Hackers have successfully injected malicious code into popular npm packages by leveraging a phishing campaign against project maintainers. The attackers orchestrated a targeted campaign aimed at developers stewarding key projects and managed to steal their npm access tokens. With full control over the compromised accounts, they uploaded trojanized versions of libraries directly into the official registry—bypassing GitHub repositories entirely, leaving no trace in the form of commits or pull requests.
According to security firm Socket, the affected packages include widely used modules such as eslint-config-prettier, eslint-plugin-prettier, synckit, @pkgr/core, and napi-postinstall. These tainted versions were published under the legitimate names of the packages, potentially infiltrating the workflows of thousands of unsuspecting developers. The embedded malware was designed to execute DLL files on Windows systems, thereby enabling remote arbitrary code execution on compromised machines.
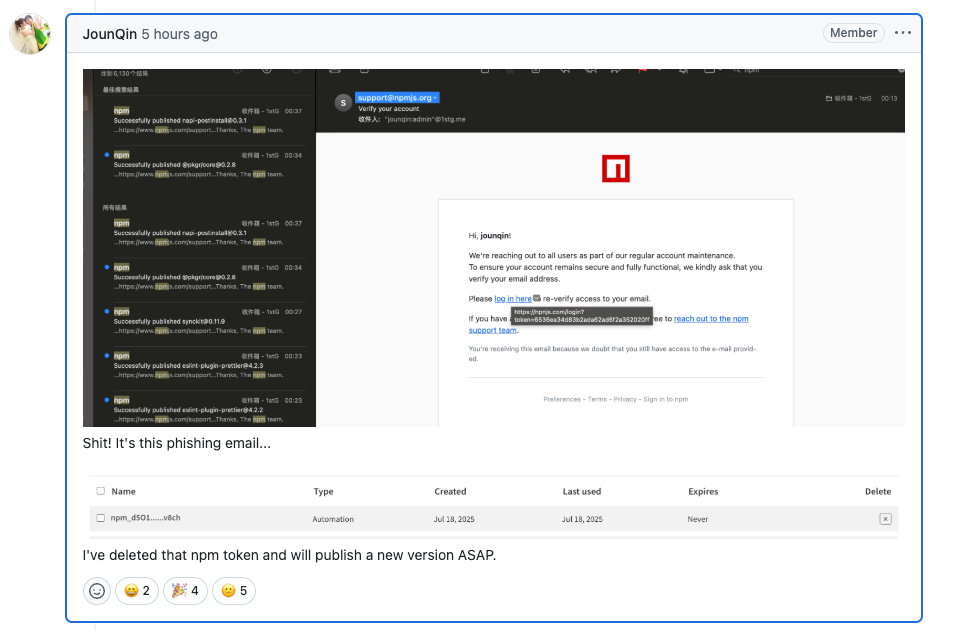
The phishing attack began with deceptive emails crafted to resemble official communication from npm. These emails urged recipients to verify their email addresses, directing them to a lookalike domain—npnjs.com—intended to mimic the legitimate npmjs.com. Victims were then lured into entering credentials on a forged login page that perfectly replicated the appearance of the real one.
Socket warns that such intrusions pose an existential threat to the broader software supply chain, as malware introduced via dependencies can propagate silently and persist undetected for extended periods. Developers are urged to immediately audit their dependencies and revert to safe versions if any of the affected modules were included. Enabling two-factor authentication and employing scoped tokens instead of conventional passwords when publishing packages is also strongly recommended.
Amid this incident, researchers uncovered a secondary wave of attacks involving 28 protest-themed packages uploaded to the npm registry. These modules were designed to disable mouse functionality on websites with Russian or Belarusian domains and play the Ukrainian national anthem in an endless loop. The malware activated only if the browser was set to Russian language preferences and the user revisited the targeted site—rendering the attack highly selective.
As noted by researcher Olivia Brown, such malicious activity can remain hidden for extended periods, deeply embedded within nested dependencies. The true impact may only surface weeks after the initial compromise.
Developers are strongly advised to purge the identified packages and conduct a comprehensive system audit to detect signs of compromise if they were previously installed.




