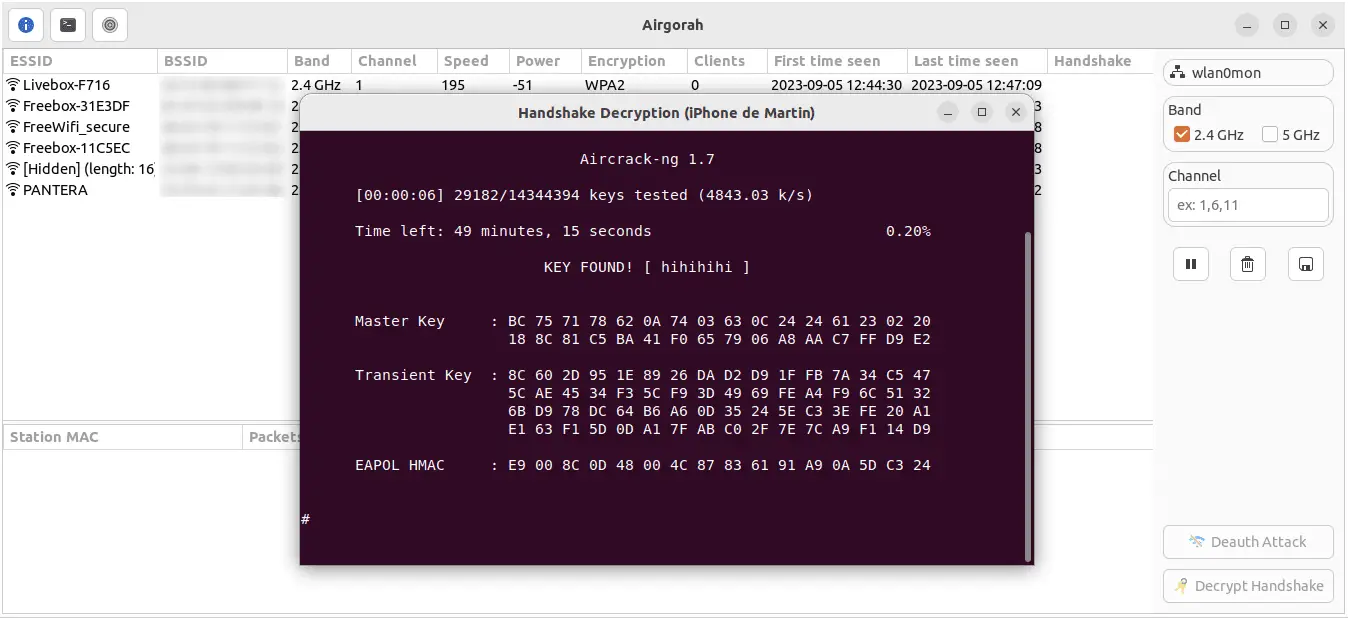
airgorah Airgorah is a WiFi auditing software that can discover the clients connected to an access point, perform deauthentication attacks against specific clients or all the clients connected to it, capture WPA handshakes, and crack...
Process Stomping A variation of ProcessOverwriting to execute shellcode on an executable’s section What is it Process Stomping, is a variation of hasherezade’s Process Overwriting and it has the advantage of writing a shellcode payload on...
Invoke-SessionHunter Retrieve and display information about active user sessions on remote computers. No admin privileges are required. The tool leverages the remote registry service to query the HKEY_USERS registry hive on the remote computers....